- Jamf Nation Community
- Community & Events
- Jamf Nation
- Re: New Ventura Payload for Crowdstrike & Full Dis...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
New Ventura Payload for Crowdstrike & Full Disk Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-28-2023 12:12 PM
Hello,
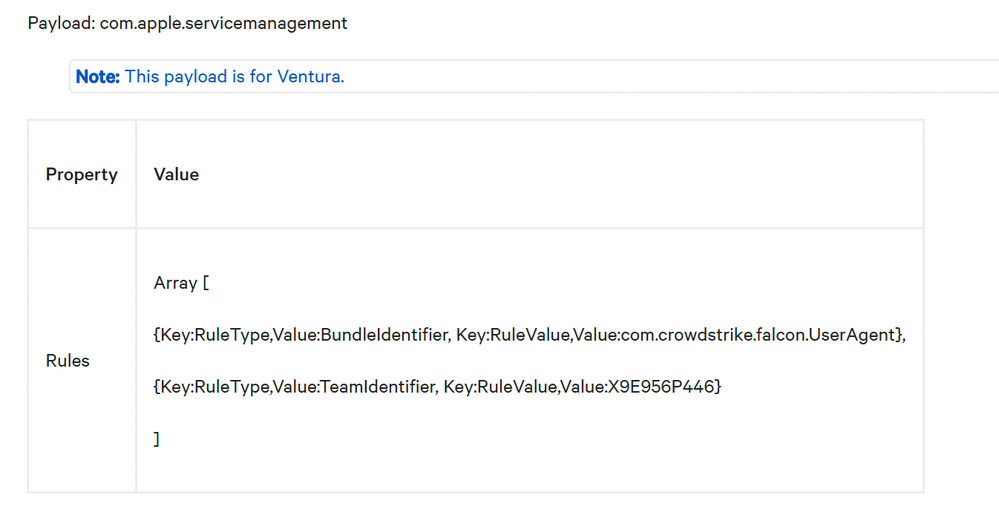
Has anyone been able to configure the Payload needed for Crowstrike to run with Ventura? (Screenshot attached it all Crowstrike's support continues to give me)
I have configured the system extensions as well as the content filter, but can't seem to figure this one out as they don't give much information. I've attempted to use PPPC-Utility as well as Apple Configurator, but they don't seem to work. As we have to go in and manually approve access. This is not ideal as it's our antivirus software and we'd like to have it up and running as soon as the device is enrolled.
I am also confused about how to enter the XML script into Jamf, that they provide to allow full disk access to Crowstrike. (Code below)
Any assistance is much appreciated. Thank you!
<dict>
<key>SystemPolicyAllFiles</key>
<array>
<dict>
<key>Allowed</key>
<true/>
<key>CodeRequirement</key>
<string>identifier "com.crowdstrike.falcon.Agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = X9E956P446</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.crowdstrike.falcon.Agent</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<false/>
</dict>
<dict>
<key>Allowed</key>
<true/>
<key>CodeRequirement</key>
<string>identifier "com.crowdstrike.falcon.App" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = X9E956P446</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.crowdstrike.falcon.App</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<false/>
</dict>
</array>
</dict>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-05-2023 12:19 PM
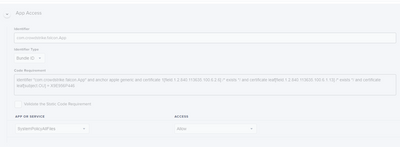
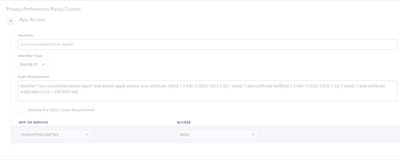
Here is what we did for the PPPC
I think the bottom thing you posted is the Managed Login Items section. This is what we did for that so end users can't disable it. Everything seems to be working with with those two things, along with system extensions, filter, and notifications configured as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2023 12:18 PM - edited 05-16-2023 12:41 PM
It's my understanding from reading the Apple Developer notes - CrowdStrike has a duplicate reference to the Team Identifier in the system extensions payload. I took out the duplicate and it worked, but be careful using the "allowed team identifier, anything with that TeamID can run" - I've seen a lot of people buzzing about how that's blocked for JAMF now. This link from Addigy does a good job of explaining how you can only have one of the three settings present.
**Side note here too - in the content filter, the only way i got it to work (green bubble) was to set the other unused filter types to "ignore" (you can do that in 10.46 finally). It seems as if an unanswered key like that leaves it as an open argument.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-16-2023 08:51 PM
I spoke too soon. Every since my update to 10.46 - my FDA is broken for new enrollments. (CrowdStrike and Rapid7 both)