- Jamf Nation Community
- Products
- Jamf Pro
- Re: How to: Firefox trusting company certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-25-2017 05:03 AM
Firefox manages certificates separated from the system certificates that are used by Safari or Chrome. To circumvent the issue that users are presented with the "certificate not trusted, add exception" notification, it is possible to add the certificates automated to the users firefox installations by utilizing the following commands: Importing Certificates on Firefox & code snippet for looking for the profile name
I know that there is also the CCK utility, but that is also more or less a pain in the a**, especially when you want to maintain firefox installations that are already existing (and have a filled user profile).
Firefox now provides the possibility to trust certificates that are stored in the system keychain by setting the key "about:config", "security.enterprise_roots.enabled" to TRUE. Mozilla Help
This setting should also be stored somewhere in prefs.js, but i have not figured out how to fiddle around with this file without ruining the user profile.
Now my question:
Does someone know a handy way to set this setting on all machines without destroying everything?
Solved! Go to Solution.
- Labels:
-
Package Building
-
Policies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2019 12:13 AM
SOLVED, but some bits needed to come together:
With Firefox 64 it is now possible to trust root certificates that are in the system certificate store
https://wiki.mozilla.org/CA/AddRootToFirefox
Also with Firefox 64 it is now possible to not only edit and distribute settings via the about:config (firefox config editor), but also by using .json files
https://support.mozilla.org/en-US/kb/customizing-firefox-using-policiesjson
AND even better, it is also possible to use configuration profiles:
"Policies can be specified using the Group Policy templates on Windows or configuration profiles on macOS (https://github.com/mozilla/policy-templates/tree/master/mac), or by creating a file called policies.json."
https://github.com/mozilla/policy-templates/blob/master/README.md
Here you can find the example plist with all currently possible keys ("IMPORTANT: This file is in active development along with the policies in Firefox. To get the policy information that corresponds to a specific release, go to https://github.com/mozilla/policy-templates/releases."
https://github.com/mozilla/policy-templates/blob/master/mac/org.mozilla.firefox.plist
--> The important part regarding certificates is:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>EnterprisePoliciesEnabled</key>
<true/>
<key>Certificates</key>
<dict>
<key>ImportEnterpriseRoots</key>
<true/>
</dict>
</dict>
</plist>You can simply edit the .plist for your needs and then upload it to the JSS (config profile - custom settings, preference domain is org.mozilla.firefox)
Just distributed this to our testing machines and it seems to work (finally!)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-06-2017 01:38 PM
I am very interested in this as well. I am having the same issues everyone else has and the old posts about CCK are not helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-08-2017 10:44 AM
watching this one also
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2019 12:13 AM
SOLVED, but some bits needed to come together:
With Firefox 64 it is now possible to trust root certificates that are in the system certificate store
https://wiki.mozilla.org/CA/AddRootToFirefox
Also with Firefox 64 it is now possible to not only edit and distribute settings via the about:config (firefox config editor), but also by using .json files
https://support.mozilla.org/en-US/kb/customizing-firefox-using-policiesjson
AND even better, it is also possible to use configuration profiles:
"Policies can be specified using the Group Policy templates on Windows or configuration profiles on macOS (https://github.com/mozilla/policy-templates/tree/master/mac), or by creating a file called policies.json."
https://github.com/mozilla/policy-templates/blob/master/README.md
Here you can find the example plist with all currently possible keys ("IMPORTANT: This file is in active development along with the policies in Firefox. To get the policy information that corresponds to a specific release, go to https://github.com/mozilla/policy-templates/releases."
https://github.com/mozilla/policy-templates/blob/master/mac/org.mozilla.firefox.plist
--> The important part regarding certificates is:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>EnterprisePoliciesEnabled</key>
<true/>
<key>Certificates</key>
<dict>
<key>ImportEnterpriseRoots</key>
<true/>
</dict>
</dict>
</plist>You can simply edit the .plist for your needs and then upload it to the JSS (config profile - custom settings, preference domain is org.mozilla.firefox)
Just distributed this to our testing machines and it seems to work (finally!)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-30-2019 09:06 AM
Does anyone know what the key pair is for browser.urlbar.autoFill I want to turn that to False.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-21-2019 12:34 PM
Thank you for this! @AndreasRumpl
@ammonsc You may have to do this with a ../default/pref <filename>.js file. Using AutoConfig or just a config.js file.
Regards,
TJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2020 01:59 PM
How would i go about adding the following to this plist?
Enable support for client certificates stored on macOS and Windows by setting the experimental preference security.osclientcerts.autoload to true.
i attempted it myself, but doesnt seem to populate into firefox about:config
the purpose of this is so that firefox works with okta device trust which requires user certs in keychain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2022 06:16 AM
Hi, @jorge_
Were you able to solve this for Okta device trust and Firefox? I have the exact same requirement and modifying the plist did not seem to work for me.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-04-2020 04:26 AM
@jorge.blandon As mentioned by AndreasRumpl just create the Plist file using the above mentioned settings and it will automatically import the Certificate from keychain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-01-2020 09:50 AM
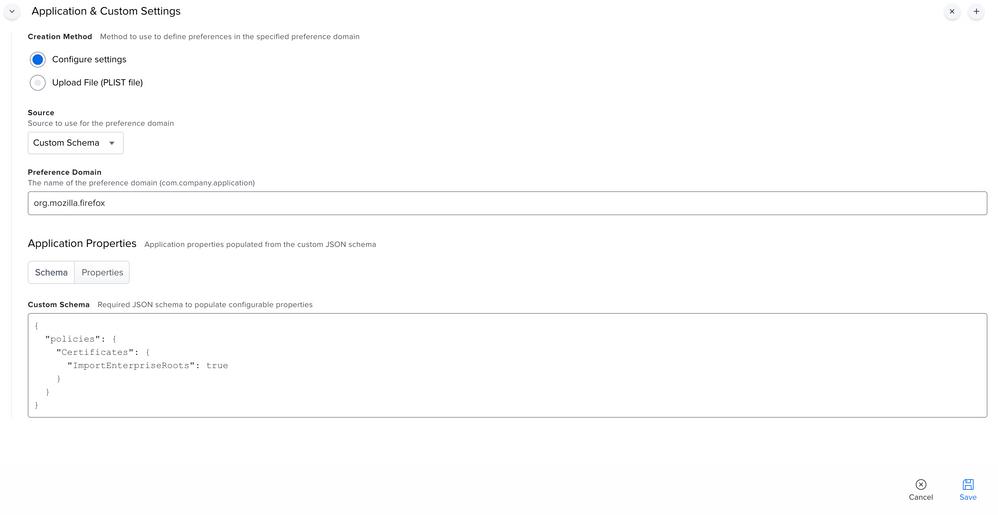
Would like to add that you can instead use the following json schema instead of uploading a plist:
{
"policies": {
"Certificates": {
"ImportEnterpriseRoots": true | false
}
}
}- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2021 12:02 PM
We are trying to get our Securly filter certificate to be trusted in firefox and am not having much luck using the json schema above. I have it deployed exactly as shown, with only the "true" value configured. Firefox just fails to verify any website certificates and when i check the about:config its obvious the security.enterprise_roots.enabled is still set to false. Any ideas? we are testing on M1 hardware with Big Sur.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2021 01:24 PM
@spowell please share the XML from your PLIST. This is working fine for me on an M1 Mac.
Do your certificates meet Apple's validity and cipher strength requirements? Validity shouldn't be an issue if you are pushing them via MDM, but cipher strength will be.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-26-2021 09:28 AM
I found a very basic error in the plist I was uploading and after correcting that the filter was working as expected in FireFox. Thanks for your response @jtrant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-09-2023 12:43 AM
Mind sharing the plist ?