- Jamf Nation Community
- Products
- Jamf Connect
- Jamf Connect Login, 802.1x Wireless, ADCS Connecto...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Jamf Connect Login, 802.1x Wireless, ADCS Connector, Unbound
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2021 05:47 PM - edited 03-30-2022 06:12 AM
Hello,
Has anyone successfully been able to connect to an 802.1x wireless network from the Jamf Connect Login screen while being unbound and using the ADCS Connector? If so, please share your Network/Certificate payloads.
Edit: After configuring this myself and helping many others with this issue, I've created a simple guide for those of you that need help below:
1. Configure one of the following:
A. ADCS Connector (expensive)
B SCEP PKI Cert (inexpensive)
2. Add the PKI Cert to your Jamf Pro Server.
3. Learn how your Radius server authenticates. (username, hostname, serial, etc)
4. Configure a Wireless configuration profile that contains the chain of trust for your radius server the ADCS/SCEP cert and trust these certs. The profile most also contain your wireless payload.
5. Deploy the profile.
How to configure ADCS: https://youtu.be/oRkpkN1Z3aI
How to configure SCEP: Integrating with DigiCert Using Jamf Pro - Integrating with DigiCert Using Jamf Pro | Jamf
Open a ticket with Jamf Support: Ask for Benjamin Julian. In my experience he is the most knowledgable about 802.1X configurations.
- Labels:
-
Jamf Connect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 09:11 AM
Our setup with AD-bound Macs was similar, and unfortunately we were not able to recreate it without being Bound, so we have machines logging in with a fixed secret account.
However, our old system had the "Use as a Login Window configuration" checked in our payload, which meant that when users logged into their domain accounts, the computer would re-authenticate to the network using their credentials (important for us as their VLAN and network access was determined based on AD groups). However, it seems that Jamf Connect ignores this setting in Jamf Pro.
If someone else has a solution for this, I'd love to hear it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-25-2021 02:25 PM
@walkerkierluk I figured out how to do this without being bound. I'm planning on creating a new discussion on how to do it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-24-2021 06:51 PM
@bwoods Do you have any insight on it? Running into this issue now. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-25-2021 08:02 AM
@user-ZPdAbvOnsK, happy to help. I guess this would be the best place to discuss. Let me know where you're having problems. Can you at least get your ADCS Connector profile to your clients?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2021 08:00 AM
Thanks bwoods, so the ADCS Connector does work, we have a machine cert rolled out based upon Serial Number (The thought was since Computer names can be changed so easily, we didn't want a bunch of certs being distributed). We use Cisco ISE that looks for machine certificates and based on certain criteria, will move the machine to the proper subnet.
We created a Network payload that includes the machine cert, along with the trusted chain certificates, and the Cisco ISE Certificate. The payload is also configured to be used with 802.1x on "Any Ethernet" and to use the machine cert for authentication. ISE never picks up the Certificate at all, and only if we create a "dummy" computer object in AD that matches the serial number of the machine, it will recognize and move the machine to the proper subnet. It sounds like it may be an ISE thing but I just want to make sure I'm not potentially missing something in the payload. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2022 02:17 PM - edited 02-07-2022 02:18 PM
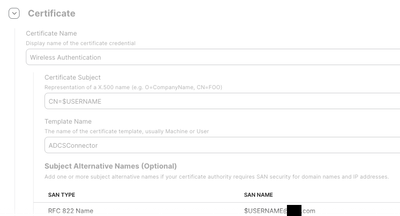
@jakeobbewe're using user based authentication in ISE. My certificate subject is CN=$USERNAME@domain.com, my SAN type is RFC R22 Name, and my SAN is $USERNAME@domain.com.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2021 08:07 AM
@user-ZPdAbvOnsK ISE first checks for the cert on the machine and then normally looks for the computer object in AD before granting access unless. ISE can be setup not to do the search but i doubt your cyber or network teams would want that
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-30-2021 10:23 AM
@user-ZPdAbvOnsK please contact me on the MacAdmins slack channel for more help. My username is brndnwds6 on there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-03-2022 10:11 AM
bwoods - Unfortunately I can't get a proper invite on the MacAdmins slack channel so can't see the "working" deployment. We are in the exact same scenario and could use your insight.
Unbound.
ADCS Connector working.
Targets Serial Number.
Once logged into the Mac - the 802.1x Immediately connects. But from Jamf Connect Login page - WiFi will not connect and only presents username/password field when everything is device based certs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2024 08:16 AM
were you able to get this figured out? I'm dealing with the same problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-29-2024 08:38 AM - edited 02-29-2024 08:40 AM
You basically need to dupe your radius server into thinking your machine cert is a user cert. In your profile change the device level to computer and use $Username as the subject. Wireless should work at the login screen after doing this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2023 06:57 AM
Hi Everyone,
I solved the 802.1x problem. You can contact me here to find out how to solve the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2023 11:19 AM
Hello @husnudagidir I would like to learn more about your solve for the 802.1x problem. Currently using Meraki Radius authentication with EAP-PEAP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2023 12:49 PM
Hi jalcantara,
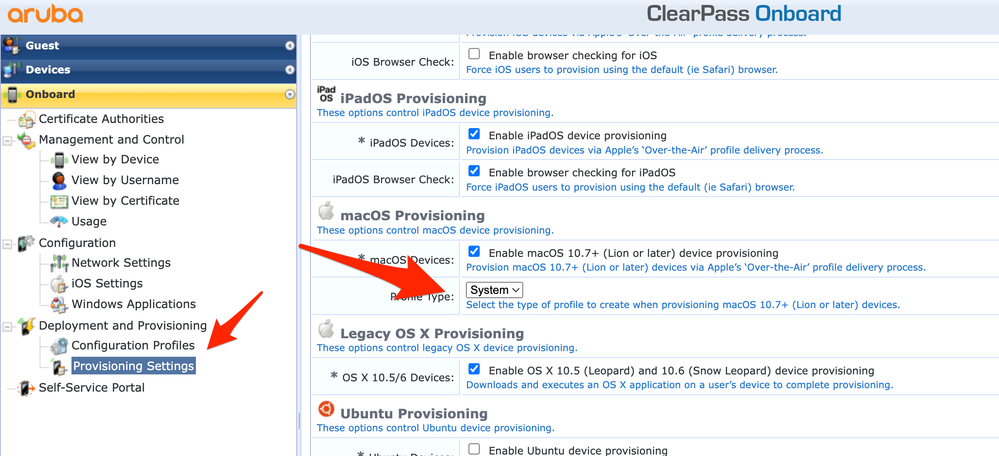
We use Aruba brand Access Points in our WIFI network. 802.1x is used to connect to the network through these products and we include users in the network by verifying with a certificate. At this stage, identity and certificate verification is done with an application called ClearPass. The ClearPass application also serves as an MDM server and SCEP server. When we connect to Access Points, the ClearPass application sends a profile file to users via a web interface. Actually the whole solution is contained in this profile file settings. We changed the part specified as "user" in the settings of this configuration profile file, sent to MacOS devices by the ClearPass application, to "system". Thus, as soon as our MacOS device was turned on, the user was able to connect to the network automatically without logging in. If the application you use is ClearPass, I can support this article with screenshots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2023 01:03 PM
Hi jalcantara,
We use Aruba brand Access Points in our WIFI network. 802.1x is used to connect to the network through these products and we include users in the network by verifying with a certificate. At this stage, identity and certificate verification is done with an application called ClearPass. The ClearPass application also serves as an MDM server and SCEP server. When we connect to Access Points, the ClearPass application sends a profile file to users via a web interface. Actually the whole solution is contained in this profile file settings. We changed the part specified as "user" in the settings of this configuration profile file, sent to MacOS devices by the ClearPass application, to "system". Thus, as soon as our MacOS device was turned on, the user was able to connect to the network automatically without logging in. If the application you use is ClearPass, I support this article with screenshots. You can use the screenshot below. After making this change, you need to delete and reinstall the WIFI profile on the macOS device. After this step, the problem disappears.