I've been over the forums and found some resources relating to this issue, but nothing definitive as of yet. So, here goes!
My current enrollment workflow (working through the slow process of changing, but this is what I have to work with):
- User sets up a new Mac and creates some local account
- Enroll via $jssurl/enroll
- Enrollment script installs base sw/configs and binds to AD
- Reboot
- User is then directed to log in using their AD credentials, go to Self Service, and enable FV2.
I'm trying to make that last step automatic as part of the enrollment script. Here's what I have so far:
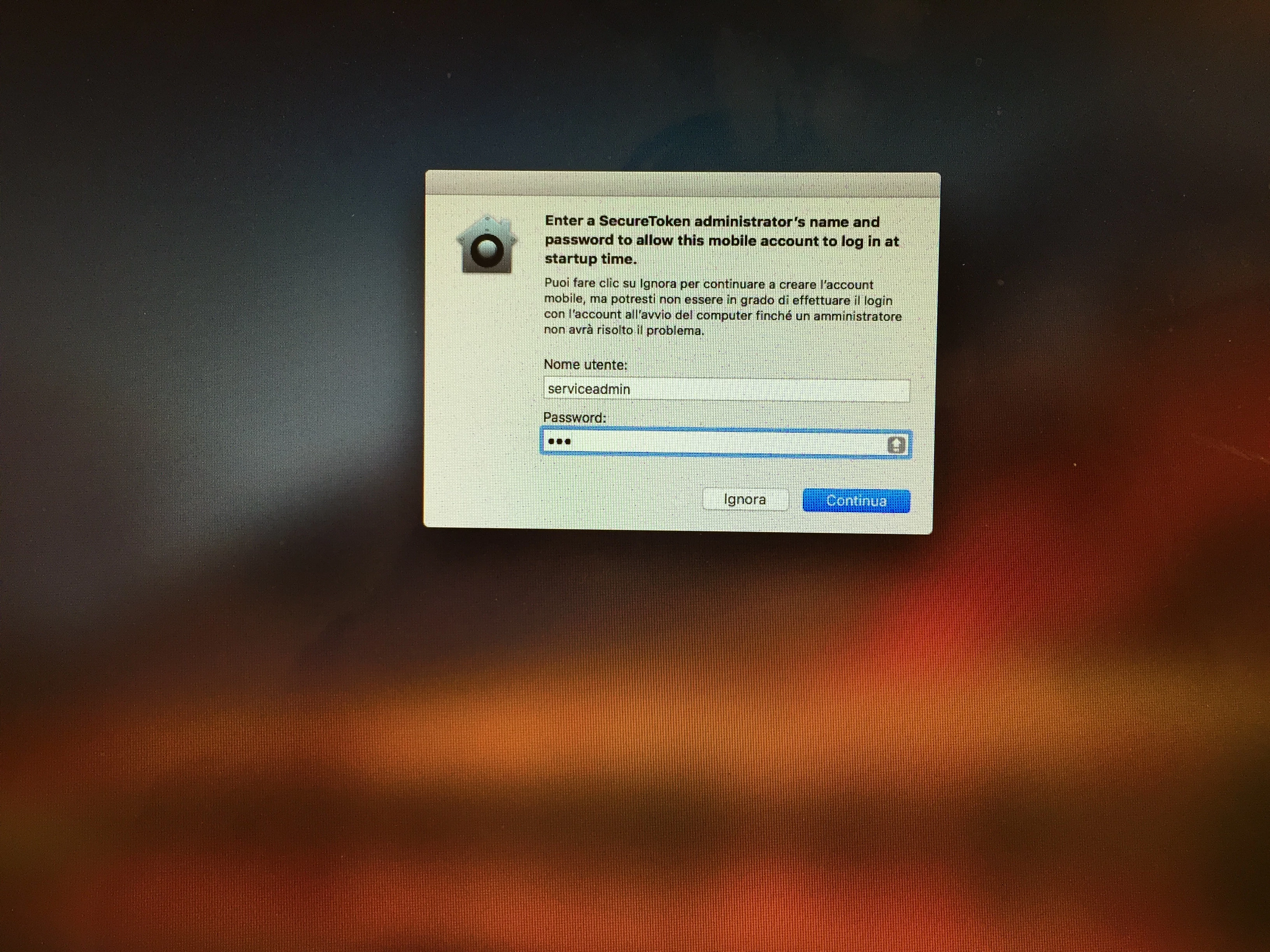
- Use createmobileaccount to make an account using their AD username
- Grant the account admin rights
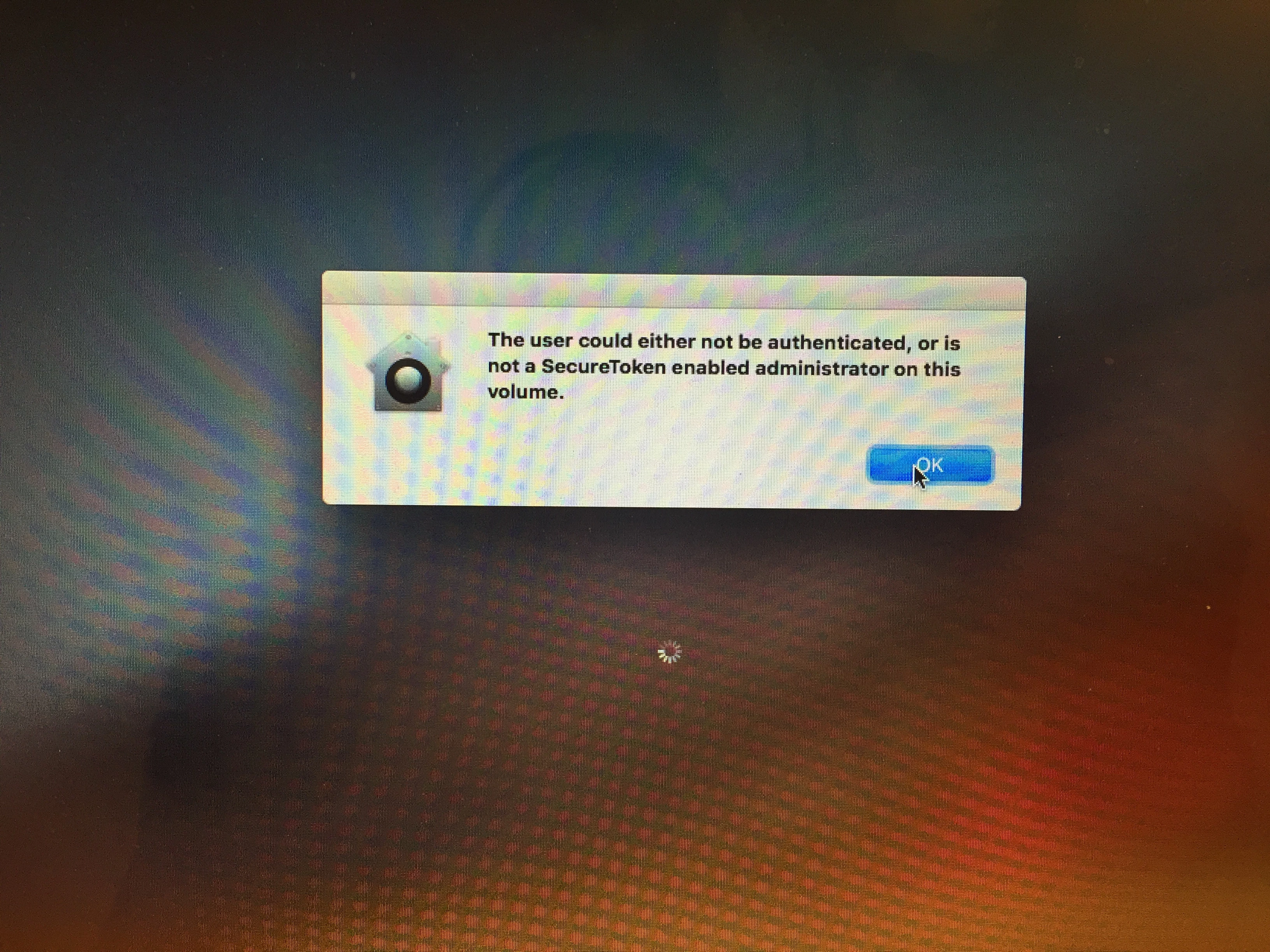
- Prompt for current and AD credentials, then use sysadminctl to grant a secure token
- Run fdesetup with deferral to enable for the AD account at next login
- Reboot
Now, fdesetup showdeferralinfo shows that enablement is pending for the AD account. sysadminctl -secureTokenStatus $ADUser shows that there is indeed a secure token for that user. However, when $ADUser logs in, they are prompted to enable FileVault (good), but FileVault is never actually enabled (not so good). Logging out and back in results in the same prompt and no encryption. The deferred enablement seems to try to kick in every login, but never succeeds.
I'm a bit puzzled here, and would appreciate any suggestions! Happy to share more info on any of the above if required.
Thanks!