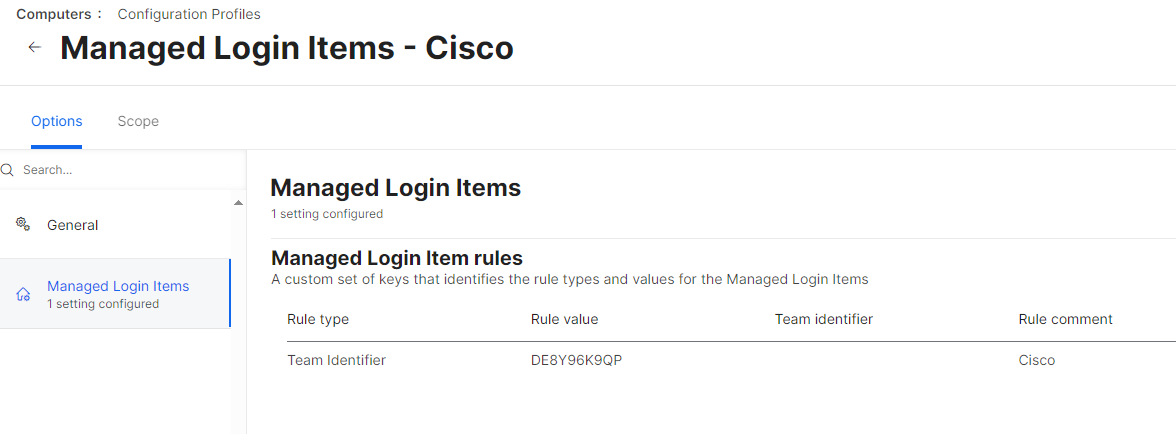
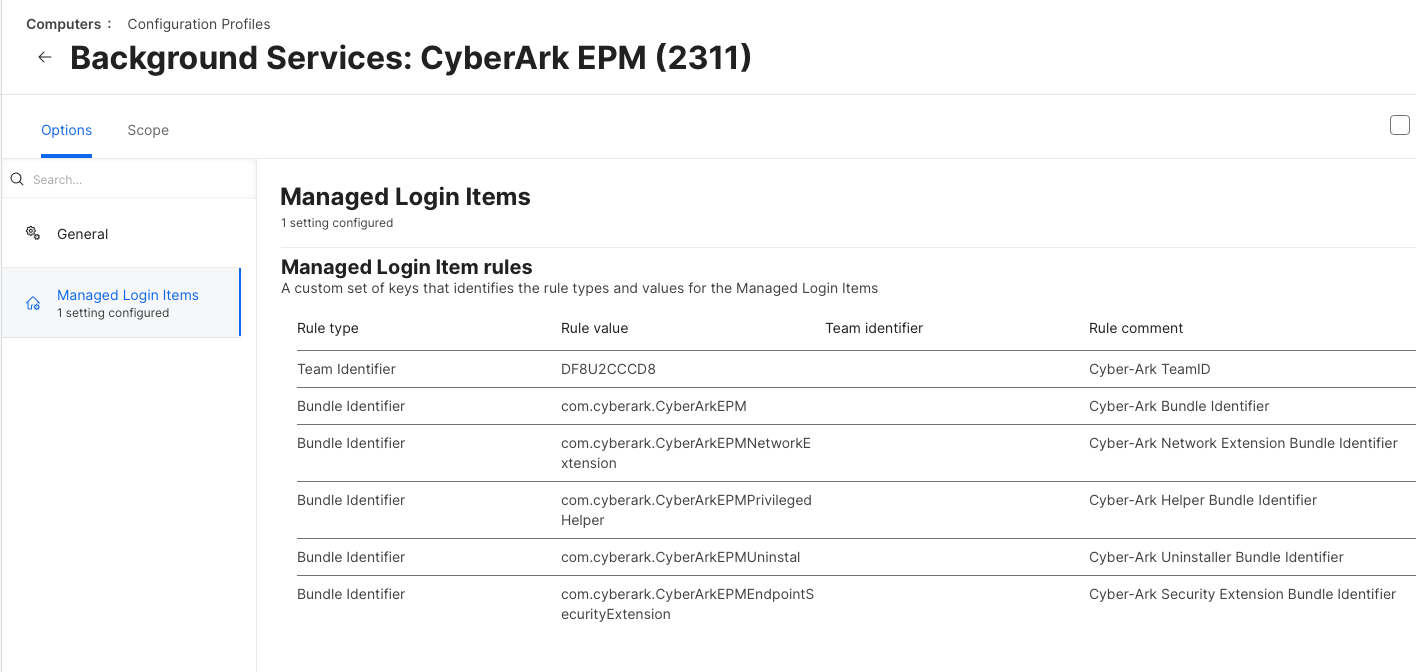
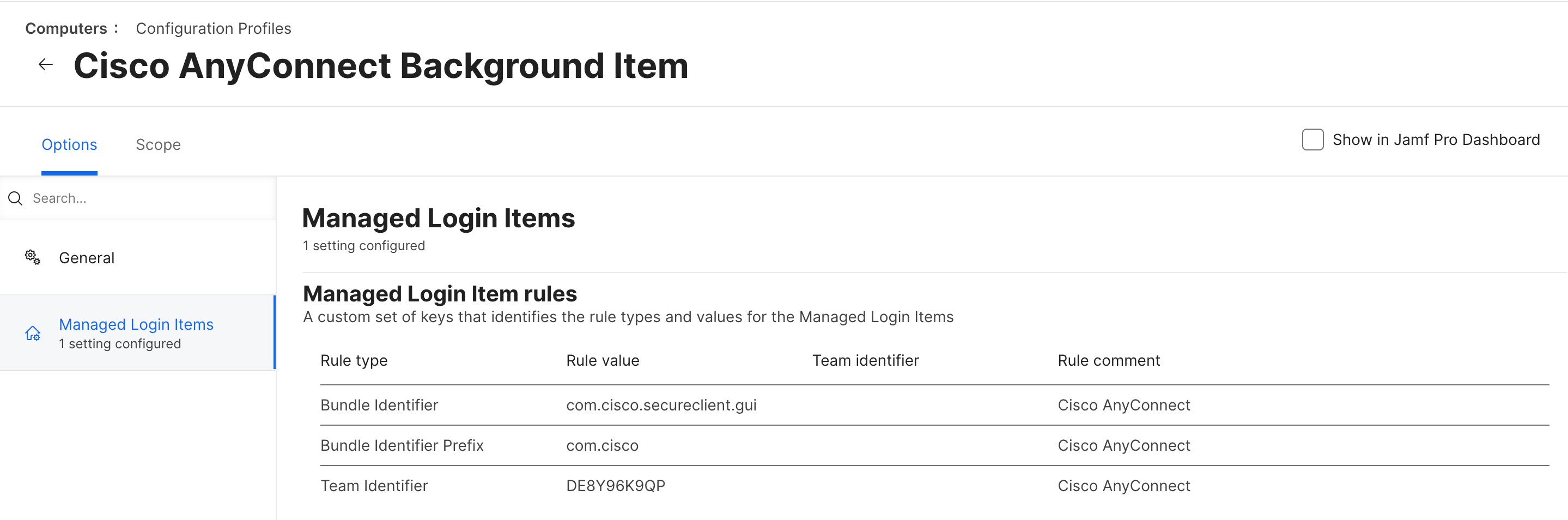
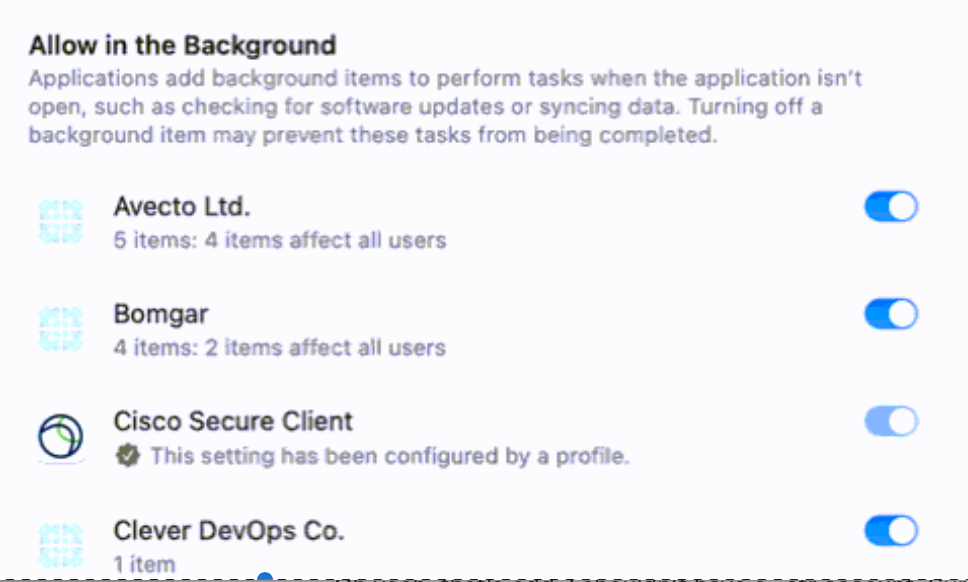
I've been down the rabbit hole of deploying Cisco's new Secure Client and I am running into an issue that I cannot find any documentation on. Some context: we only need the Umbrella Module for our school and nothing else that is loaded within Cisco's PKG. I have been successful with deploying the choice XML file, but I get the following pop-up in the installation:
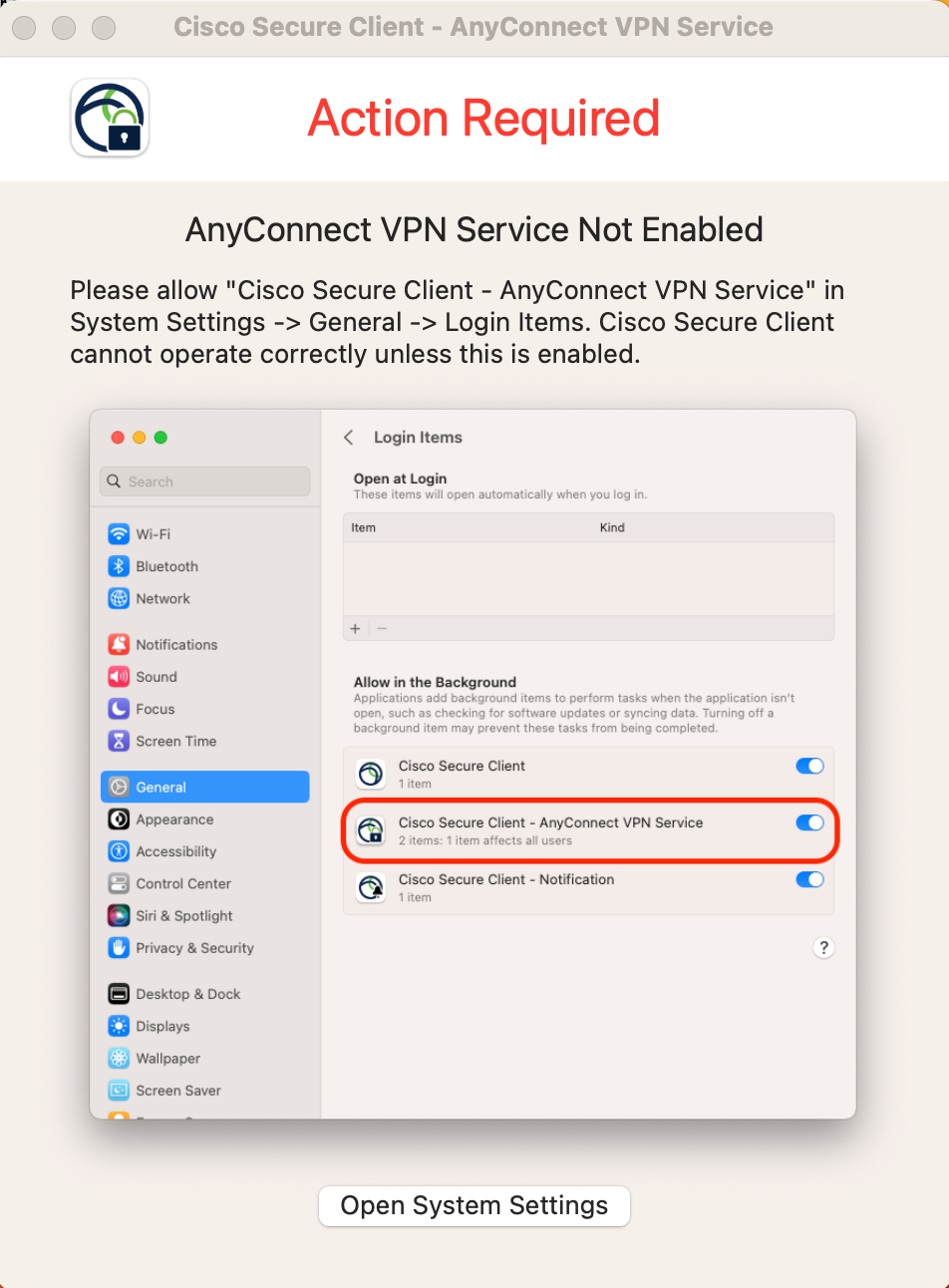
I would like this permission to be enabled within the config profile I built in jamf, but I can't seem to locate any of the info I need to do so. I already have gone through Cisco's docs and pushed out the System Extensions payload, but that seems to be just for the Cisco Secure Client itself and not this "AnyConnect VPN Service." If I manually toggle it on, the Umbrella Roaming Module will activate and work as it should, but if this is not toggled on, then the roaming stays inactive.
Any ideas? I am assuming there is something I am missing in the System Extensions payload, but I could be wrong...