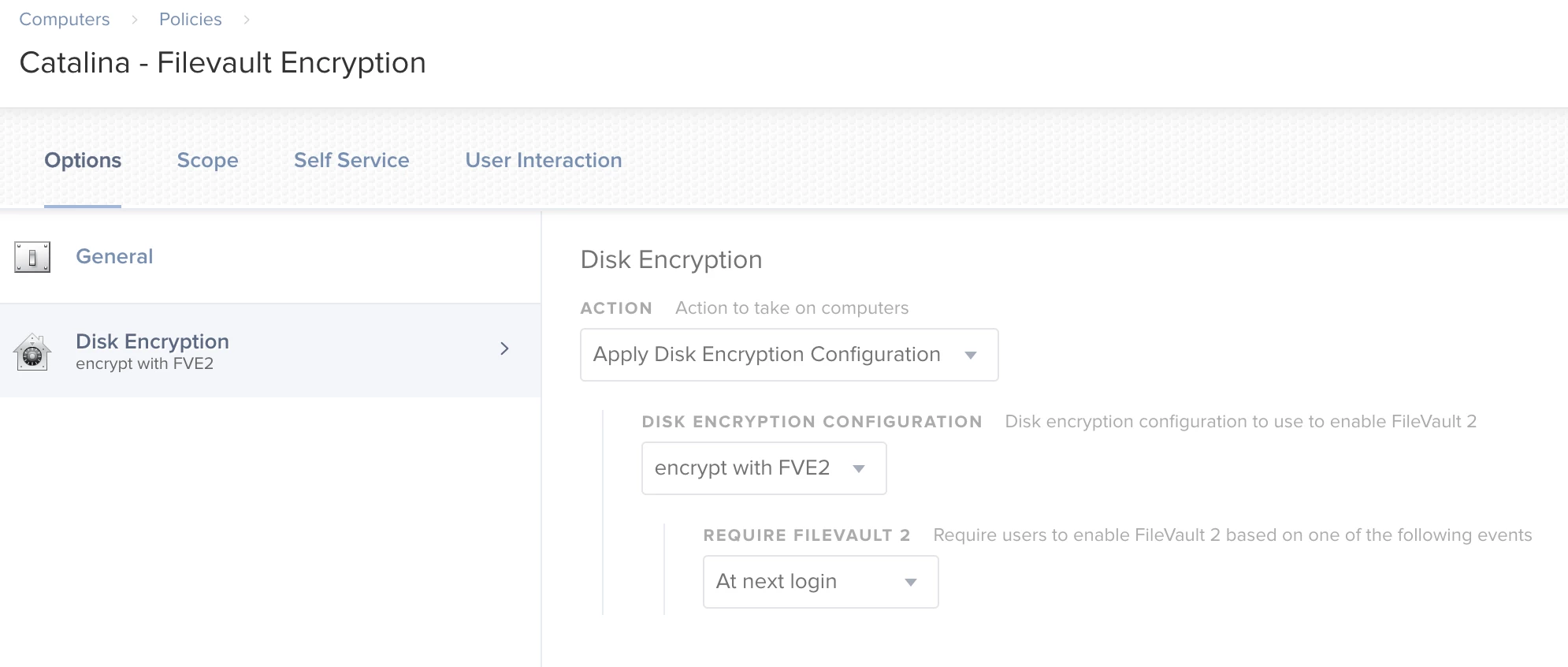
For the last year I have been using a Security and Privacy Configuration profile combined with a FV2 policy to set Filevault Encryption on new DEP Macs that I have been deploying like this-
Profile: Require FV and Escrow
Policy: Apply FV2 Individual Key at next login.
This has been working great with Mojave Macs, but with Catalina, at first login, before the deployment has even started (I'm using DEP Notify), i get a pop-up saying "fdesetup would like to enable FileVault"
The thing is, I don't know what is triggering this- the Profile is not requiring FV, and even if it was, this would only be at logout, and the policy has not even run. I have even tried removing all profiles- it still comes up. Could it be the T2 chip doing this?
Even if I click enable, FV is not enabled, and will not enable when the policy runs, or if I try and enable manually. So strange. If I roll it back to Mojave, this works perfectly.
Has anyone else come across this? It's doing my head in to be honest, and I have a load of Catalina Macs to deploy... help!
Thanks
Laurence