@franton how on earth will we ever repay you?! Apple and Jamf should shower you with Bitcoins.
Kextpocalyse 2: The Remediation

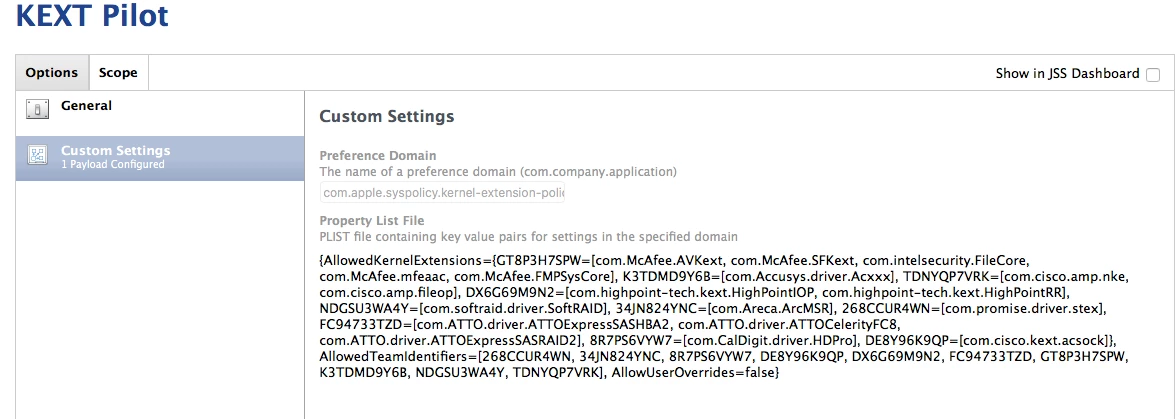
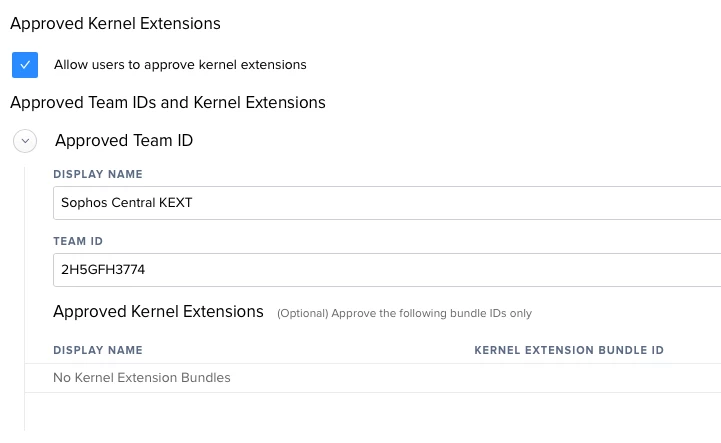
What a way to quickly/easily inventory KEXTs on a computer...whether an OOB (baseline) or one with a bunch of stuff installed (to grow list of TeamID/BundleIDs).