This sounds like an issue related to the new kext configurations required in 10.13.4. See: https://support.apple.com/en-us/HT208019
Pretty sure there's a config profile payload to approve these extensions but only if the devices are enrolled through DEP or have been "user approved"
Hi @reidg
It does sound like the new restrictions around kernel extensions (kexts) in macOS 10.13.4. You'll need to deploy a configuration profile to your Macs to approve those kexts.
There are two ways right now to find which kexts you have to allow, a script @franton developed that will list them for you or this crowd-sourced Google doc where have been listed developers. In fact I see two for Cisco AMP: https://docs.google.com/spreadsheets/d/1IWrbE8xiau4rU2mtXYji9vSPWDqb56luh0OhD5XS0AM/edit#gid=0
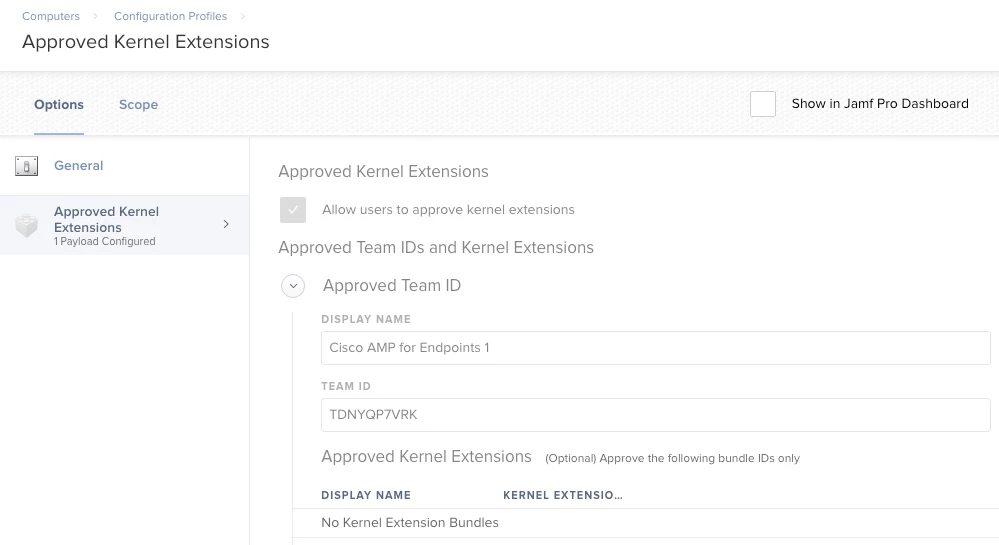
In the config profile go to Kernel Approved Extensions (it's at the bottom of the list in Jamf 10.3). If you add Cisco and that Team ID, you can then add the two kexts and their Bundle IDs to your config profile and deploy that to your Macs. After a reboot you shouldn't see that message anymore.
Here is that script:
#!/bin/bash
# Script to scan a system for kexts and gather the information needed for Apple whitelisting
# richard at richard - purves dot com
plist="com.apple.syspolicy.kernel-extension-policy.plist"
output="$HOME/Desktop"
override="false"
# Stop IFS linesplitting on spaces
OIFS=$IFS
IFS=$'
'
# Scan the drive to find 3rd party kexts
# Excluding /System /private ./StagedExtensions and /dev
echo "Searching your drive for kext files"
echo "This may take a while. Please wait ..."
echo "(please enter your password if prompted)"
paths=($( sudo find / ( -type d -name "System" -prune ) -o ( -type d -name "private" -prune ) -o ( -type d -name "StagedExtensions" -prune ) -o ( -type d -name "dev" -prune ) -o ( -name "*.kext" -type d -print ) ))
echo ""
# Report the details of all found
if [ ${#paths[@]} != "0" ];
then
for (( loop=0; loop<${#paths[@]}; loop++ ))
do
# Get the Team Identifier for the kext
teamid[$loop]=$( codesign -d -vvvv ${paths[$loop]} 2>&1 | grep "Authority=Developer ID Application:" | cut -d"(" -f2 | tr -d ")" )
# Get the CFBundleIdentifier for the kext
bundid[$loop]=$( defaults read "${paths[$loop]}"/Contents/Info.plist CFBundleIdentifier )
echo "Team ID: ${teamid[$loop]} Bundle ID: ${bundid[$loop]}"
done
fi
echo ""
# Start to generate a plist file
echo "Processing Team IDs into xml"
echo ""
if [ ${#paths[@]} != "0" ];
then
# Prune the duplicate ID's from the array
nodupes=($( echo "${teamid[@]}" | tr ' ' '
' | sort -u ))
# Now write out the xml with what we've discovered
# Header first
echo '<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>' > /private/tmp/tmp.xml
# Start with the User Override
echo "<key>AllowUserOverrides</key>
<$override/>" >> /private/tmp/tmp.xml
# Now the Team IDs
echo '<key>AllowedTeamIdentifiers</key>
<array>' >> /private/tmp/tmp.xml
for (( loop=0; loop<${#nodupes[@]}; loop++ ))
do
# Write the team identifier to the file
echo "<string>"${nodupes[$loop]}"</string>" >> /private/tmp/tmp.xml
done
# Now for the Bundle IDs with the Team IDs
echo '</array>
<key>AllowedKernelExtensions</key>
<dict>' >> /private/tmp/tmp.xml
for (( loop=0; loop<${#nodupes[@]}; loop++ ));
do
# Write the team identifier to the file
echo "<key>"${nodupes[$loop]}"</key>" >> /private/tmp/tmp.xml
echo '<array>' >> /private/tmp/tmp.xml
# Parse collected data to write out captured bundle ids that match to the team id
for (( loopint; loopint<${#teamid[@]}; loopint++ ));
do
if [ "${nodupes[$loop]}" = "${teamid[$loopint]}" ];
then
echo "<string>${bundid[$loopint]}</string>" >> /private/tmp/tmp.xml
fi
done
# Reset internal loop variable and close tags
loopint=0
echo '</array>' >> /private/tmp/tmp.xml
done
# Close up, we're done
echo '</dict>
</dict>
</plist>' >> /private/tmp/tmp.xml
fi
# Now format the file nicely and rename
cat /private/tmp/tmp.xml | xmllint -format - > "$output/$plist"
rm /private/tmp/tmp.xml
cat "$output"/"$plist"
# Reset IFS and quit
IFS=$OIFS
exit
#!/bin/sh
We are seeing this as well.
What is strange is that the WACOM software for their tablets also has a kext but it installs just fine and the tablet works.
Why does one work and not another?
To save you some time, at least for this one, the TeamID for our AMP product is TDNYQP7VRK
Thanks everyone for the feedback. Our Team ID and Bundle ID for AMP are below:
Team ID: TDNYQP7VRK Bundle ID: com.cisco.amp.fileop
Team ID: TDNYQP7VRK Bundle ID: com.cisco.amp.nke
Now we need to fast track the JAMF update to 10.3 so we can utilize that configuration profile.
We've updated to JAMF 10.3 and have had to add a few more kexts that were being blocked. The Configuration Profile for Approved Kernel Extensions works very well and deploys quickly to machines in scope during our testing.
So far, we've had to add 2 Team IDs for AMP, 2 Team IDs for VMware Fusion, and 1 for Microsoft SCEP (ESET). Below is a screenshot of the configuration profile screen for those who haven't seen it yet.