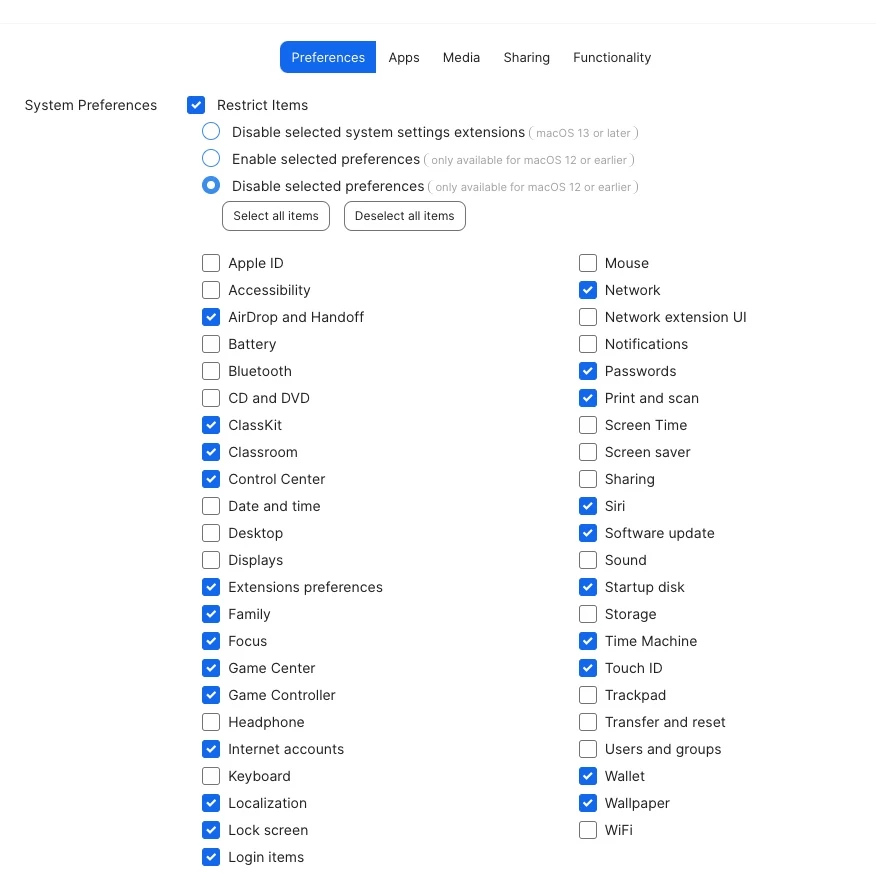
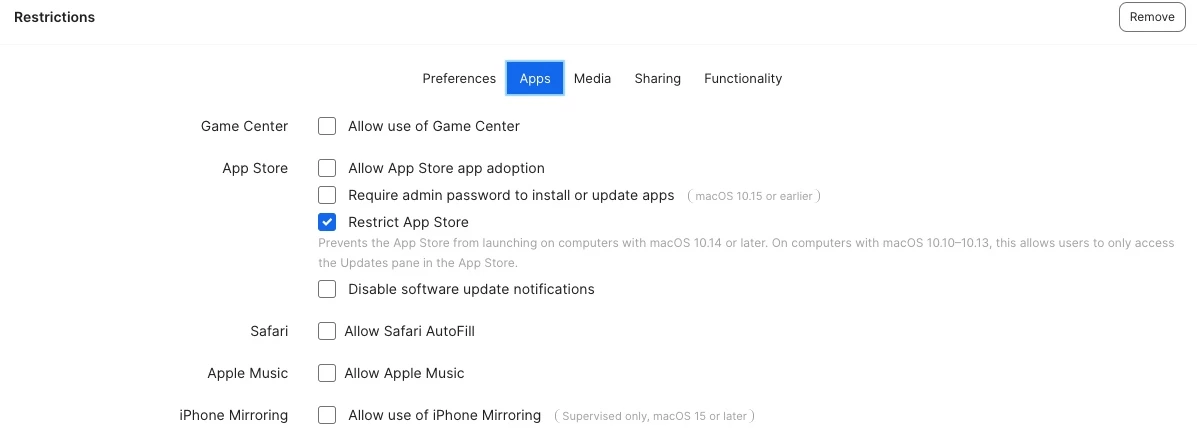
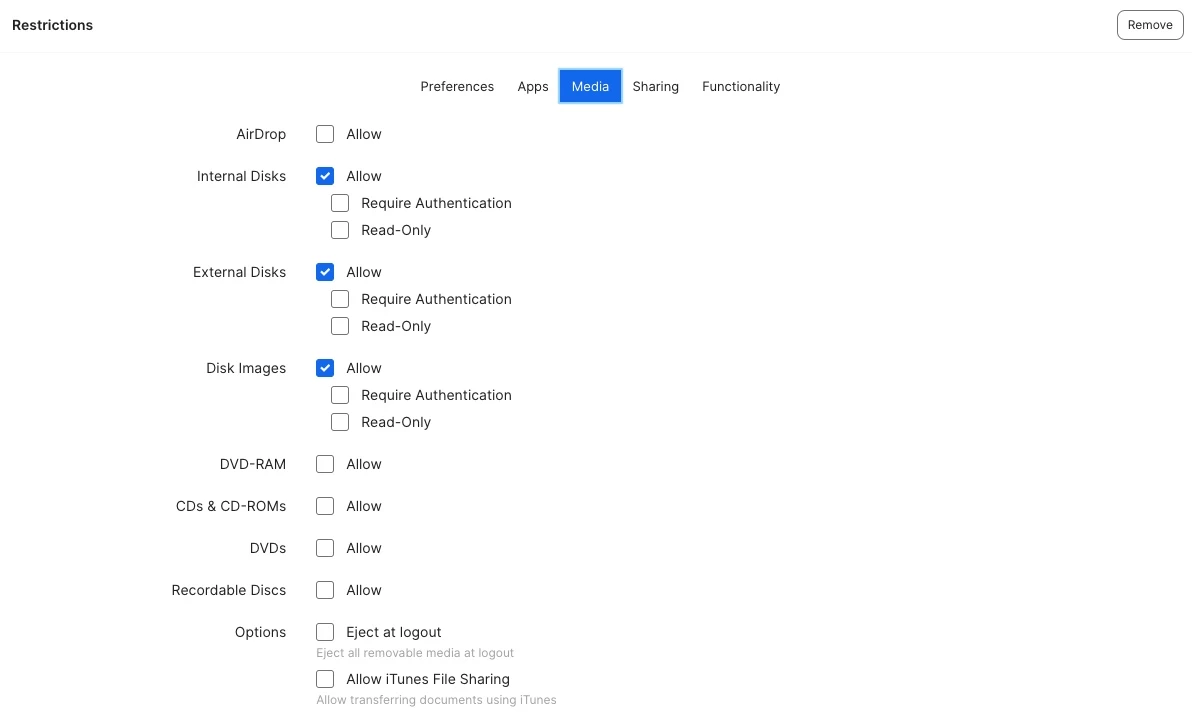
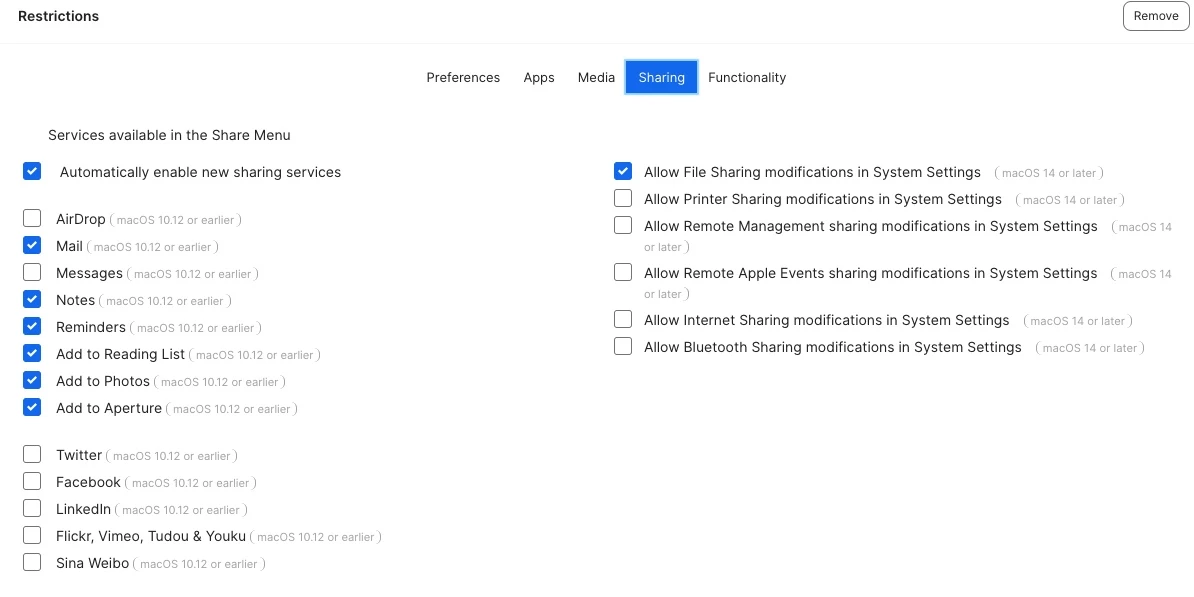
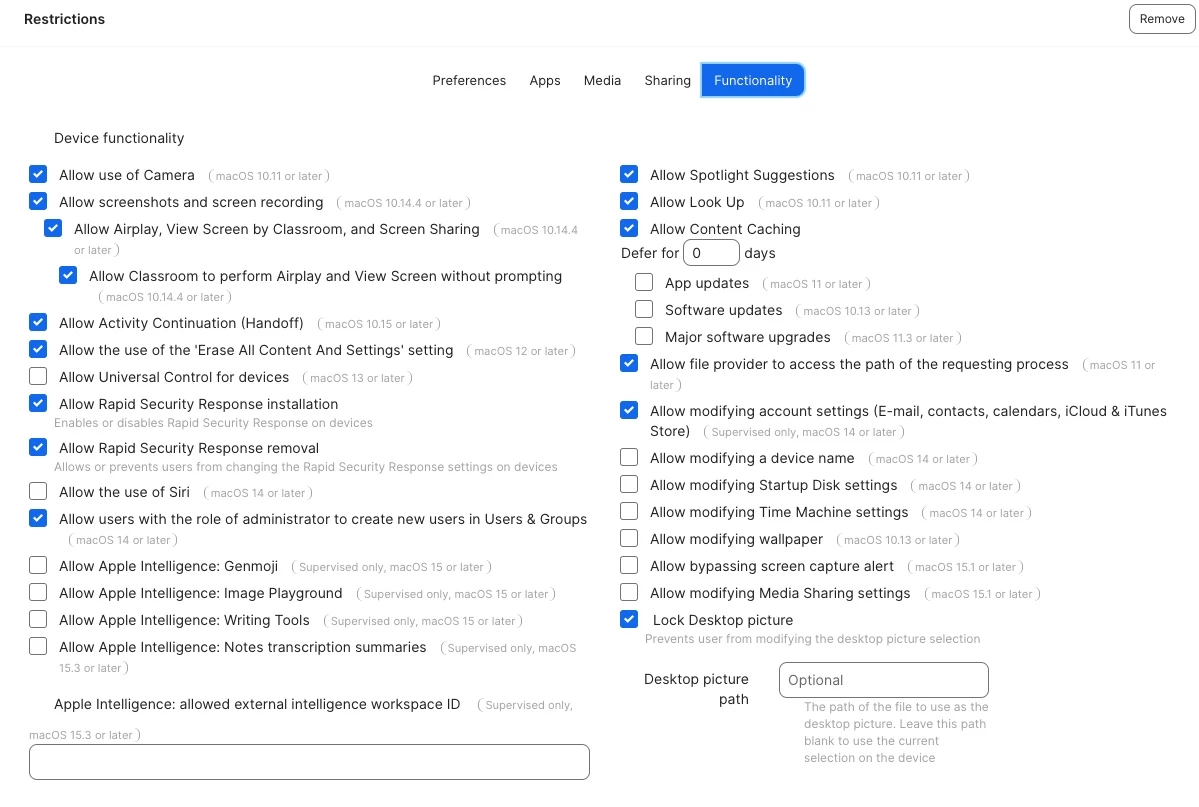
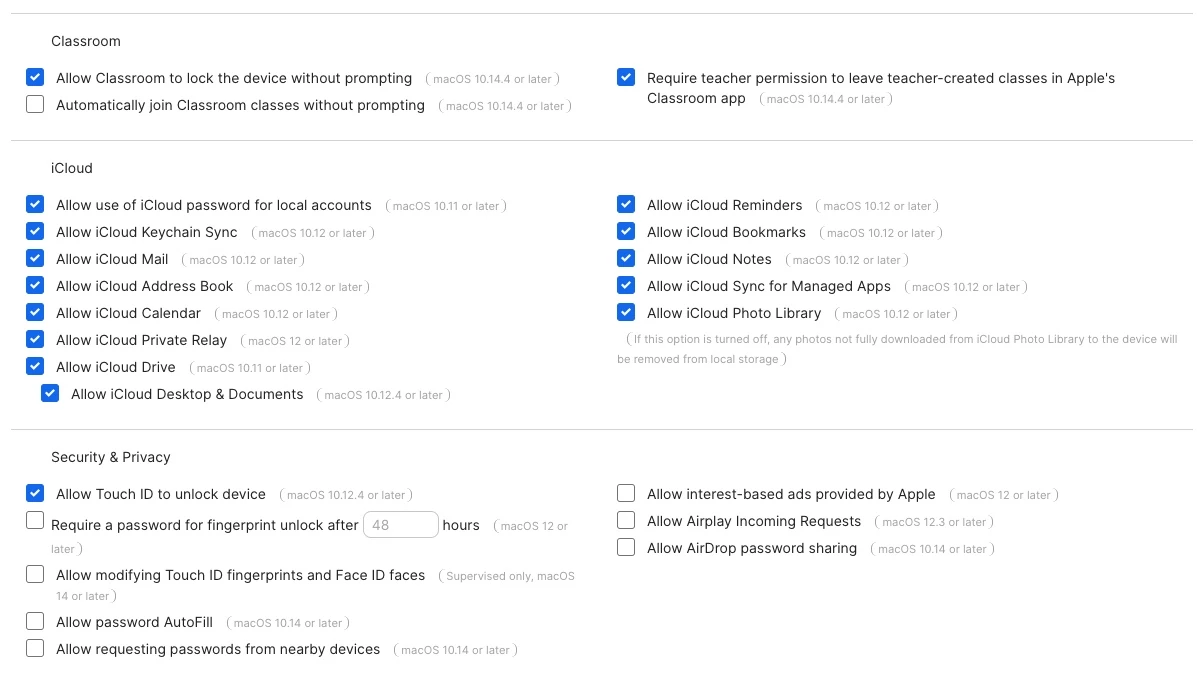
Would anyone be willing to share any profiles you've customized to restrict student devices from accessing certain areas of their MacBooks? We're hoping to see if there's anything specific we should be blocking and to hopefully make improvements to our management approach.
Backstory:
The school did not have profiles in place, which allowed students unrestricted access to their devices for years. A few months ago, I implemented a profile with restrictions, and it has helped prevent students from altering several settings. However, we are still in the early stages (still learning Jamf) and are allowing access to certain features, such as:
- Downloading Apps from anywhere (music department has an app that won't download if we restrict this to Apple and trusted developers) - potential workaround is to package the app and deploy via Jamf as an in-house app and then restrict app downloads again at the end of the school year.
- Allowing all iCloud settings for managed Apple ID access (our Ed Tech is pushing for more collaborative work with Apple Apps and Cloud access). Issue: The students sometimes log in to their personal Apple IDs and don't log out when we collect the devices, so we're spending an extra few seconds resetting the device if it's a non-returning student.
I would love to hear any ideas and methods others have implemented regarding restrictions at your school. I've attached some photos of the profile we are currently working to deploy with additional restrictions. Any advice is greatly appreciated!