Hey,
Our agent for macos requires spficif bluetooth permissions to function properly. For most other MDMs we enable this by sending a mobile config containing BluetoothAlways key in Services, as documented here.
JAMF seems to remove this key from mobileconfigs uploaded through UI and also directly through API.
Example section that needs to be included in the mobileconfig:
<key>Services</key>
<dict>
<key>BluetoothAlways</key>
<array>
<dict>
<key>Allowed</key>
<integer>1</integer>
<key>CodeRequirement</key>
<string>anchor apple generic and identifier "com.sentinelone.sentinel-helper" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "4AYE5J54KN")</string>
<key>Identifier</key>
<string>com.sentinelone.sentinel-helper</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<integer>0</integer>
</dict>
</array>
</dict
How the mobileconfig pushed to endpoint actually looks like:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>75311209-1d90-478e-bcb5-c443d8729f7c</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string> Sentinel Labs, Inc.</string>
<key>PayloadIdentifier</key>
<string>75311209-1d90-478e-bcb5-c443d8729f7c</string>
<key>PayloadDisplayName</key>
<string>SentinelOne_Privacy_Control_Permanent</string>
<key>PayloadDescription</key>
<string>SentinelOne registration token profile</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadUUID</key>
<string>7e990303-38f8-4c08-8b03-12d9ab6c3cdf</string>
<key>PayloadType</key>
<string>com.apple.TCC.configuration-profile-policy</string>
<key>PayloadOrganization</key>
<string>Sentinel Labs, Inc.</string>
<key>PayloadIdentifier</key>
<string>7e990303-38f8-4c08-8b03-12d9ab6c3cdf</string>
<key>PayloadDisplayName</key>
<string>Bluetooth permissions always granted</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
</dict>
</array>
</dict>
</plist>
This results in the configuration either
- Failing, as the pushed config is invalid (ignore the UUIDs; different attemps)
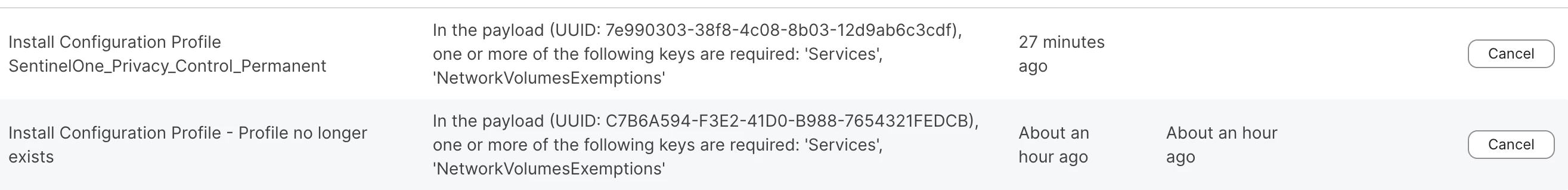
- Finishing, but missing the required part of the payload, meaning that the agent is misconfigured


