I'm pretty sure I know the answer, but can't find the statement in any documentation. Is it possible to pull attributes when you have Cloud Identity Provider enabled for Azure in via extension attributes? If so, what attributes are available?
Yes, you can pull extended attributes from Azure AD into an Extension Attribute. I used the Microsoft Graph Explorer to find a weird attribute (proxyAddresses), one that I knew would not be in Jamf Pro, put it into an Extension Attribute and the info was pulled back.
Yes, you can pull extended attributes from Azure AD into an Extension Attribute. I used the Microsoft Graph Explorer to find a weird attribute (proxyAddresses), one that I knew would not be in Jamf Pro, put it into an Extension Attribute and the info was pulled back.
Do you have Azure setup under LDAP servers or Cloud Identity Provider?
CIP... I have no LDAP servers configured in the server I was testing with.
CIP... I have no LDAP servers configured in the server I was testing with.
Interesting....mine won't pull anything in.....
Are you verifying the attribute you are pulling from has data via the Microsoft Graph Explorer first? And then I have to ask it, you are updating inventory on the device, right? ;-)
Are you verifying the attribute you are pulling from has data via the Microsoft Graph Explorer first? And then I have to ask it, you are updating inventory on the device, right? ;-)
yes and yes! I noticed using the graph explorer, if you use v1 there is very limited info. If I switch to Beta i get a lot more data (including the proxyAddresses which is not returned on v1).
The only other thing I can think is that you still have an LDAP server configured. I believe that an LDAP server takes precedence over CIP. I had my Okta dev account configured under LDAP and when I tried to pull info it would pull from Okta and not Azure. So I deleted the Okta LDAP setup and CIP took over.
Worst case, you can open a support ticket and they should be able to assist.
The only other thing I can think is that you still have an LDAP server configured. I believe that an LDAP server takes precedence over CIP. I had my Okta dev account configured under LDAP and when I tried to pull info it would pull from Okta and not Azure. So I deleted the Okta LDAP setup and CIP took over.
Worst case, you can open a support ticket and they should be able to assist.
Figured it out. I had a bad EA asking for something that wasn't permitted. Removed that EA and now I'm getting data!!
Yes, you can pull extended attributes from Azure AD into an Extension Attribute. I used the Microsoft Graph Explorer to find a weird attribute (proxyAddresses), one that I knew would not be in Jamf Pro, put it into an Extension Attribute and the info was pulled back.
Hi there, i have been looking into the same thing. Total newbie here.
How do you achieve calling Graph from JAMF to populate the data? Is it an API call? I am a bit lost...
When i look into my JAMF instance in the "Extension Attributes" there is nothing that mentions my iDP. Jamf training also mentions LDAP but we are not connecting any of that as we are going cloud first.
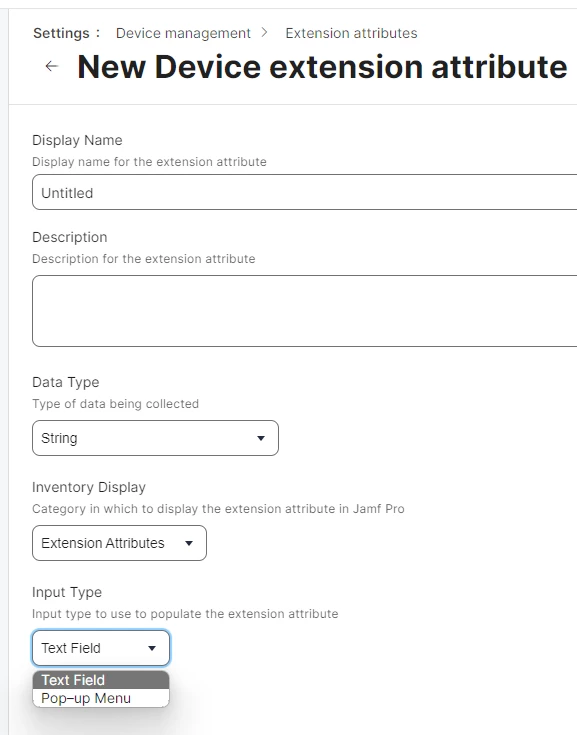
Any idea where i need to look or what i have to read to understand what i should do to pull the data from Azure ?
Thanks
Hi there, i have been looking into the same thing. Total newbie here.
How do you achieve calling Graph from JAMF to populate the data? Is it an API call? I am a bit lost...
When i look into my JAMF instance in the "Extension Attributes" there is nothing that mentions my iDP. Jamf training also mentions LDAP but we are not connecting any of that as we are going cloud first.

Any idea where i need to look or what i have to read to understand what i should do to pull the data from Azure ?
Thanks
Apologies this is the right screenshot
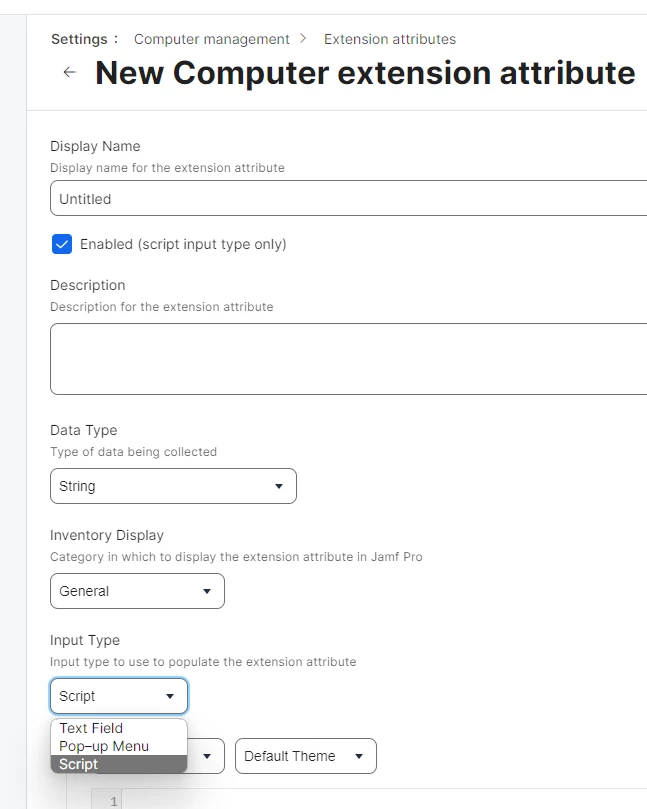
Apologies this is the right screenshot

As long as you have a Cloud Identity Provider configured under Settings -> System -> Cloud Identity Providers, you should have the option to pull from Directory Service.
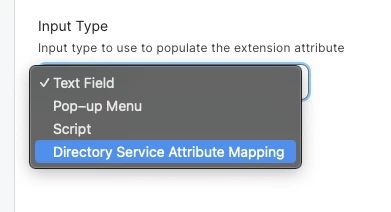
I have nothing configured under LDAP Servers. I only have entries under Cloud Identity Providers.
As long as you have a Cloud Identity Provider configured under Settings -> System -> Cloud Identity Providers, you should have the option to pull from Directory Service.

I have nothing configured under LDAP Servers. I only have entries under Cloud Identity Providers.
And my mention of Microsoft Graph was simply as a way to determine what attribute to pull out of Entra ID.
As long as you have a Cloud Identity Provider configured under Settings -> System -> Cloud Identity Providers, you should have the option to pull from Directory Service.

I have nothing configured under LDAP Servers. I only have entries under Cloud Identity Providers.
Thanks
interesting... I have not got the option. I have Azure Configured and test returns results without issue. Might be a JAMF quirk?
Thanks
interesting... I have not got the option. I have Azure Configured and test returns results without issue. Might be a JAMF quirk?
Under Settings -> Computer Management -> Inventory Collection, make sure you have "Collect user and location information from Directory Service" checked.
I just spun up a fresh instance, added Cloud Identity Provider connected to my Entra ID instance, and checked that box and I get the Directory Service Attribute Mapping option in Extension Attributes.
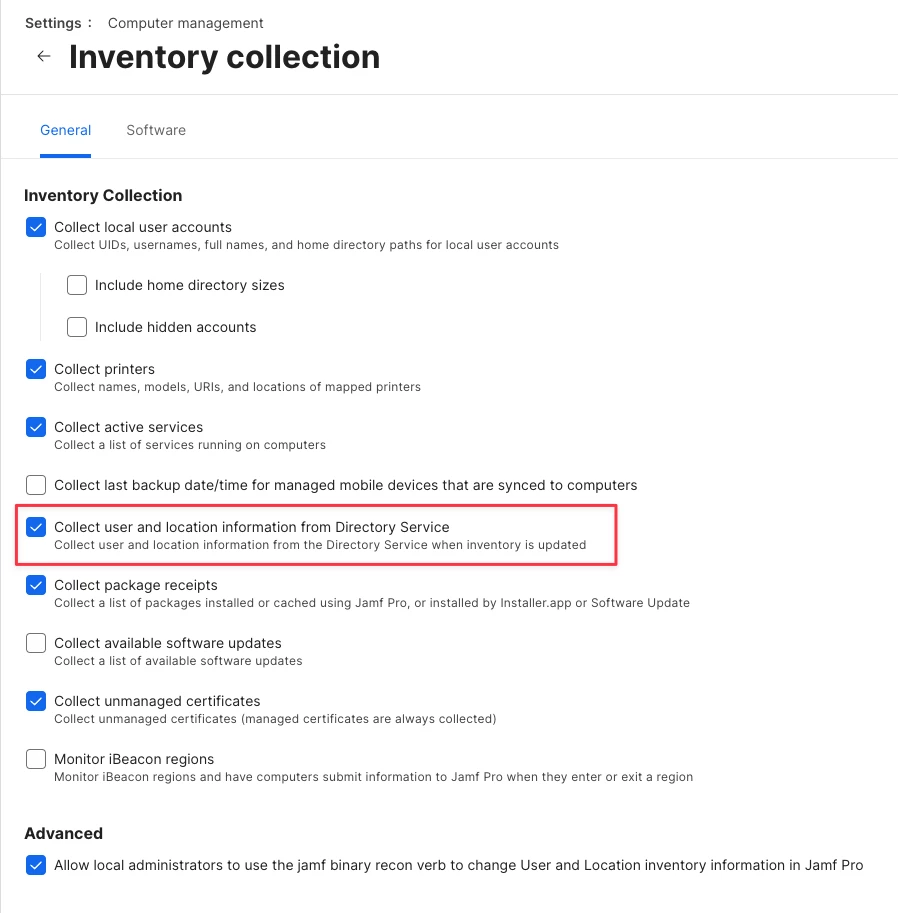
That checkbox is also needed if you want user information to populate on device records in Jamf Pro.
Under Settings -> Computer Management -> Inventory Collection, make sure you have "Collect user and location information from Directory Service" checked.
I just spun up a fresh instance, added Cloud Identity Provider connected to my Entra ID instance, and checked that box and I get the Directory Service Attribute Mapping option in Extension Attributes.

That checkbox is also needed if you want user information to populate on device records in Jamf Pro.
BOOM!
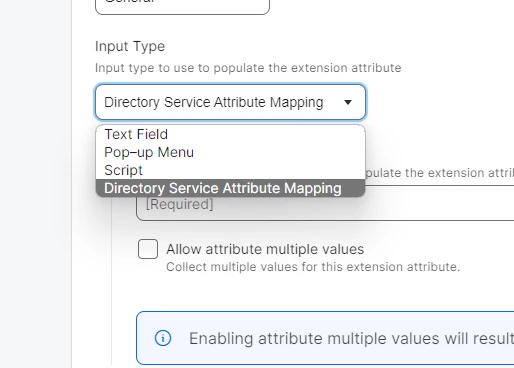
Thanks a lot for that! Cheeky little option that was!
BOOM!

Thanks a lot for that! Cheeky little option that was!
@MMTechno, did you have to do anything else? Still, after finding these instructions, we struggled to pull the fields we wanted. Some examples we want to pull data from are in the pictures below, and we will map to those spots.
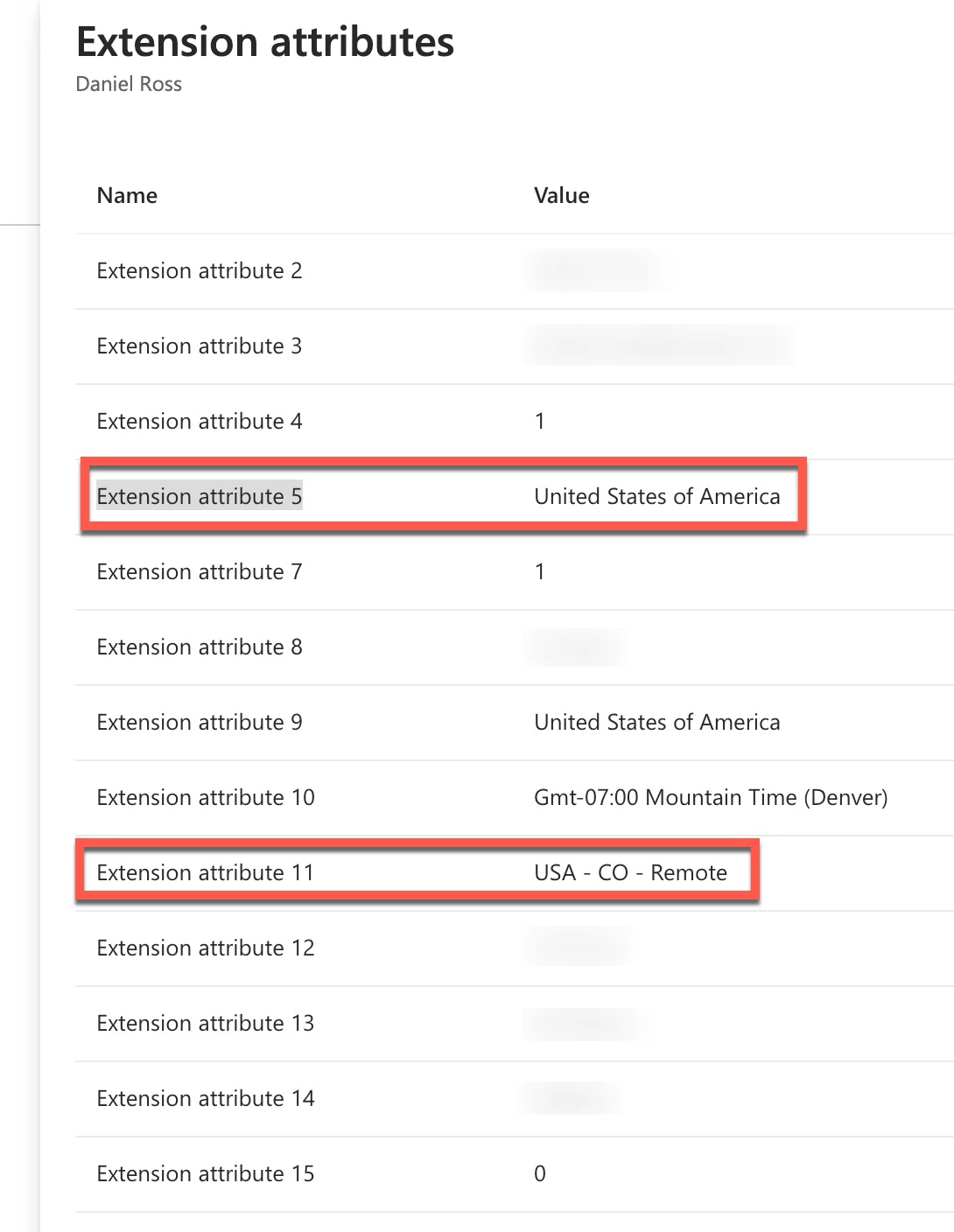
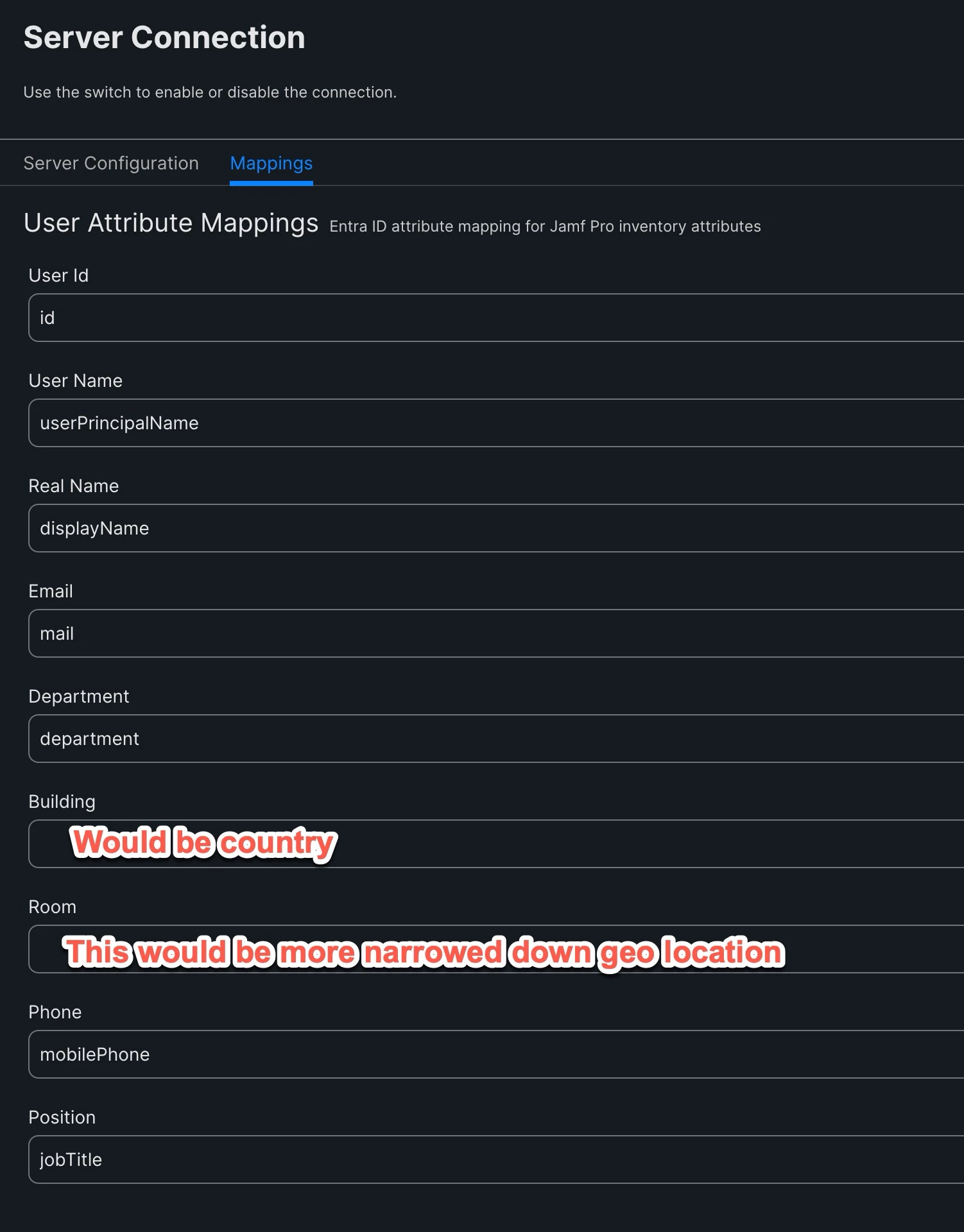
@MMTechno, did you have to do anything else? Still, after finding these instructions, we struggled to pull the fields we wanted. Some examples we want to pull data from are in the pictures below, and we will map to those spots.


@daniel_ross I'm guessing those fall under `onPremiseExtensionAttributes` right? Currently Jamf Pro is unable to collect from that JSON object because it is a list of attributes (like an array).
You may find those attributes elsewhere in the user record where they have a UDID of sorts as part of the name. Something like `extension_a34572989d08a08c899b999a_country`, or whatever. If you have those entires and they are not part of a JSON "array" (for lack of a better term), then you may be able to pull those in.
Yes, you can pull extended attributes from Azure AD into an Extension Attribute. I used the Microsoft Graph Explorer to find a weird attribute (proxyAddresses), one that I knew would not be in Jamf Pro, put it into an Extension Attribute and the info was pulled back.
Hey Steve... Do you know what the attribute name would be to get a list of groups that a user is a member of? When using LDAP, the attribute name was "memberOf" but that doesn't seem to work after switching to an Entra ID connection.
Hey Steve... Do you know what the attribute name would be to get a list of groups that a user is a member of? When using LDAP, the attribute name was "memberOf" but that doesn't seem to work after switching to an Entra ID connection.
As far as I am aware, Entra ID does not have the concept of 'memberOf.' Instead, you determine group membership by looping through every group and checking if the user is part of the group. So unfortunately there is no easy way to build an Extension Attribute to pull in group information because of that.
@MMTechno, did you have to do anything else? Still, after finding these instructions, we struggled to pull the fields we wanted. Some examples we want to pull data from are in the pictures below, and we will map to those spots.


Did you ever solve this? I'm running into this same issue.
Reply
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
