I currently leverage a smart group, softwareupdate -aiR, custom notifications and the deferral option for an automated OS patching workflow both myself and user base are really happy with.
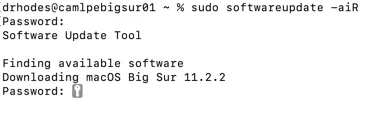
In testing the m1 chipset I am finding softwareupdate -aiR isn't functional in the workflow. Looks like there is an additional prompt for a password prior to downloading??? Anyone seen this or have any ideas as to why?