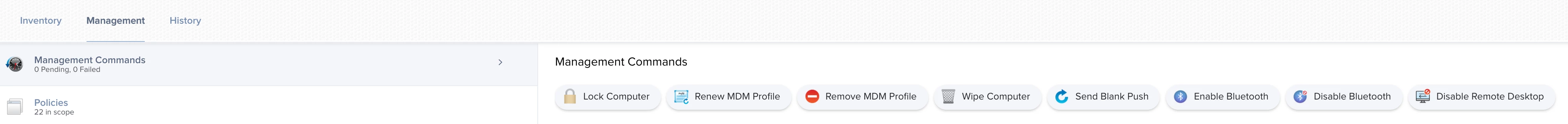
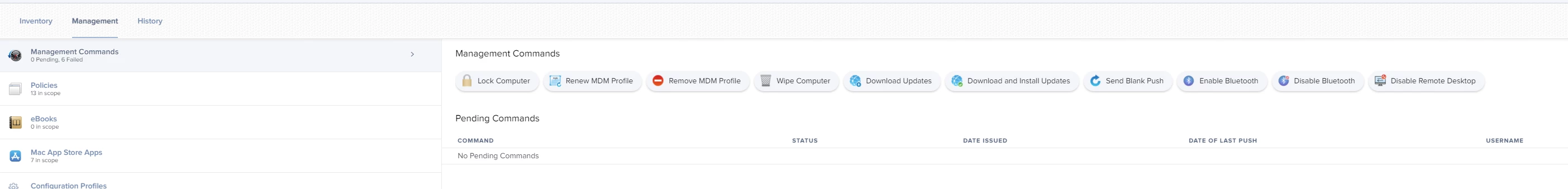
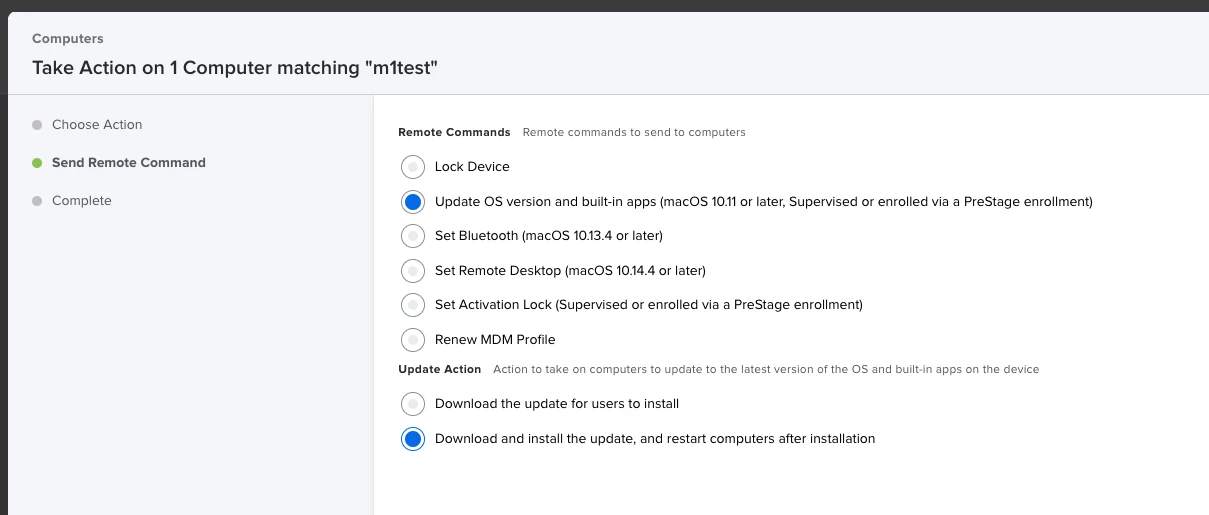
Anyone having issues attempting to update Big Sur devices via Policy and using Apple's Software Update server? The policy is not working for Big Sur including intel machines. Attempting to get the latest update (20D74).
With the terminal open, it states it downloads. It shows as completed in Jamf within the policy. Also within client history. Yet reboot does not install the update.
Mojave and Catalina devices update fine.