Hi All,
I’ve come across a strange issue stopping me rolling out M1 MacBook Pros to our users to replace older Intel machines.
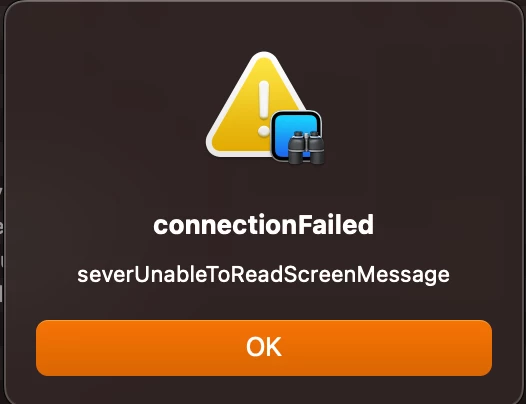
I’m unable to use ARD to screen share onto an M1 Mac in these scenarios:
Filevault on and Firewall on
Filevault on and Firewall off
Works if Filevault is off and Firewall on or Filevault is on and Firewall is off.
I’ve tested a MacBook Pro 14inch and 16inch M1 running Monterey 12.0 through to 12.2 with the same result.
If I test an Intel Mac with the same Filevault/Firewall on, ARD works no problem.
Not sure if I’ve missed something daft on these M1 machines or a bug in Monterey on Apple silicon.
Cheers,
Robert.