Hello, we have configured an 802.1X network profile with a scep profile that generates a machine certificate per computer. When connecting to the network we are forced to select the certificate. Isn't there a way to make the selection automatic?
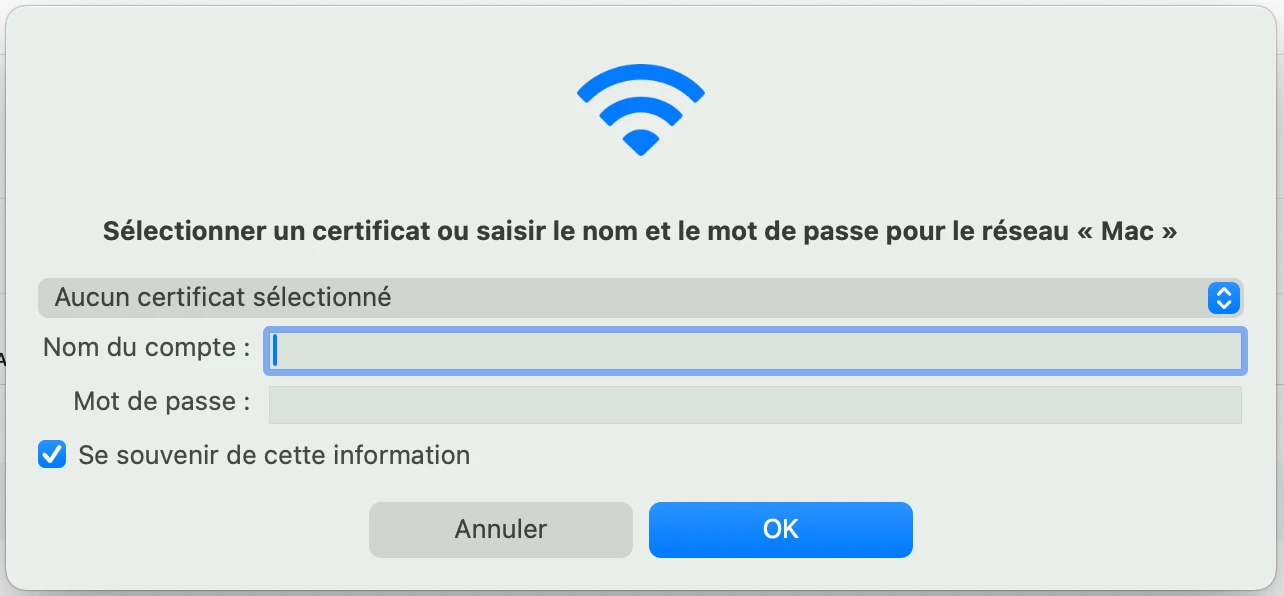
Hello, we have configured an 802.1X network profile with a scep profile that generates a machine certificate per computer. When connecting to the network we are forced to select the certificate. Isn't there a way to make the selection automatic?

Best answer by dletkeman
Short answer: Yes. Make the Wi‑Fi (802.1X) payload explicitly reference the SCEP‑issued identity certificate and anchor trust to your RADIUS CA. When the Wi‑Fi payload is bound to the identity payload, macOS automatically presents that cert and won’t prompt users to choose.
What to change in your profile (Jamf / other MDM):
Identity (SCEP) payload
Ensure you deploy a device (machine) identity via SCEP. This creates the client cert (with private key) in the System keychain. In the Wi‑Fi payload you must select this identity payload as the authentication credential for EAP‑TLS.
Trust (CA) payload(s)
Deploy the full RADIUS server chain (root and any required intermediate CA certs) so the supplicant can validate the server during EAP. If the chain isn’t trusted, the Mac won’t complete EAP‑TLS and you’ll keep seeing prompts. Optionally specify the expected RADIUS server names (CN/SAN) to pin trust.
Wi‑Fi (802.1X) payload
TLSTrustedServerNames).If it still prompts:
# SHA-1 of the identity’s certificate
CERT_SHA1="ABCDEF1234..."; SSID="Mac"
security set-identity-preference -Z "$CERT_SHA1" \
-s "com.apple.network.eap.user.identity.wlan.ssid.${SSID}" \
/Library/Keychains/System.keychain(Jamf Nation thread discusses this approach and the com.apple.network.eap.user.identity.wlan.ssid.<SSID> naming.)
Re‑check RADIUS trust: If the client doesn’t trust the RADIUS cert/hostname, it won’t present its certificate (and you’ll see handshake failures in your NAC logs). Make sure the correct CA(s) and, if required, the server name(s) are in your Wi‑Fi payload.
Check login keychain for any competing 802.1x certificates and delete them.
Disclaimer: I had ChatGPT help me with some of the formating and wording and this will hopefully will help you. This meshes with what has helped me in the past.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.