Hi,
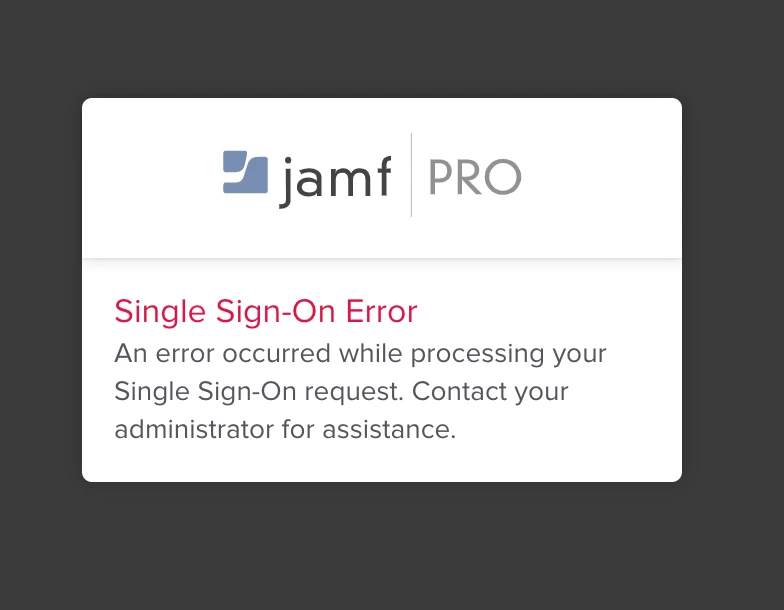
We have recently deployed Azure AD SSO (and Azure AD DS) to login to our Jamf Cloud instance.
It works great apart from SSO, every 24 hours we have to reset our web browser data to login to Jamf Admin.
Any ideas on how to make this more reliable? I's guessing its something to do with 'Token Expiration (Minutes)'. Should I just increase this to a few weeks?