I imagine I'm not alone on this. I set up a 10.13.4 machine with DEP.
In the prestage enrollment, I have it create our admin account(account ID of 501, not a hidden account). Skip the setup user stuff and most the setup assistant.
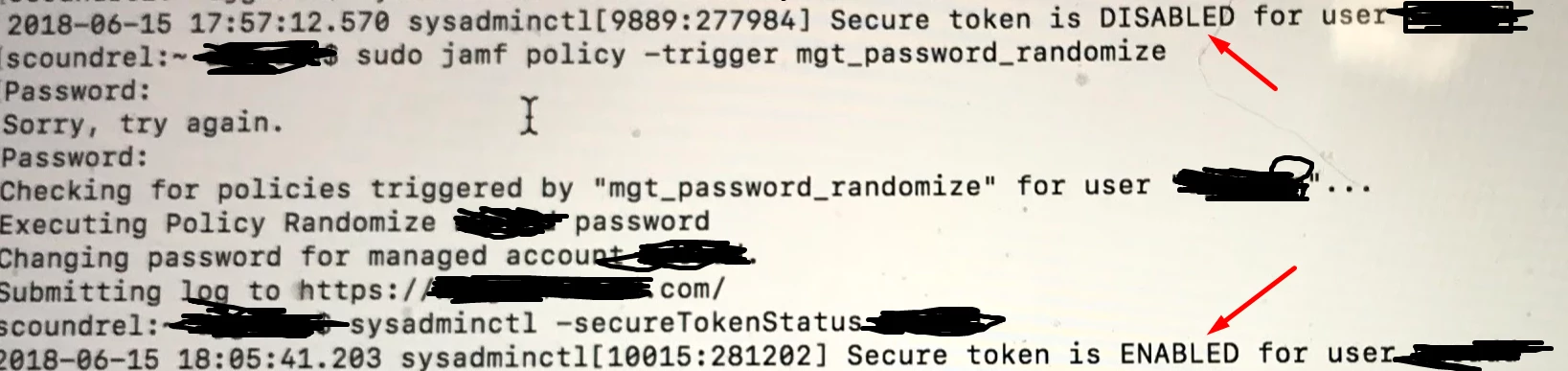
I thought I figured out how to get a secureToken, that if I logged in as our local management admin account as the first user instead of an AD account(which creates a managed mobile account). It would give the management account the secureToken and no problems and I could then use FileVault on the machine. I swear this was working. And now it isnt....
Has anyone figured out a workaround or solution?
I've thought about when I redo a machine from scratch we could install 10.12, set everything up then upgrade to 10.13. This will work with machines we currently own but not newly purchased. I've also thought about squeezing the last life out of imaging since you can(but shouldn't) image using HFS+.