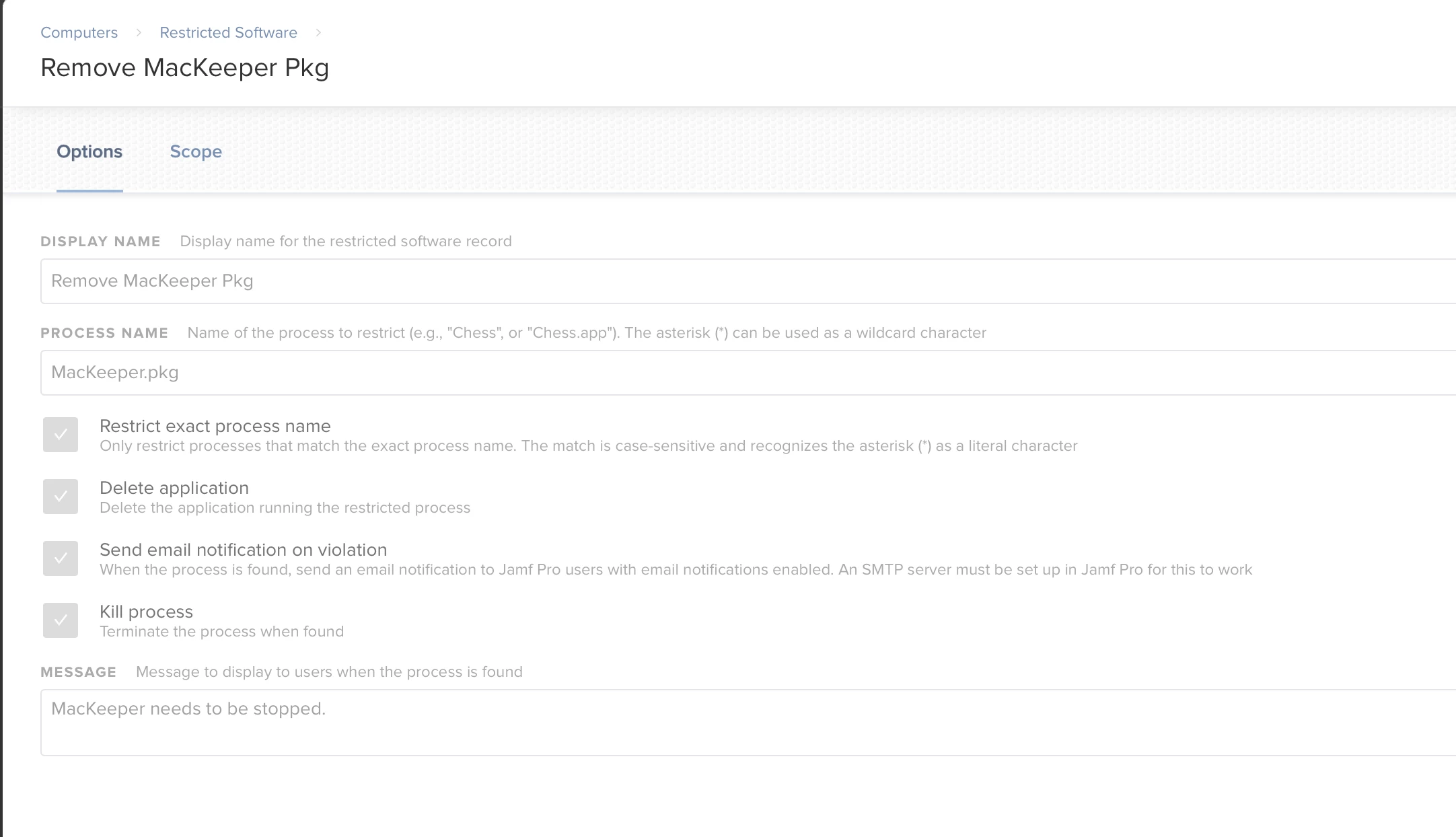
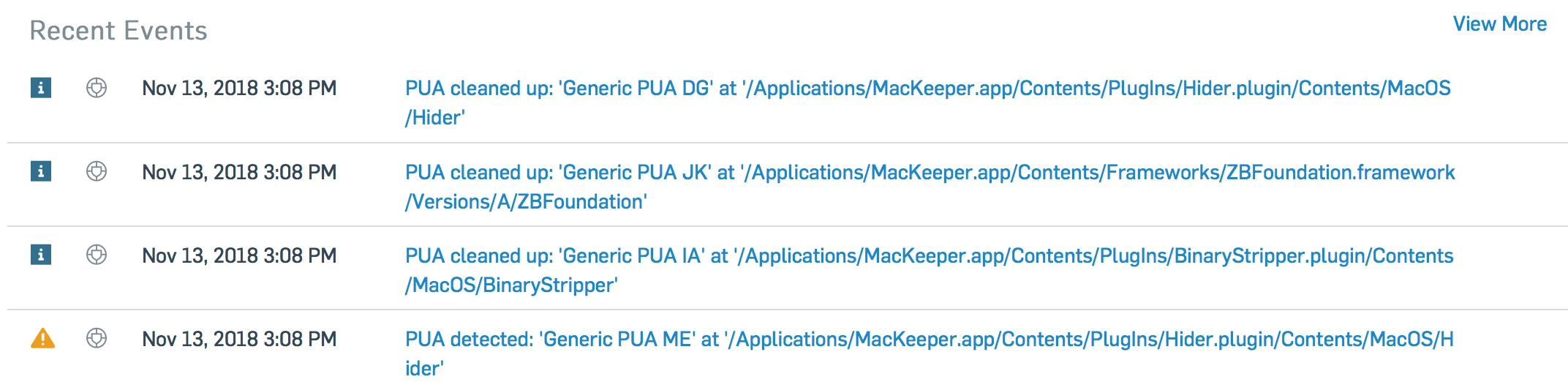
If you don't know what this is it's a nasty app that a lot of Mac users download. I would like to remove this file anytime it gets downloaded on a Mac. I need it to scan the users whole home folder. I have created a restricted app in JAMF, but it doesn't seem to work more than once.
Example file names:
MacKeeper.pkg
MacCleaner*
MacKeeper.app