Hello everyone,
We're having problems with students changing the DNS configuration to access forbidden sites.
Is it possible to block the Manual DNS option in JAMF Pro? See screenshot below
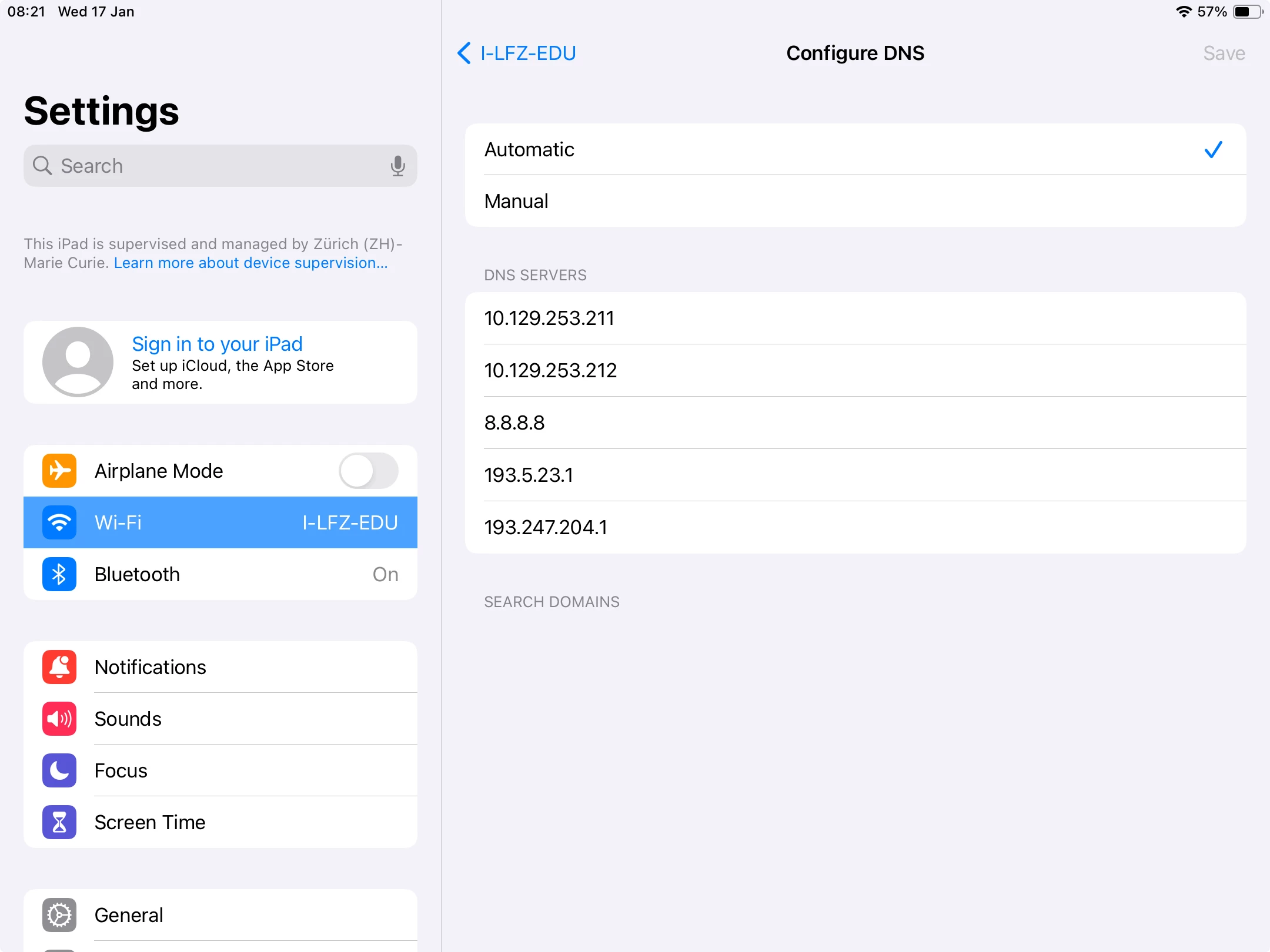
Thank you in advance for your help.
 +5
+5Hello everyone,
We're having problems with students changing the DNS configuration to access forbidden sites.
Is it possible to block the Manual DNS option in JAMF Pro? See screenshot below

Thank you in advance for your help.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.