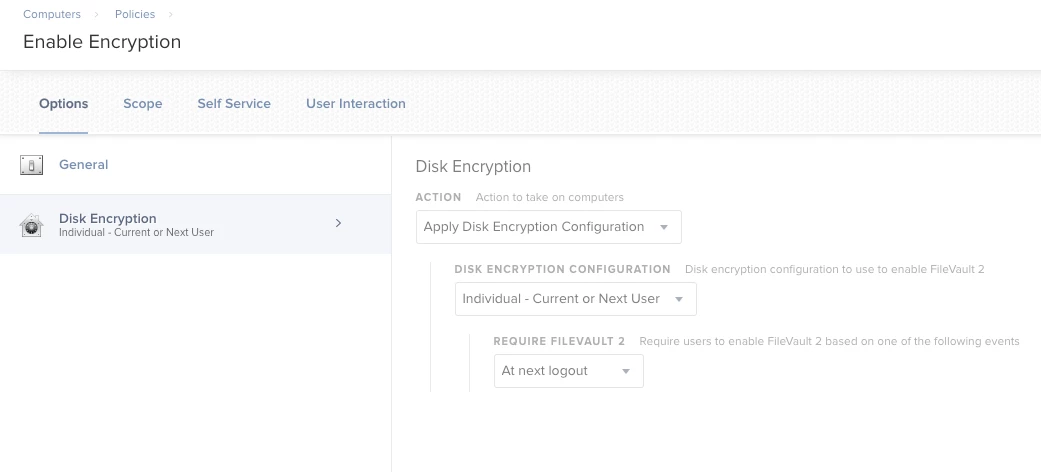
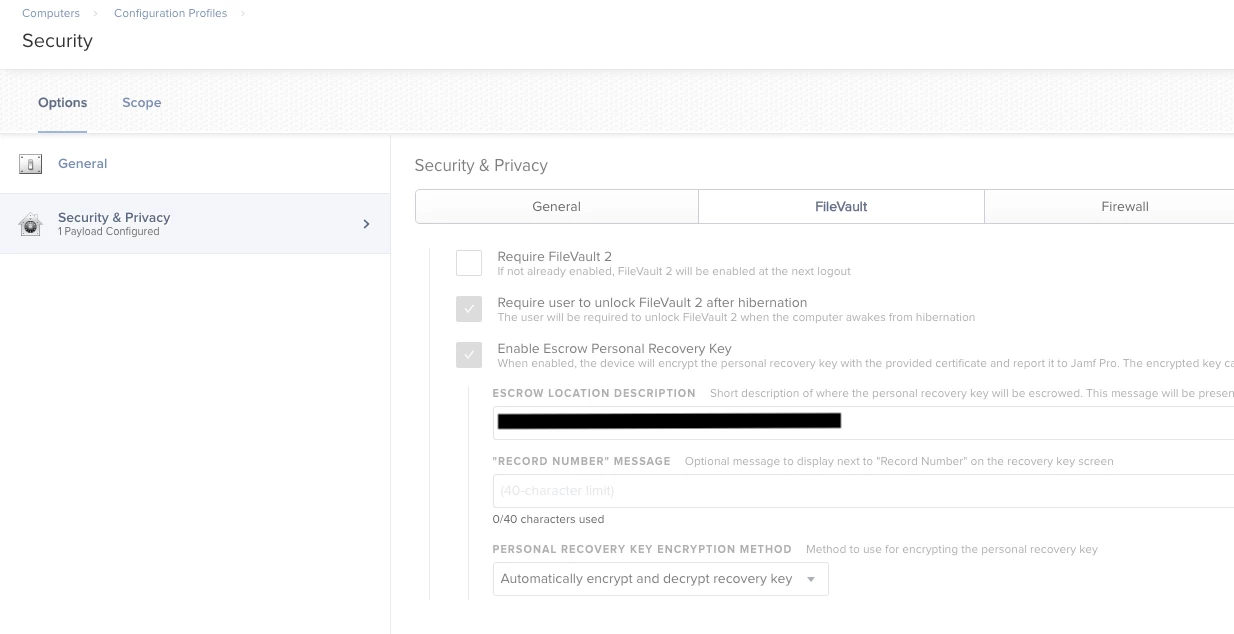
I'm currently testing out Catalina on a VM. I have the Security & Privacy MDM profile deployed to it with the setting enabled to require FileVault.
When I reboot the VM, I am prompted for my password. It says that it will enable FileVault, but it never does - the Mac just reboots and then I go through the same process all over again.
If I enable FileVault through the local Mac settings it works fine.
Is anyone else having this issue? Any idea why the MDM setting is not enabling FileVault?