I got dropped into a sticky situation and need some help strategizing...
I'm trying to work out a system for getting a client's entire fleet (about 4,000 computers globally) to switch from an institutional FV2 key, to escrowed personal keys. There is currently a single management account on each machine, but some of the machines don't have that account enabled for FV2; on those particular machines, only the employee's account is enabled. Additionally, the password for that management account can be any one of many permutations of the management password, and there is no way to know for sure which one it is for any given machine.
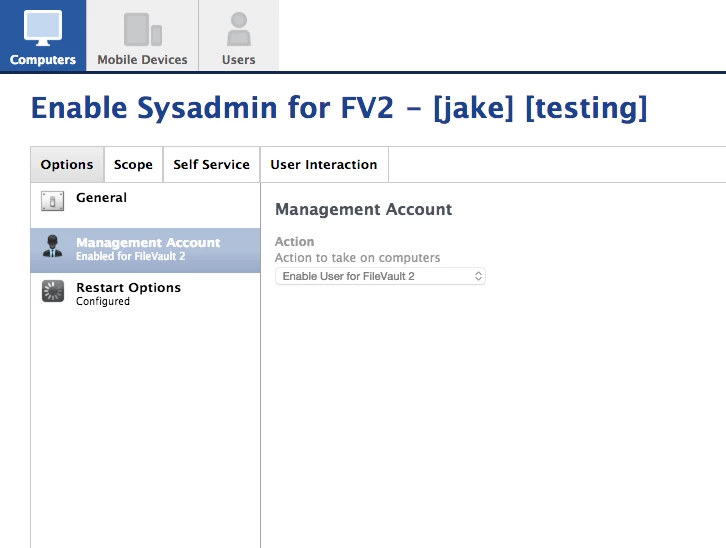
I'm pretty sure I can solve the problem for the unknown passwords, as well as the problem for FV2 on the computers that have the management account enabled. I have a bash script that will reset the password for that account on all machines that need it. I can also use fdesetup to change keys on the systems that have the management account FV2 enabled (I believe). What I can't figure out is: how am I going to change the recovery key type AND enable the management account on computers that don't have the management account enabled?
The three strategies I can think of:
1. somehow use the institutional key and expect in a bash script to get past the fdesetup prompt to unlock the hard drive. (I haven't figured out how to do this yet)
2. prompt the logged-in user to enter their password into a branded OSAscript or jamfhelper dialog box and pass that to expect. (Infosec will never let me do this.)
3. manually enable the management account on all machines that don't have it enabled, then use the Casper policy to change the recovery key type
Is there any other way to do this? Am I overthinking this?