Like a lot of others on here, we are educators that have been having a rash of students loading extensions in Chrome in order to run VPNs, games, etc. After standing on the shoulders of some much better scripters in JAMF Nation, we came up with the below deterrent. There is a never-ending list of extensions, so the question was really: "Do we want to limit their ability to load any extensions, or curb the behavior itself?" We went for 'curb the behavior'.
Most of this is based off of a couple of scripts I snagged here in the following discussion:
my link text
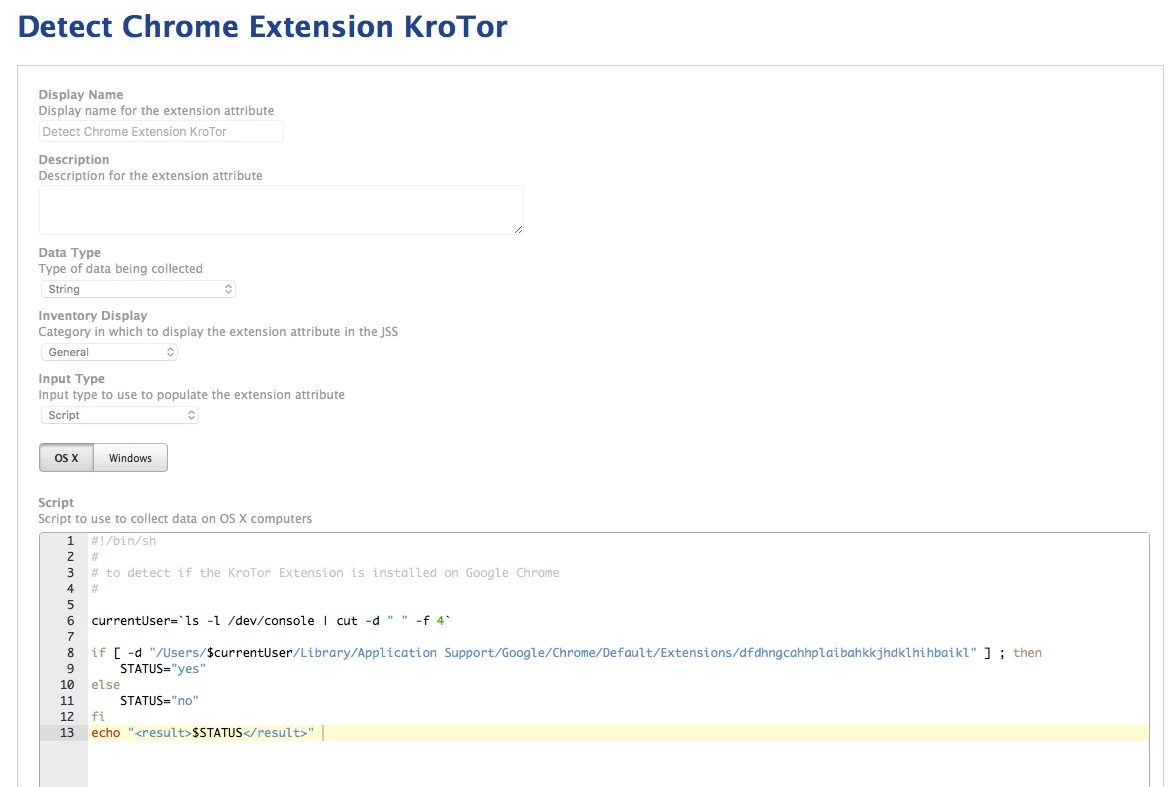
• First we got a list of offending extensions by scanning systems using @chriscollins script for reporting on installed Chrome extensions
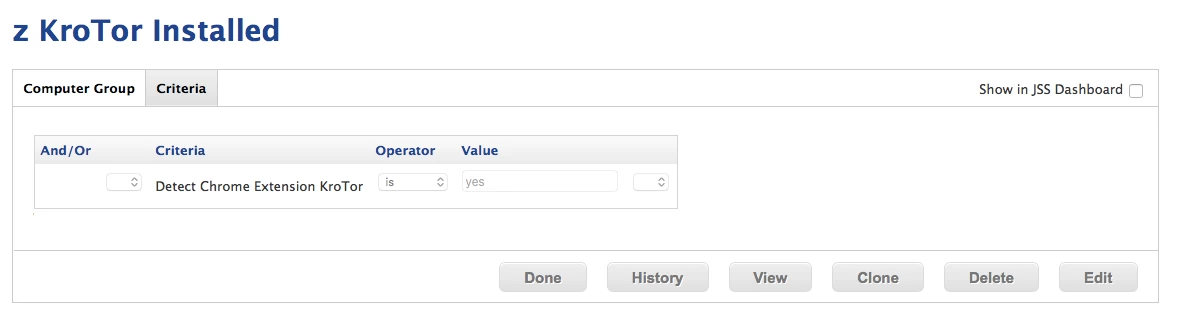
• Once we had the nasty extension we wanted too target, we created Smart Groups with @emilykausalik script
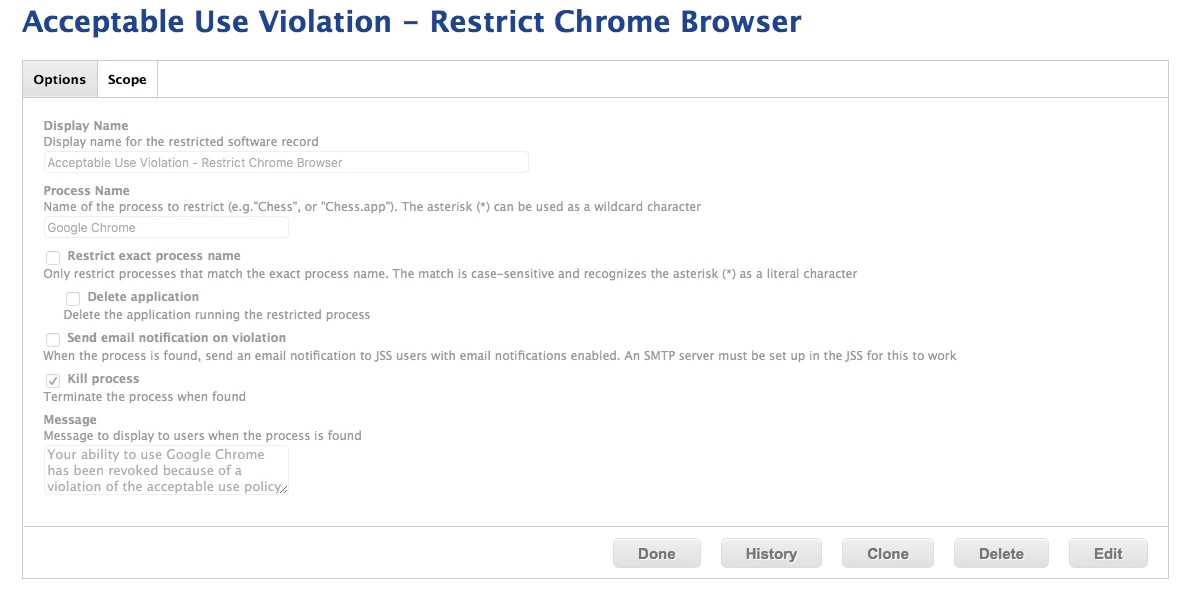
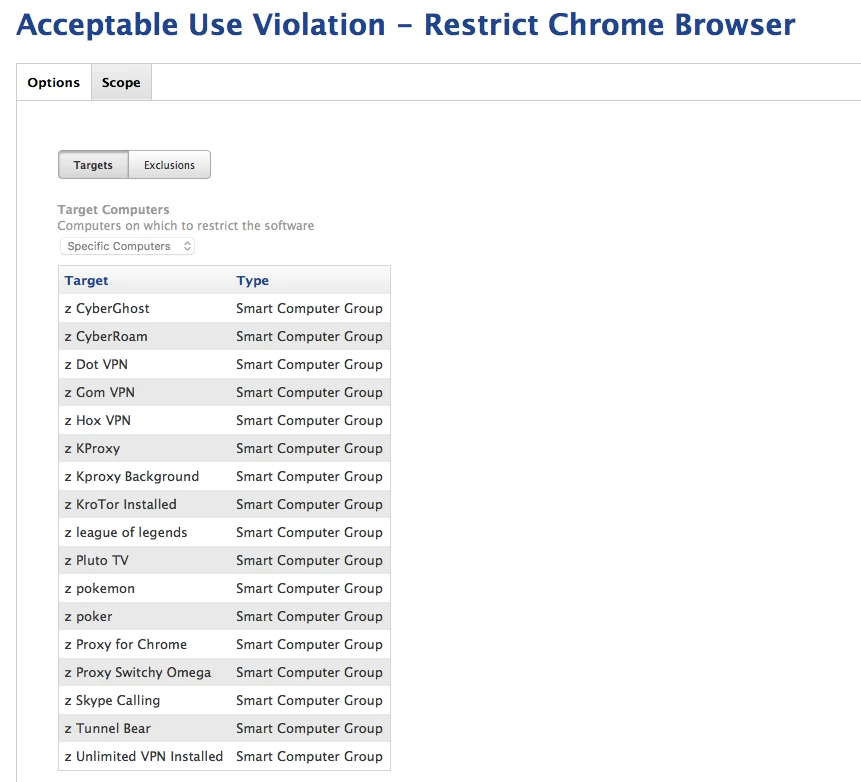
• We then built a Restricted Software rules that killed the Chrome and Firefox processes if they were in one of the offending Smart Groups, and it displayed the following message "Your ability to use Google Chrome has been revoked because of a violation of the acceptable use policy." - (we killed Firefox too because the assumption is that the behavior will just jump browsers)
The end result being that the student is then stuck using only Safari to do their schoolwork (the principal has commented that he thinks this may be against the Geneva Convention ;-) ). If they wish to have the blocks on Chrome and Firefox undone they must seek Administrations help.
We simply reverse it by the users browser profile folder out of Application Support, running a new inventory and then finally a 'sudo jamf manage' all from a policy in Self Service only available to Admins.
The end result: Kids don't really like Safari, and it has way less handy extensions and can be managed more strictly with Parental Controls if need be, so we are targeting the behavior without limiting the 'good' extensions coming in.
- One caveat: We have found that many of these Extensions are getting in when the student logs in to they personal gmail account and it comes over with their profile. So if they act surprised we let them know that is is their responsibility to check this stuff.