Edited 4SEPT2024: Updated information with the release of Jamf Pro 11.9 for PSSO and Device Compliance. Also added link to Jamf Pro documentation.
Jamf Learning Hub Instructions:
https://learn.jamf.com/en-US/bundle/technical-articles/page/Platform_SSO_for_Microsoft_Entra_ID.html
Current Public Preview Limitations
What is Public Preview
As of 15 JUL 2024, Microsoft Entra ID support for Platform Single Sign-On extension (PSSOe) is currently in Public Preview. As such, supported features and deployment information is subject to change without notice. For more information, visit https://learn.microsoft.com/en-us/entra/fundamentals/licensing-preview-info.
Jamf Pro and Microsoft Entra Conditional Access
Jamf Pro 11.9 and greater now includes logic to detects changes to PSSO registration. When a new device ID is created in Entra ID as part of the registration, the gatherAADInfo command will report device compliance state to the new object.
For versions prior to Jamf Pro 11.9, visit the Troubleshooting Steps for commands to restore device compliance data being sent to the new device ID created in Entra ID manually.
Administrators are recommended to:
- Configure Jamf Pro for Device Compliance - https://learn.jamf.com/en-US/bundle/technical-paper-microsoft-intune-current/page/Device_Compliance_with_Microsoft_Intune_and_Jamf_Pro.html
- Configure Jamf Pro to deploy a Platform Single Sign-On configuration profile
With this method, when a user registers a device with the Platform Single Sign-On flow, the device compliance will automatically be sent to Entra.
In the event that an organization deploys PSSO first and then later configures and deploys Device Compliance, the user must run the "Register Device with Microsoft" policy from Jamf Self Service or the administrator must deploy a policy to run the gatherAADInfo command at least once before device compliance will be reported.
Prepare a non-production test machine
Any experimentation with the login window has the potential to lock a user out of their machine. Therefore, use only non-production test equipment when testing and evaluating PSSOe.
Support
PSSOe is a framework built into macOS and the core functionality is designed by Apple. It is supported by a companion application built by an identity provider. It is enabled by deploying a configuration profile via an MDM.
- For questions and feedback about the core functionality of PSSOe or any feature using available betas of upcoming versions of macOS, contact AppleCare (https://www.apple.com/support/products/), file an AppleCare Enterprisesupport case, or file a feedback via https://feedbackassistant.apple.com
- For questions about the Microsoft Intune Company Portal application, contact Microsoft Support, subject to the limitations in the link above about preview features.
- For questions about deploying a configuration profile using a Jamf MDM product, contact Jamf Support(https://www.jamf.com/support/)
Deployment
Determine authentication method
Microsoft Entra ID supports three methods of authentication with PSSOe:
- Secure Enclave (Recommended) - This method creates hardware bound cryptographic keys entangled with the Secure Enclave (link:https://developer.apple.com/documentation/security/certificate_key_and_trust_services/keys/protecting_keys_with_the_secure_enclave) of the Mac hardware. Keys are not directly accessible by the user, do not store keys in the user’s Keychain, and are non-exportable. This method is recommended as it is treated by Microsoft Entra ID as a non-phishable authentication method, the strongest authentication factor type for accessing resources. The local UNIX user name and password are unchanged with this method.
- Password - This method will synchronize the local macOS UNIX user account password with the Microsoft Entra ID password. The user FileVault decryption password and Keychain password are updated to match the local UNIX account password.
- This is not considered a phishing resistant authentication factor. Setup does not require the use of a strong authentication method like multifactor authentication, and the method does not allow for use of the device as a Passkey for WebAuthN authentication.
- Administrators are strongly recommended to check all password complexity requirements in Microsoft Entra ID and password complexity configuration profile payloads passed via MDM. Conflicting complexity requirements or policies like preventing the use of previously used passwords will result in user lockout of the device.
- Legacy per-user multifactor authentication is not supported with this method and will result in the user being unable to register their account for use with PSSOe. Refer to https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-authentication-methods-manage for deprecation dates and how to migrate to Microsoft Entra Conditional Access policies for MFA enforcement.
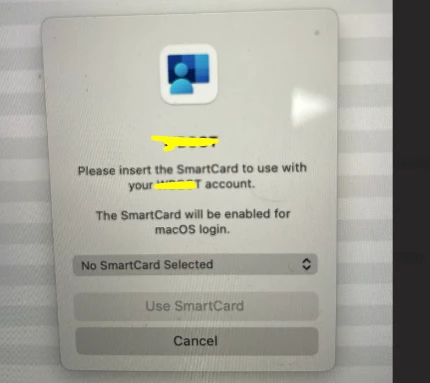
- SmartCard - Associates a user’s SmartCard (also known as PIV or CAC card) and PIN with Microsoft Entra ID authentication methods. The local UNIX user name and password are unchanged with this method. Because this method requires additional hardware for both the credential storage and readers for the credentials, administrators are not advised to use this method unless SmartCards are already in use at the organization.
Install the Company Portal app
PSSOe requires the installation of Microsoft Intune Company Portal app (https://go.microsoft.com/fwlink/?linkid=853070) version 5.2404.0 or greater.
Install Company Portal via Policy
Open the Jamf Pro administrator portal.
Navigate to Settings, Computer Management, Packages.
Upload the latest version of Microsoft Intune Company Portal installer package file to your fileshare distribution point.
Navigate to Computers, Policies.
Create a new policy with an Execution Frequency set to Once Per Computer, a Packages payload to install the Microsoft Intune Company Portal package, and a Maintenance payload to Update Inventory. Execution trigger can be set to Recurring Check-In or installed via Self Service by the user on the device.
Install Company Portal via Jamf App Catalog
Open the Jamf Pro administrator portal.
Navigate to Computers, Mac Apps.
Select the “+ New” option to create a new app installer.
Select App Source as the Jamf App Catalog.
Search for “Microsoft Intune Company Portal” and select the Add button to add the title.
Select a Target Group to deploy the application.
In the Configuration Settings option, select either to install automatically or via Self Service. Select the Update method to Automatic if you wish to keep the Company Portal app up to date with the latest version automatically.
Once the installation method is configured, install the Company Portal application on your non-production test device.
Create a configuration profile
Open the Jamf Pro administrator portal.
Navigate to Computers, Configuration Profiles.
Select the “+ New” option to create a new Configuration Profile.
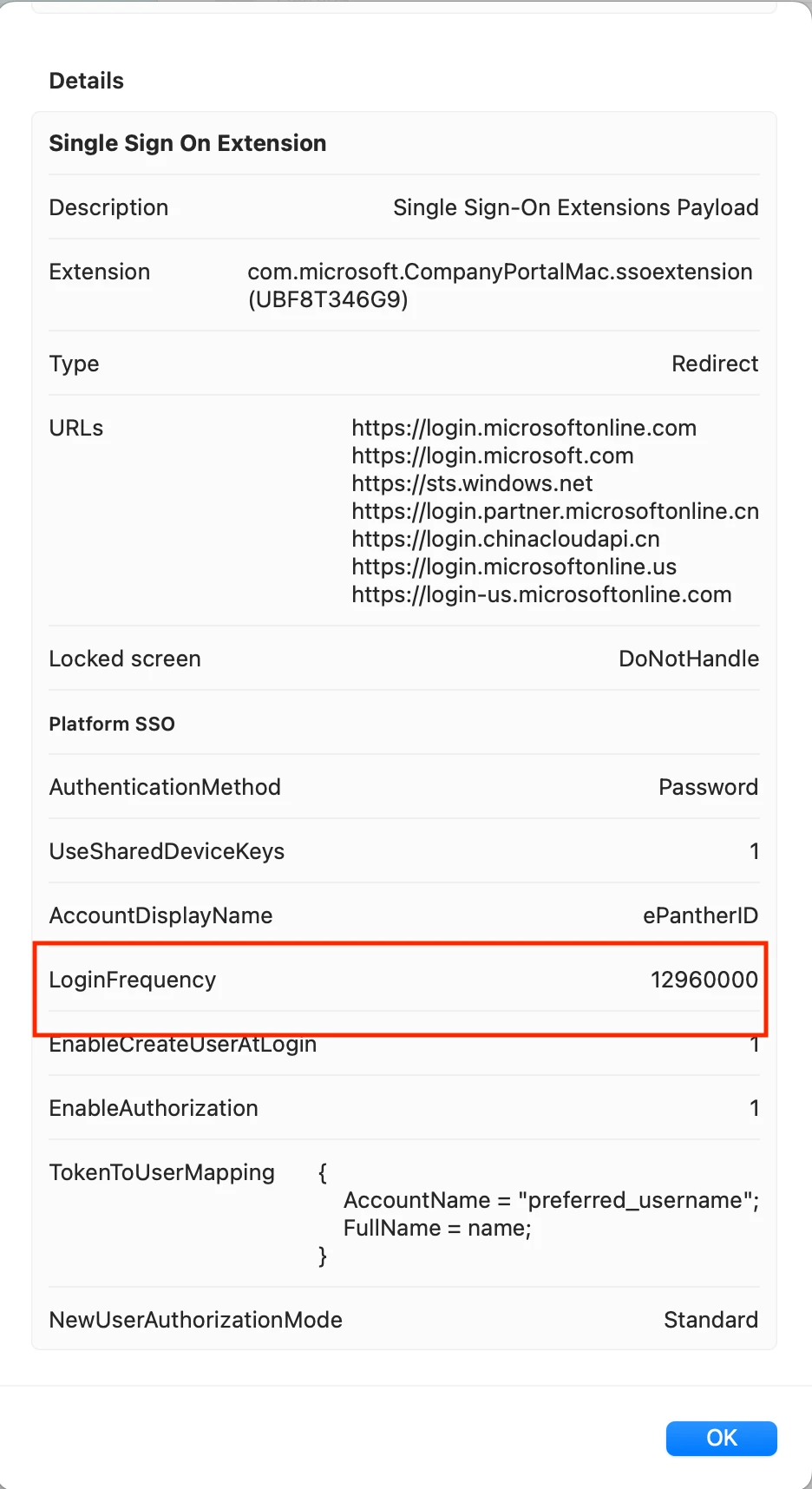
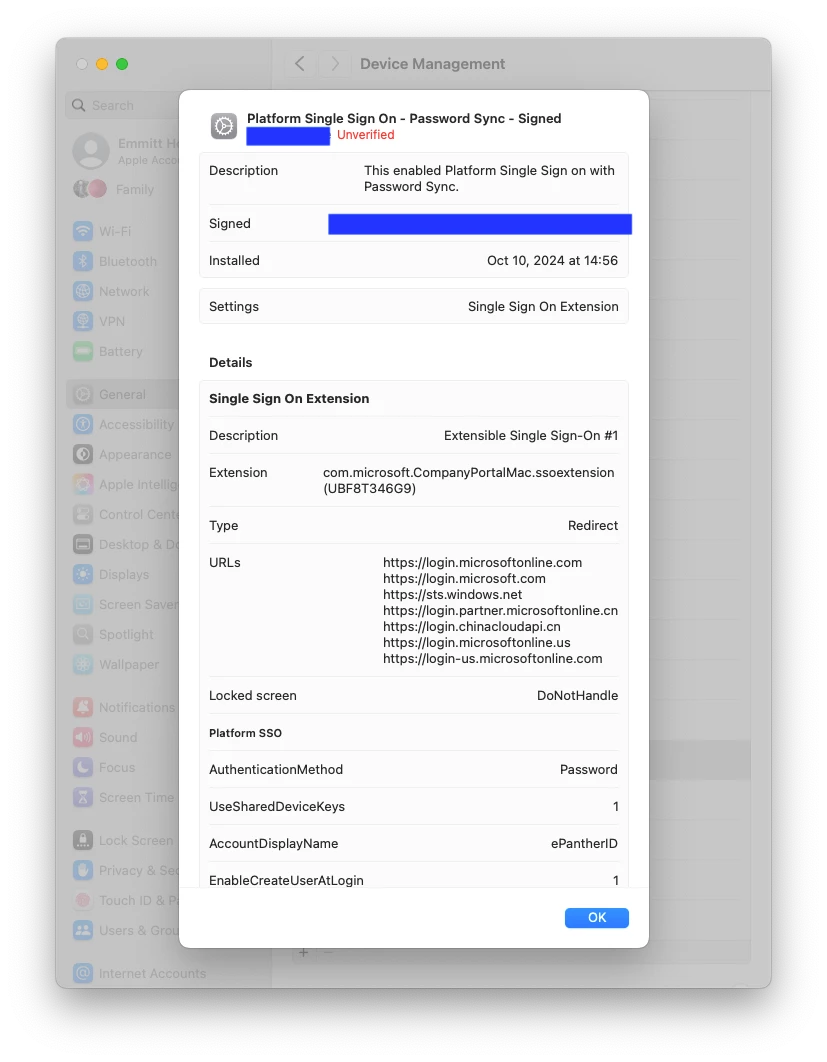
Select the payload for “Single Sign-On Extensions” and select the “+ New” option to add payload contents.
- Payload Type: SSO
- Extension Identifier: com.microsoft.CompanyPortalMac.ssoextension
- Team Identifier: UBF8T346G9
- Sign-on Type: Redirect
- URLs: URLs will be redirected to authenticate with the associated application (Intune Company Portal app). For a full list of URLs, refer to https://learn.microsoft.com/en-us/entra/identity-platform/apple-sso-plugin and are subject to change. At time of writing the minimum required URLs were:
- https://login.microsoftonline.com
- https://login.microsoft.com
- https://sts.windows.net
- Additional URLs for sovereign cloud domains are optional
- Enable the option for “Use Platform SSO”
- Select the Authentication Method your organization has selected
- Use Shared Device Keys: Enable
- (OPTIONAL) Create New User at Login
- Selecting Enable will allow any user with valid credentials on your Entra ID domain to create a new user account on the Mac. A local macOS UNIX user account will be created with the user’s Entra ID password. Users with “passwordless” only authentication in Entra ID cannot use this method.
- (OPTIONAL) Identity Provider Authorization
- Selecting Enable will allow the use of Entra ID credentials for events that require authorization prompts like use of the sudo command, unlocking certain preferences in System Settings, and installation of software. The user must have administrator rights in addition to complete authorization.
- Display Account Name: Enter a value that will be clear to your end users what user name and password is required upon registration of the device with PSSOe. These dialog boxes are displayed by macOS to prompt the user as part of the registration process.
- User Mapping - name from the identity provider ID token claim that contains the information to create the user account
- Full name: name
- Account user name: preferred_username
- A list of all additional claims is available at https://learn.microsoft.com/en-us/entra/identity-platform/id-token-claims-reference#payload-claims
- Account authorization type: Determines if entry of identity provider credentials during an authorization event will show the user is a member of the Admin or Standard users group. Select either Standard or Admin. (Groups is not supported by Microsoft Entra ID at this time).
- New user account type: Determines if a user created at the macOS login window with identity provider credentials will be a local Admin or Standard account. Select either Standard or Admin. (Groups is not supported by Microsoft Entra ID at this time).
- Authentication when screen is locked: Set to Do not handle
- (OPTIONAL) Custom Configuration: Microsoft Entra ID supports several additional configuration settings. Refer to https://learn.microsoft.com/en-us/entra/identity-platform/apple-sso-plugin#manual-configuration-for-other-mdm-services for a full list of settings.
A standard Custom Configuration payload may look like the following:
<?xml version="1.0" encoding="UTF-8"?><plist version="1.0"><dict> <key>AppPrefixAllowList</key> <string>com.microsoft.,com.apple.,com.jamf.trust,com.jamf.management.,com.jamf.protect,com.jamfsoftware.</string> <key>browser_sso_interaction_enabled</key> <integer>1</integer> <key>disable_explicit_app_prompt</key> <integer>1</integer></dict></plist>Scope the Configuration Profile to your non-production test devices.