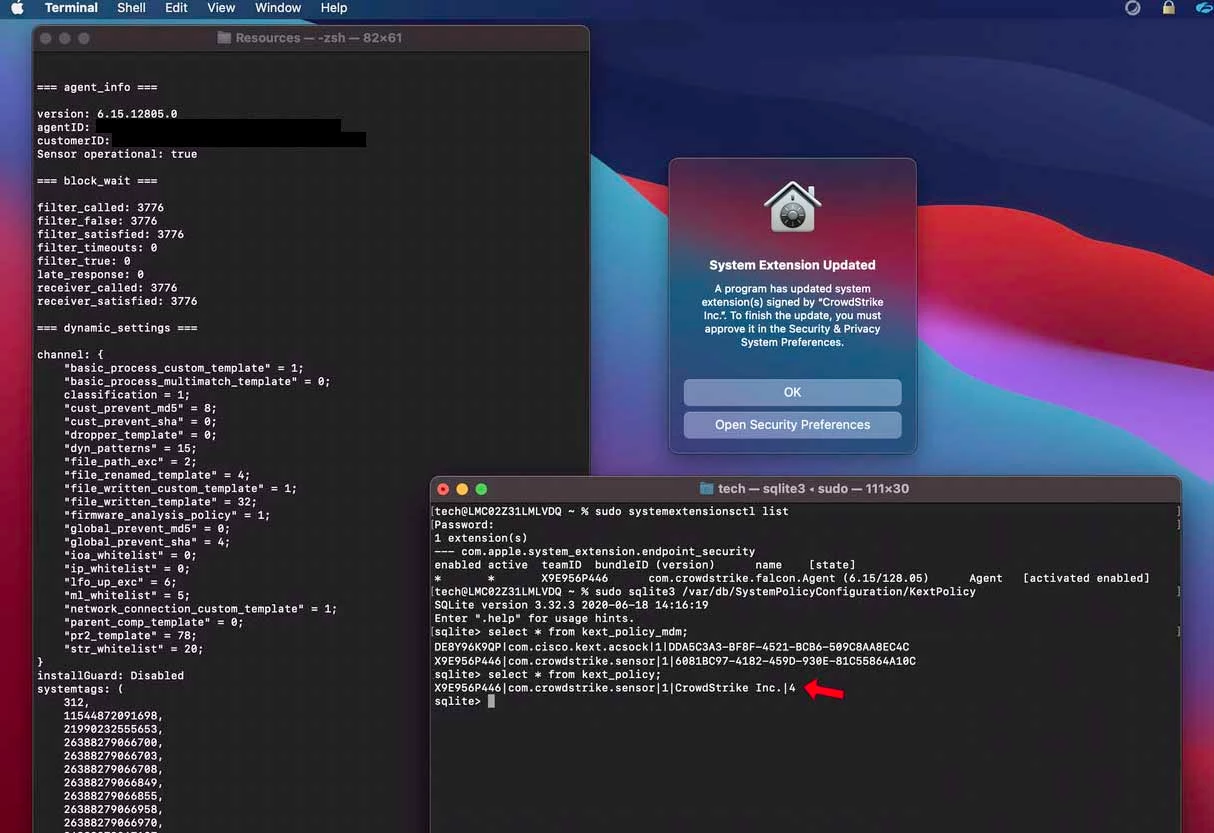
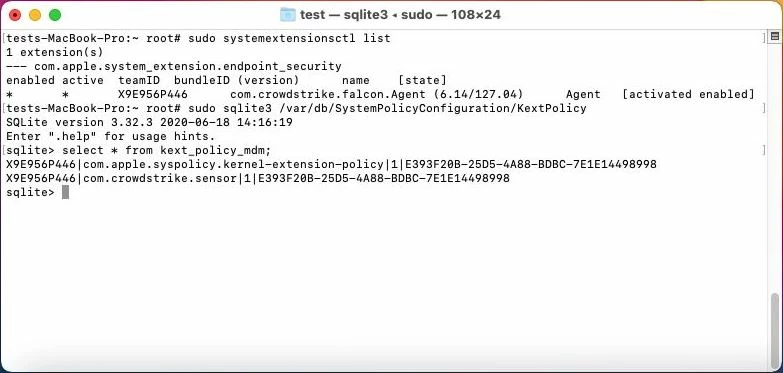
If you have to install version 6 and above of crowdstrike on bigsur, have to install their unsigned profile first. This profile only be uploaded and distributed with MDM solutions.
In order to upload to MDM, that profile needs to be signed first.
Original location of the profile --- > https://supportportal.crowdstrike.com/s/article/Tech-Alert-Preparing-for-macOS-Falcon-Sensor-6-11
1 - Follow Steps explained here,
https://www.jamf.com/jamf-nation/articles/649/creating-a-signing-certificate-using-jamf-pro-s-built-in-certificate-authority
If jamf freezes during generate of pem, ignore it & refresh the page
2- After it is generated under keychain, please locate the certificate and look for "Subject Key Identifier" Value. Copy it to clipboard and remove spaces.
3- Generate signed version of the mobile config profile following below command at terminal
sudo /usr/bin/security cms -S -Z SubjectKeyIdentifierValue -i ActualPathofUnSignedProfile -o OutPutWhereYouLiketoSaveSignedProfile