Hello All
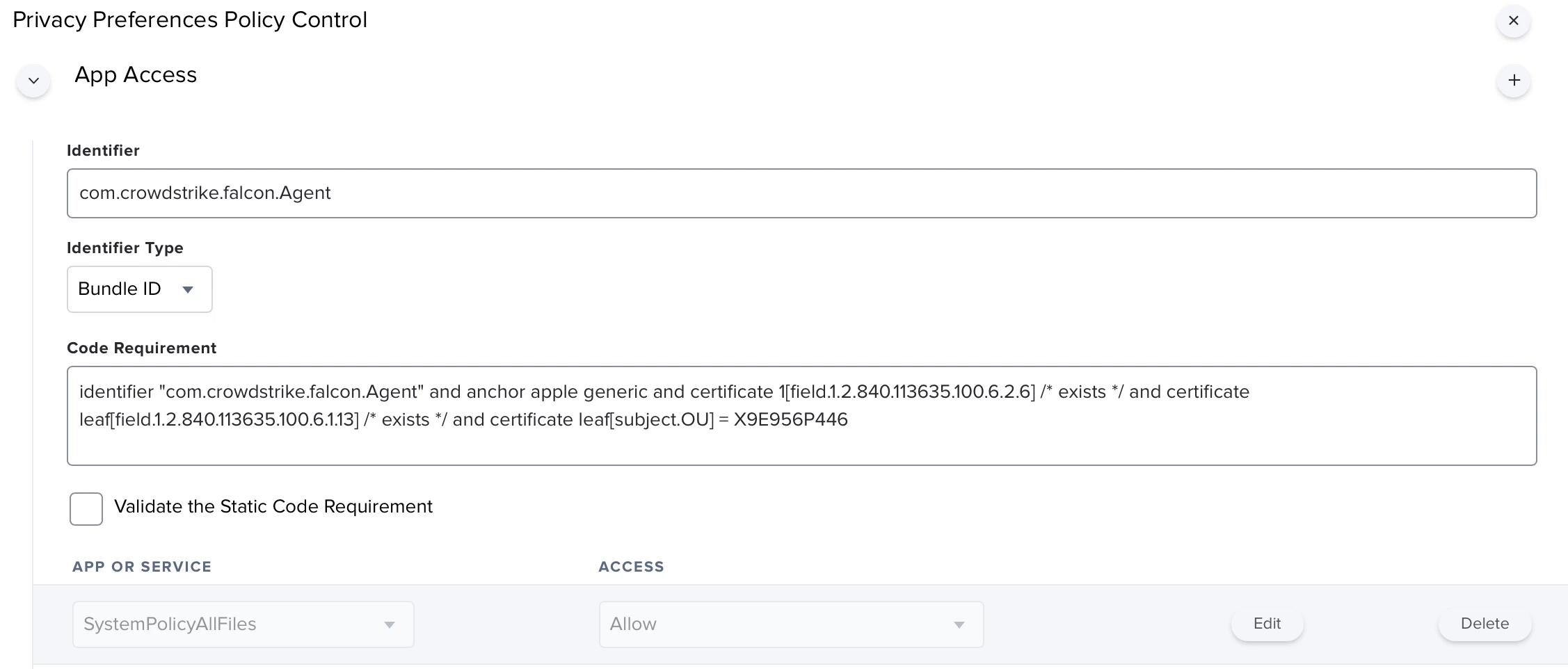
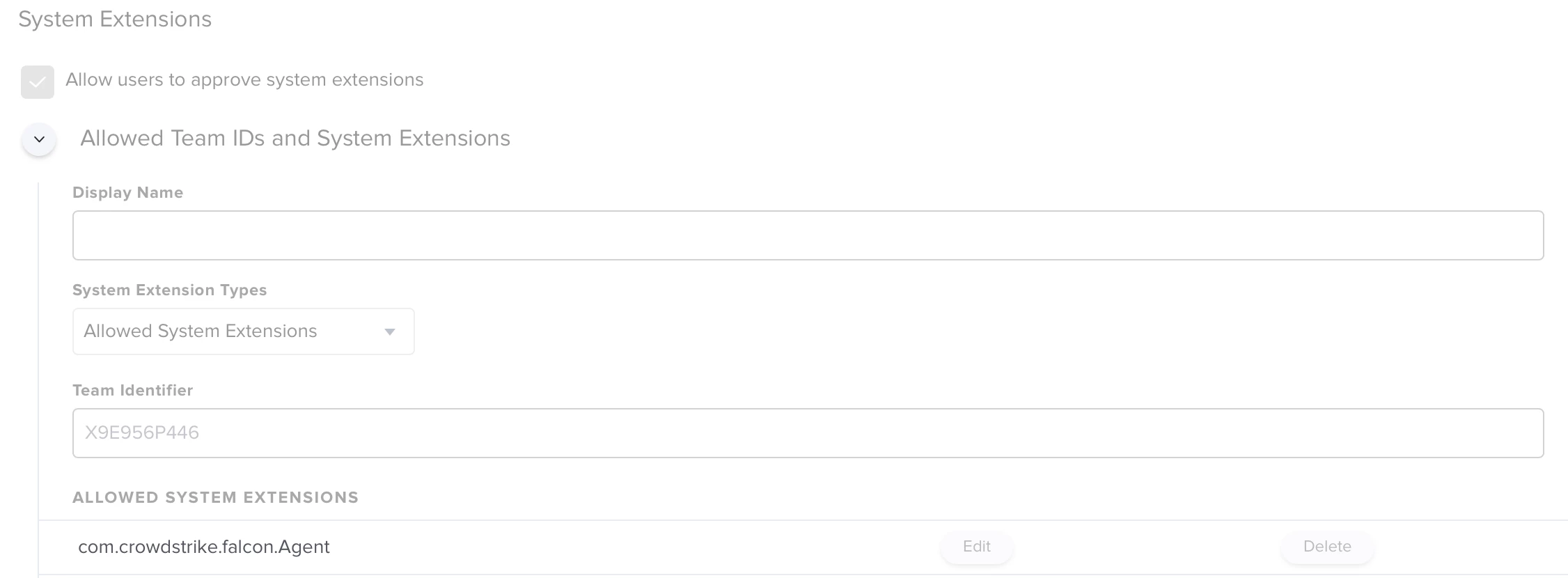
I successfully deployed the CrowdStrike with this instruction; however, the user has to manually allow the Full Disk Access in the Security & Privacy.
https://supportportal.crowdstrike.com/s/article/ka16T000000wwxVQAQ
Does anybody know how to do it or can lead me to the instruction? I have read several articles and got confused.
Thanks
Nam