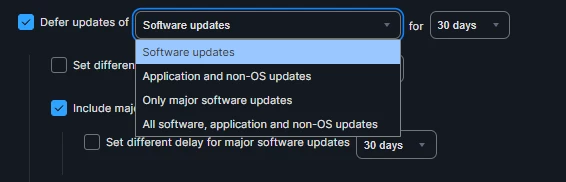
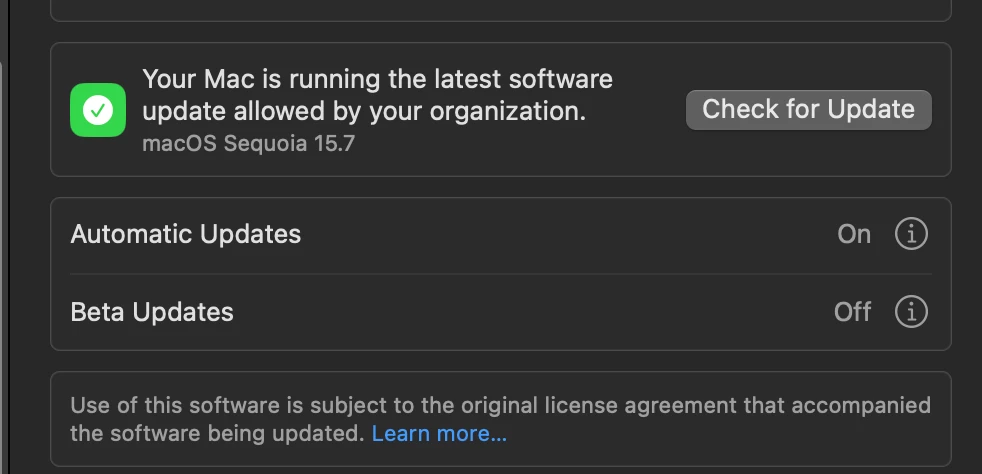
Our school district would like to defer the upcoming macOS 26 upgrade (scheduled for release on September 15) but still allow security updates for macOS Sequoia.
What is the best way to configure this in Jamf Pro so that the major OS upgrade is blocked, while security updates and minor patches for Sequoia remain available? Thanks