Upgraded from Casper 9.62 to 9.65, but started experiencing trouble when running recon via terminal. Anyone else run into this?
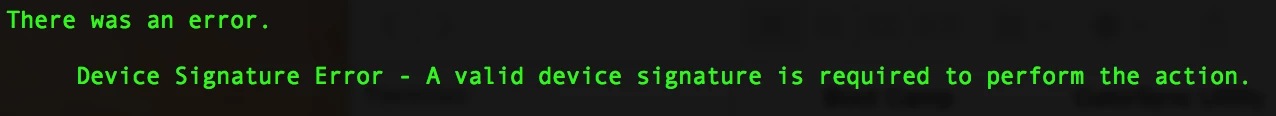
"Device Signature Error - A Valid device signature is required to perform the action.
Upgraded from Casper 9.62 to 9.65, but started experiencing trouble when running recon via terminal. Anyone else run into this?
"Device Signature Error - A Valid device signature is required to perform the action.

Best answer by dferrara
Awesome, it works! Thanks @msample!
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.