Hi All,
We have setup Jamf Pro SSO and Cloud idP for to EntraID.
We then tried to use the EntraID groups for the targeting of applications/configuration profiles but they wouldn’t scope correctly.
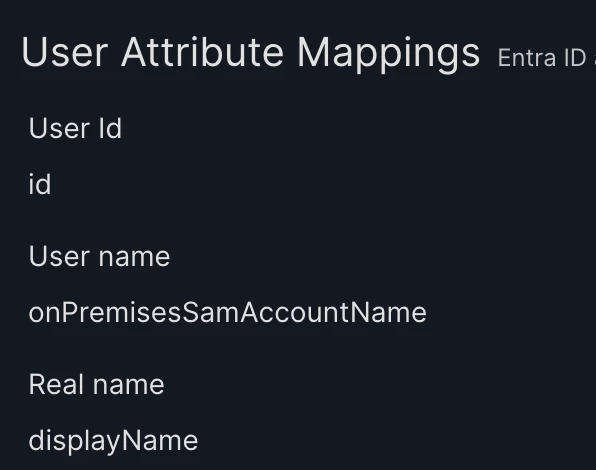
I logged a ticket with jamf support and their theory was that because we map UserPrincipalName (i.e. Full email address), this doesn’t match the username on the local account because it doesn’t support the @ symbol. Their suggestion is to drop anything after the @ symbol on the mapping but it’s not that simple as we use the full UPN for other configurations in Jamf.
So i guess my question is does anyone else have iDP setup with Jamf and do you sync the full UPN and able to target users via EntraID groups?
TIA.