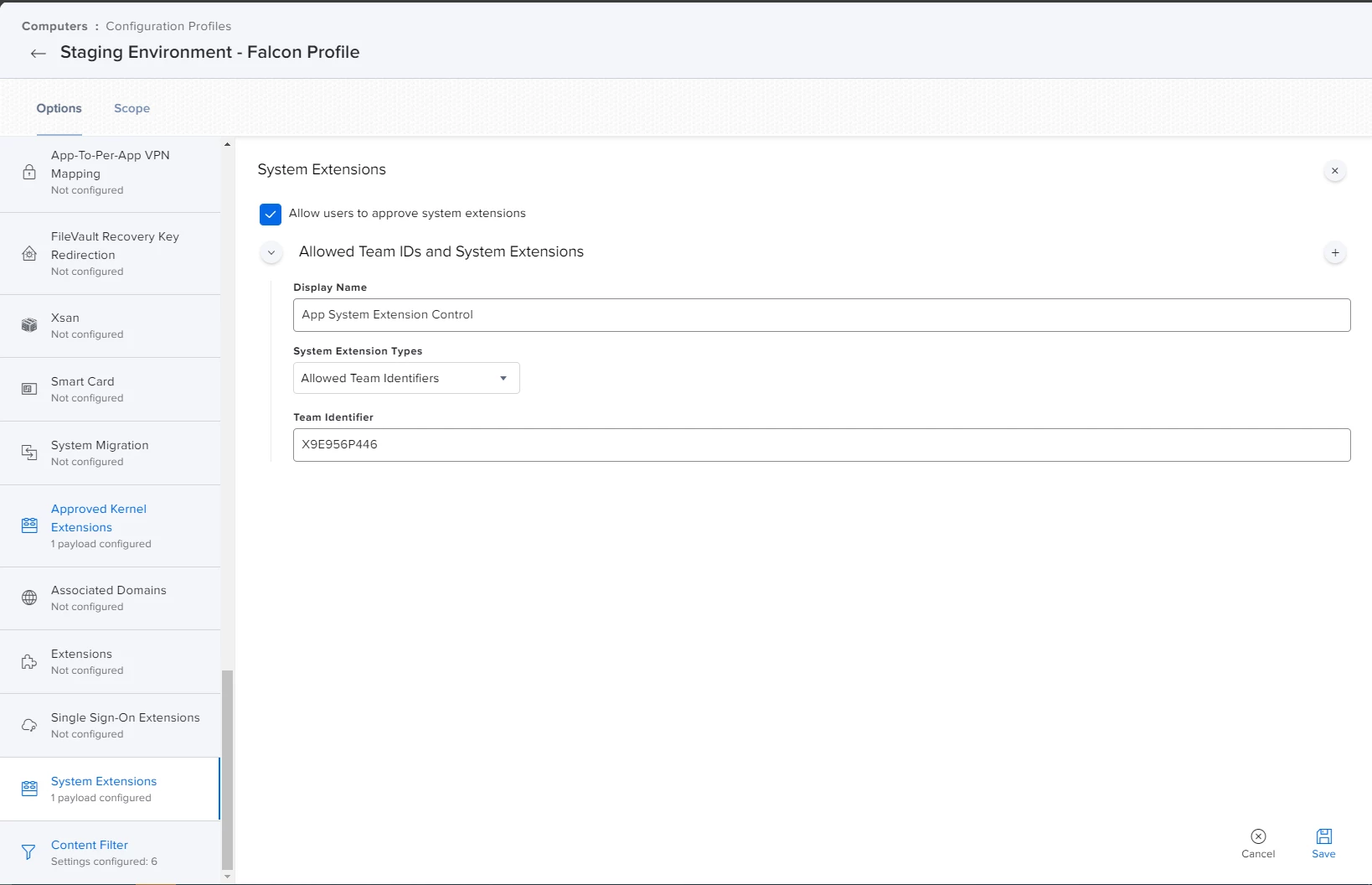
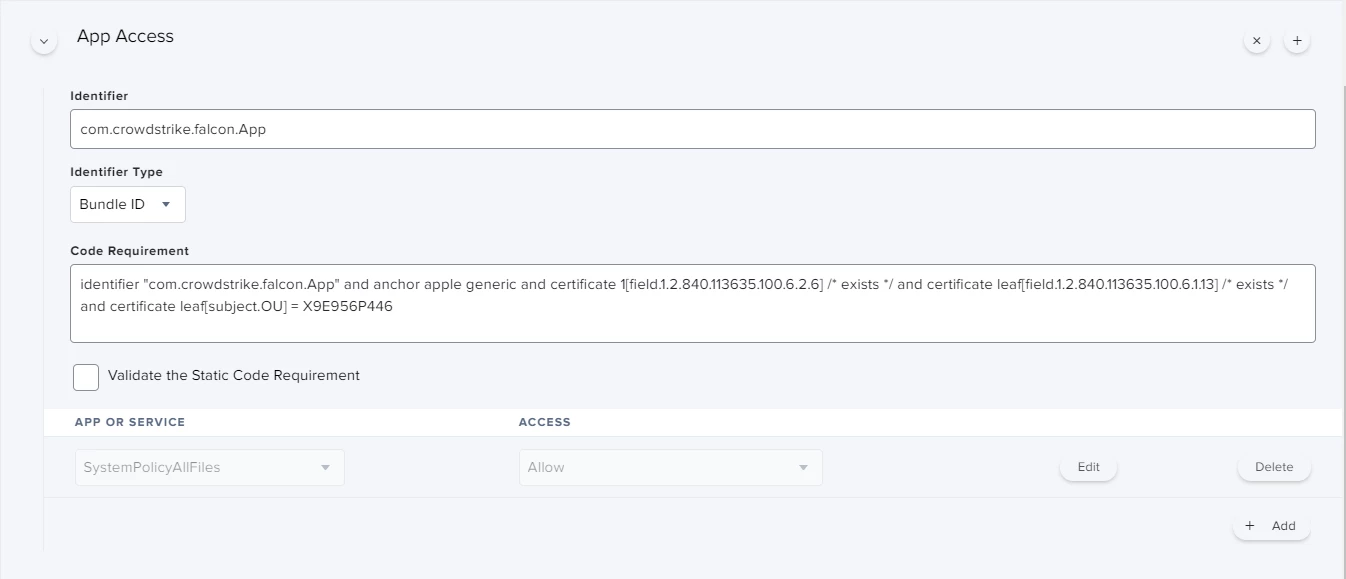
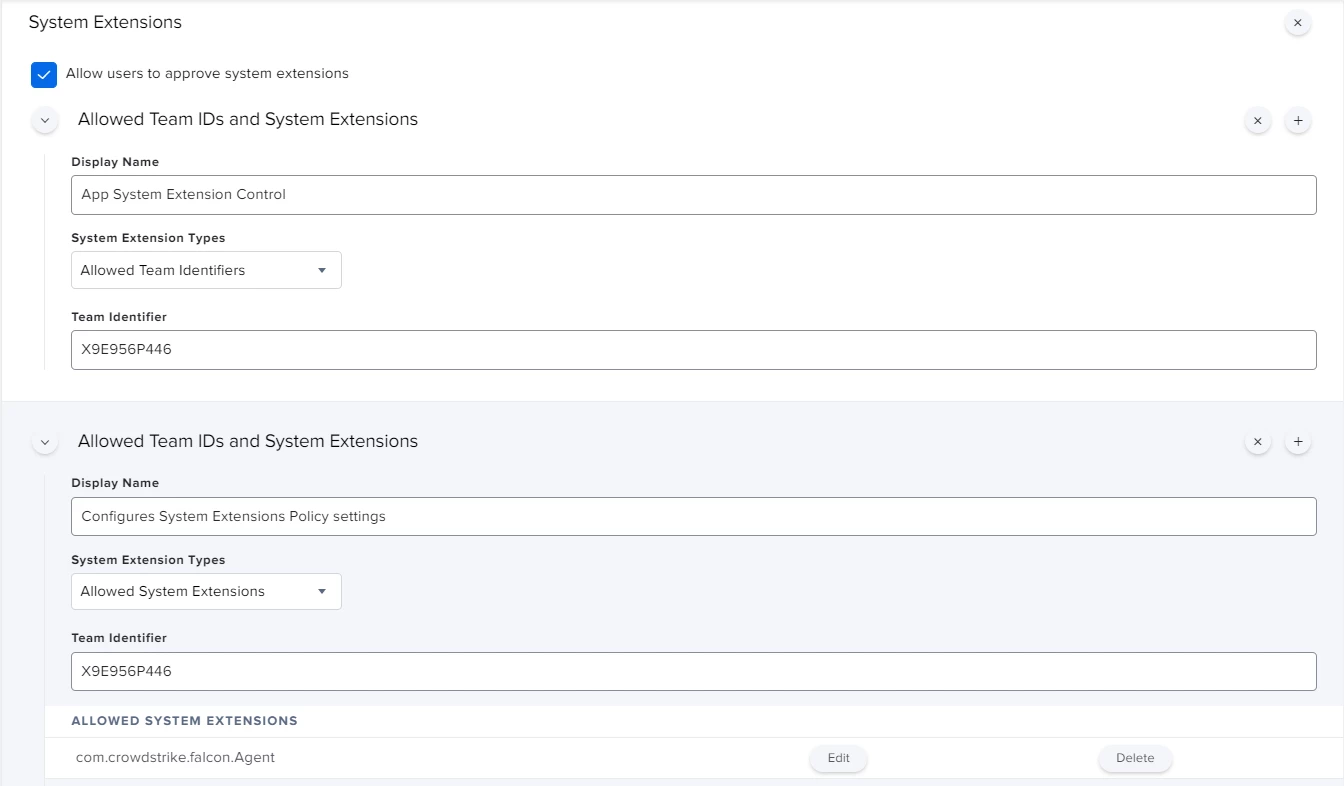
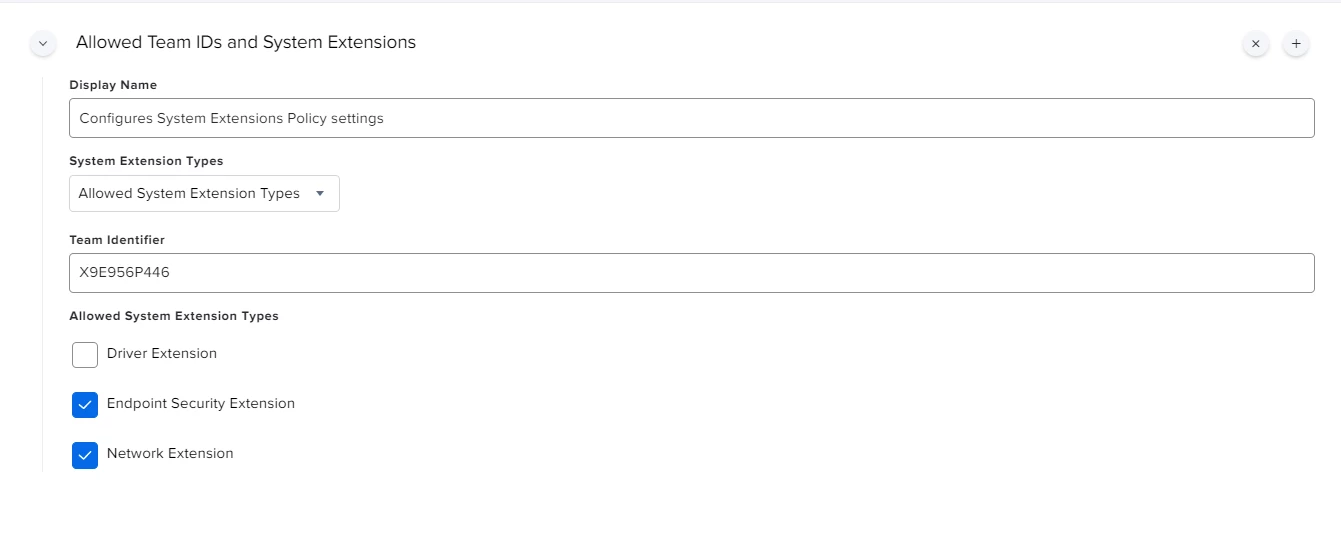
Hi all,
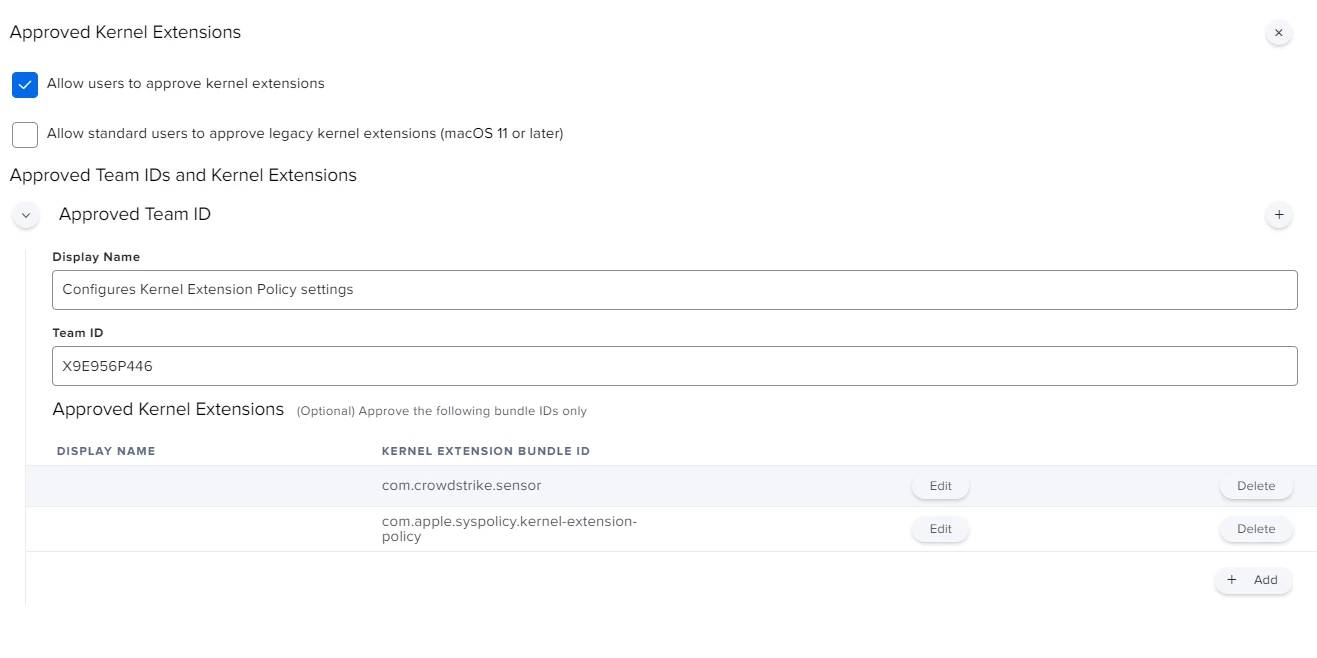
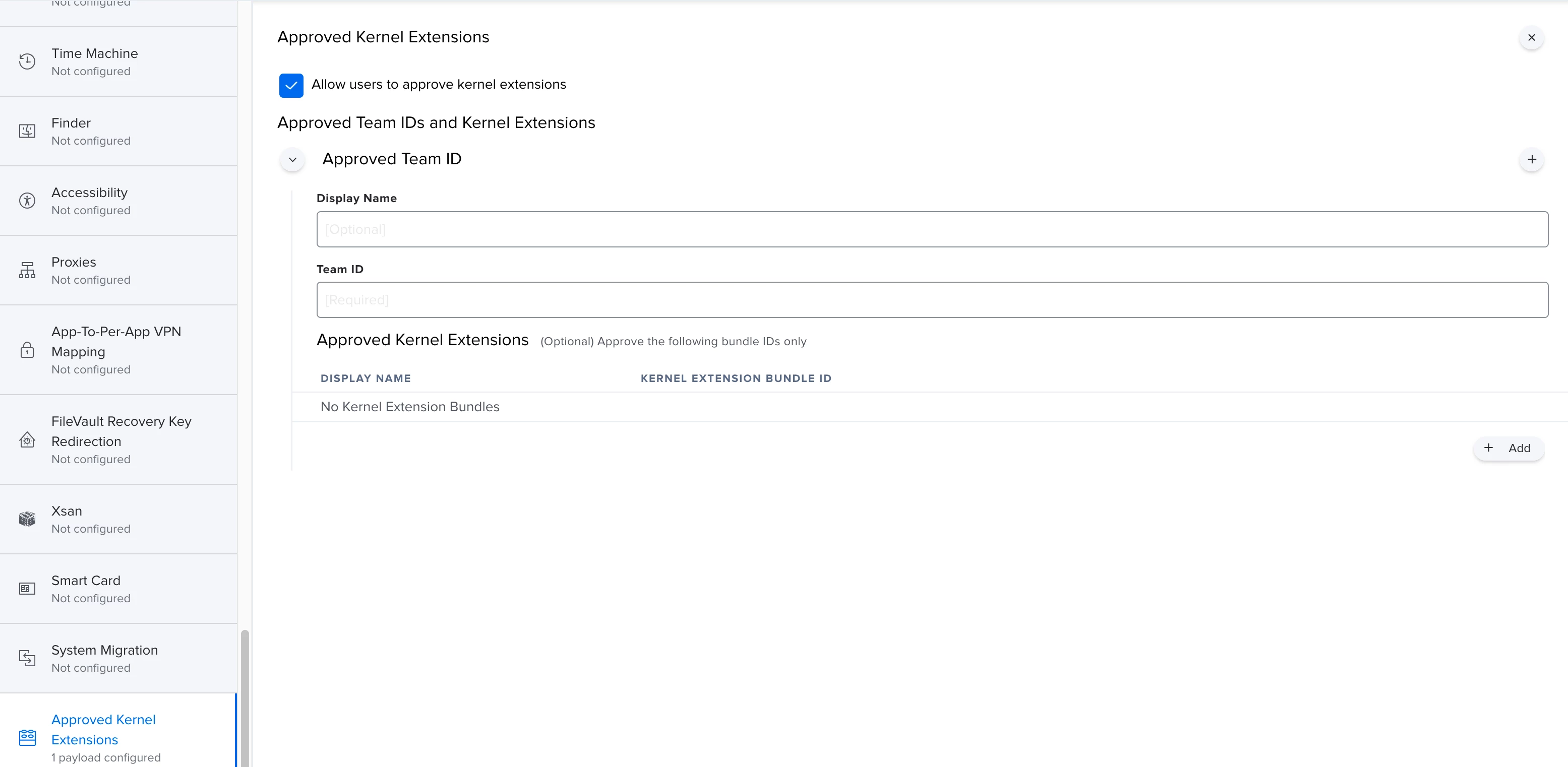
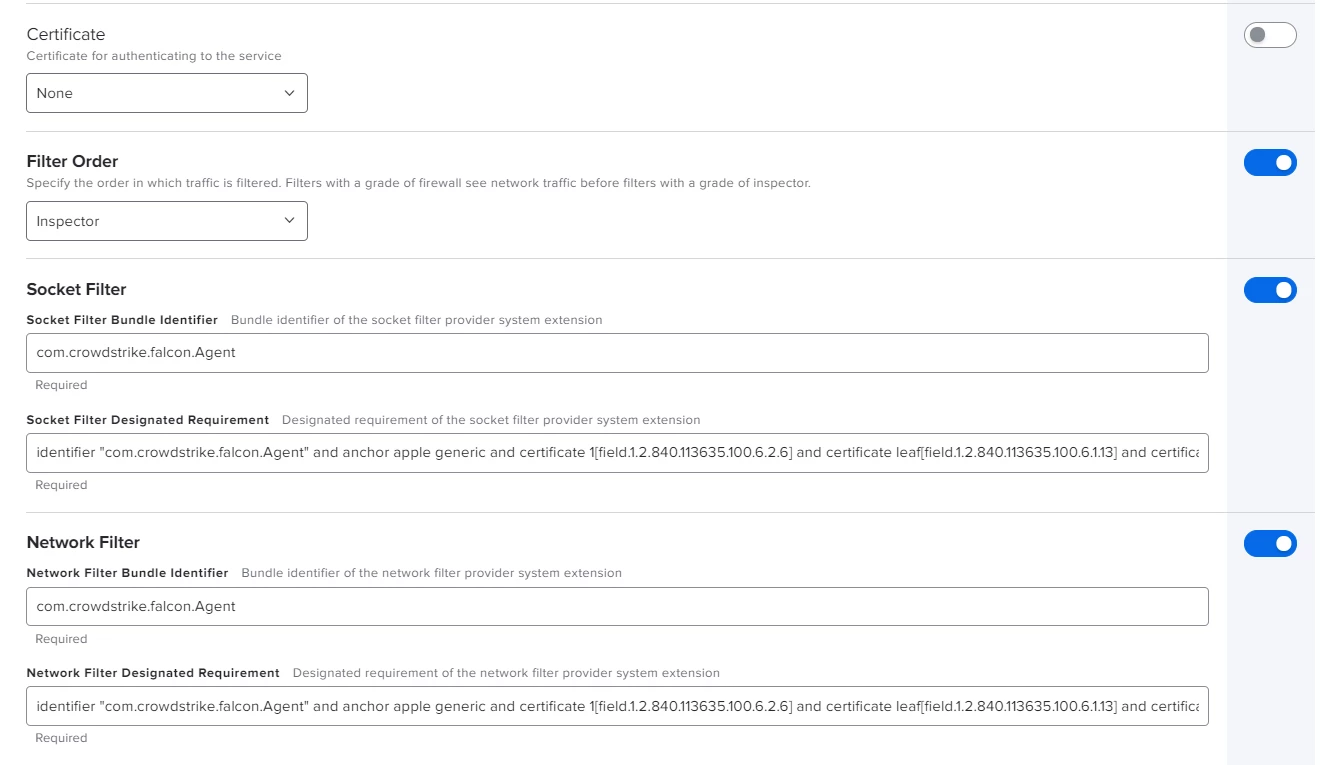
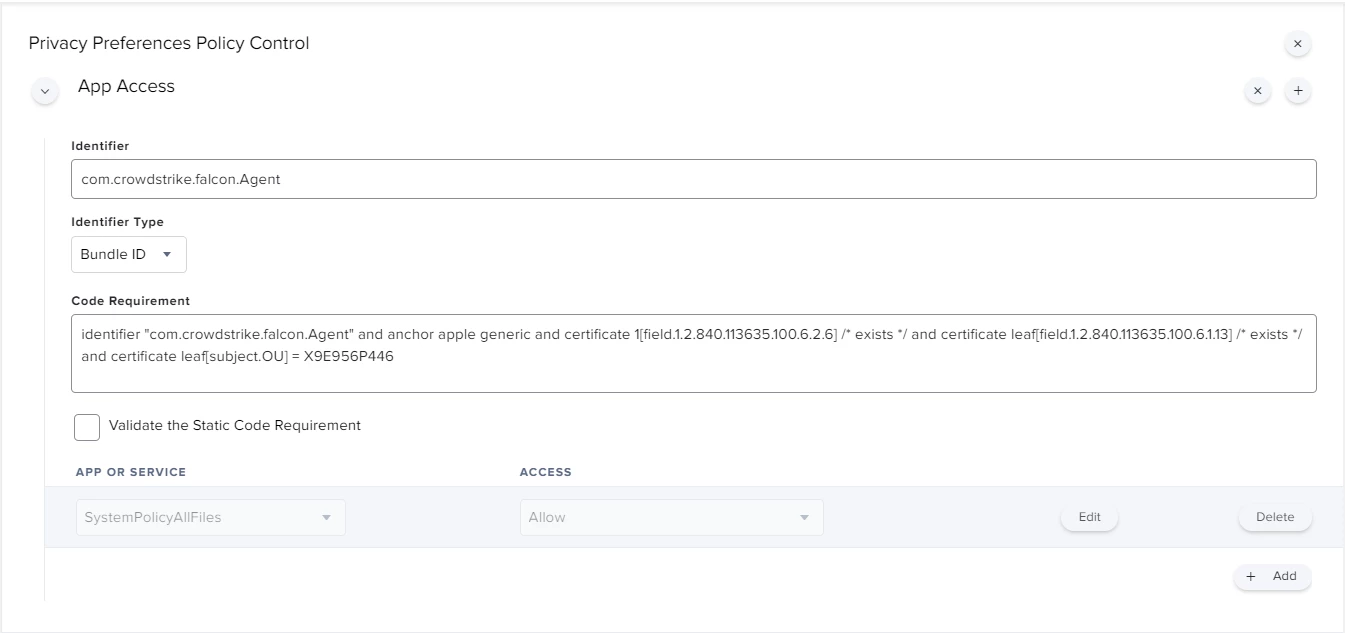
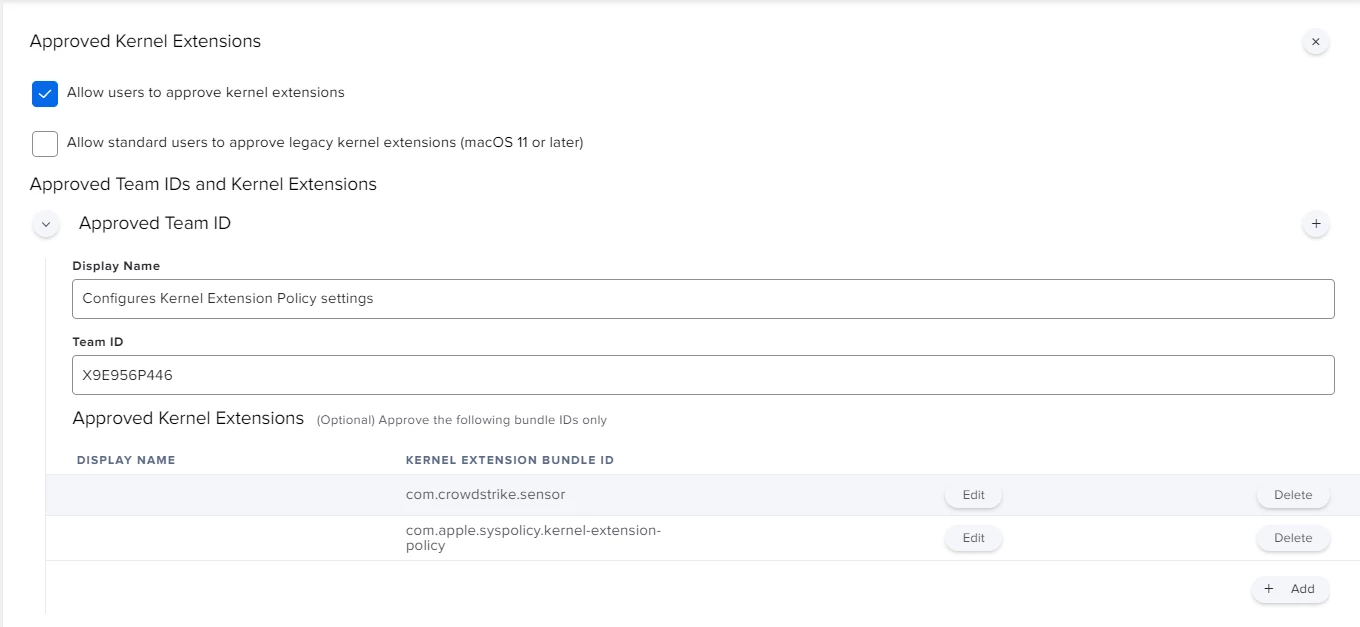
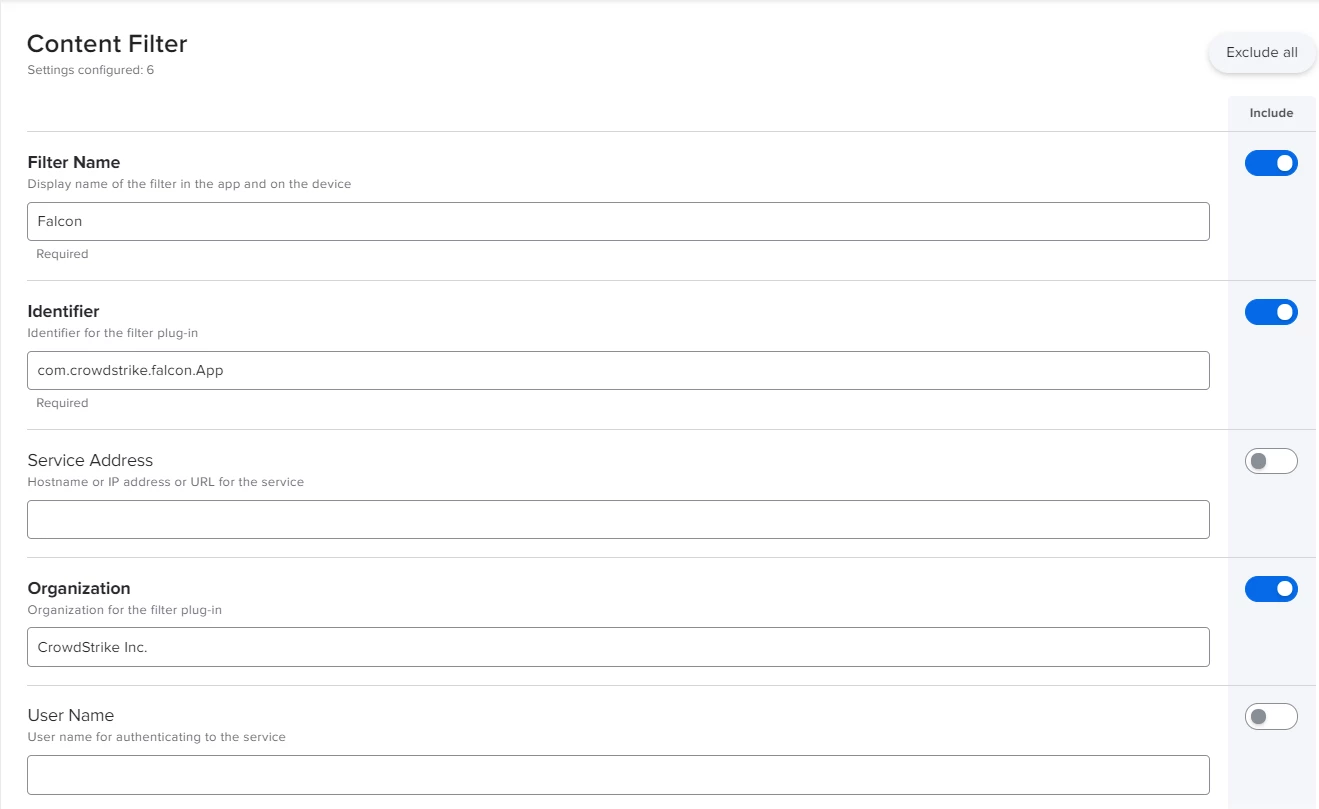
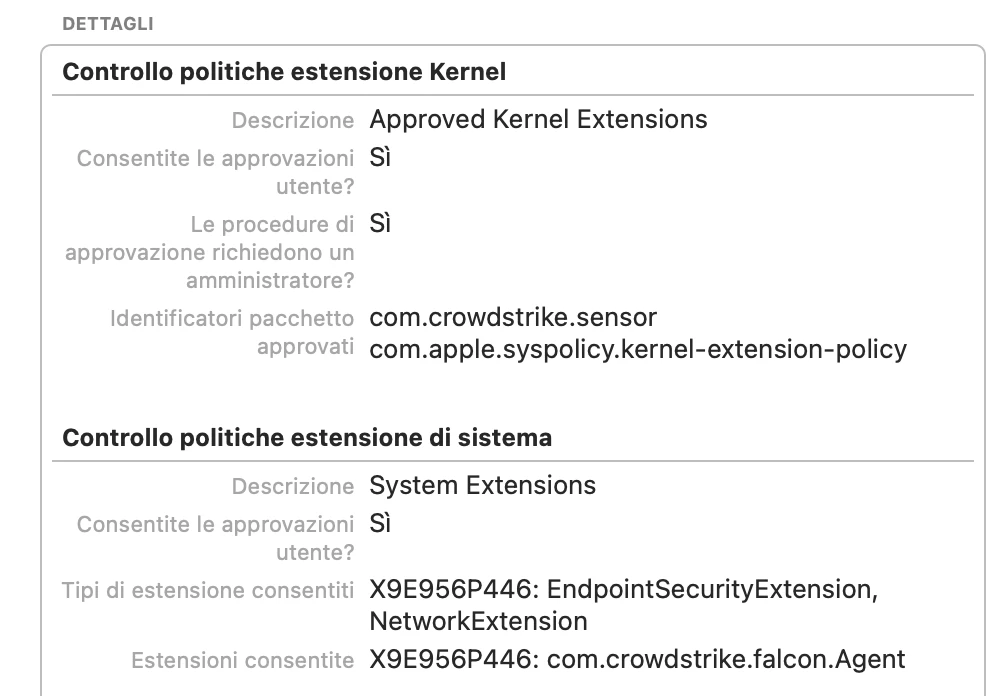
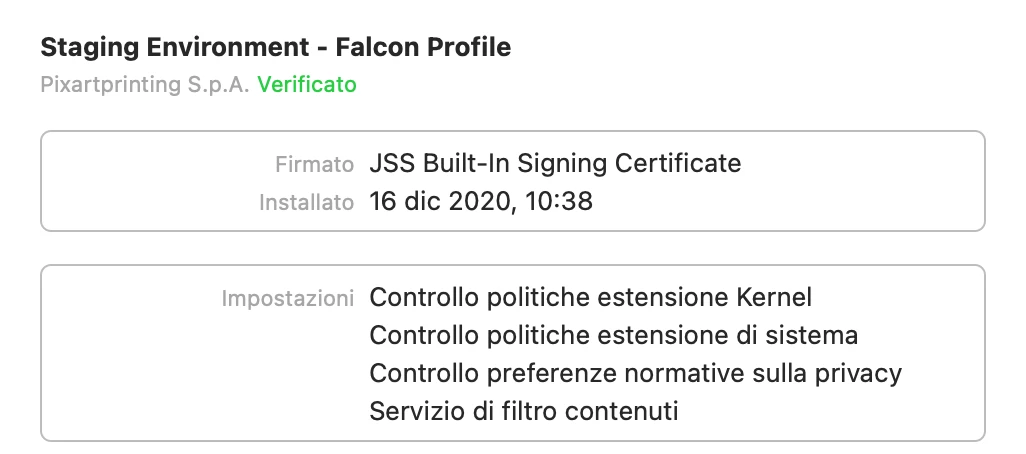
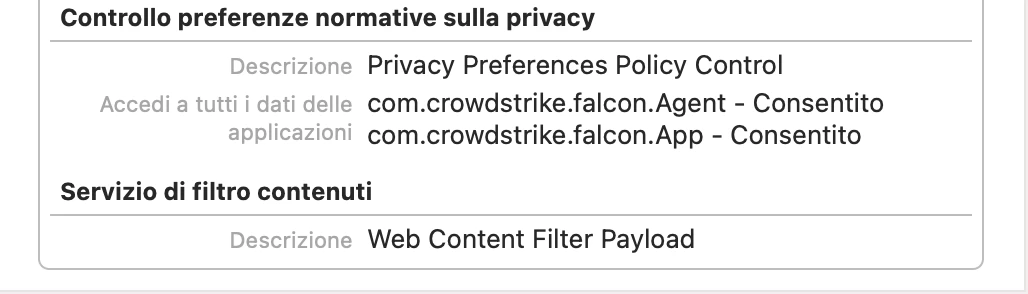
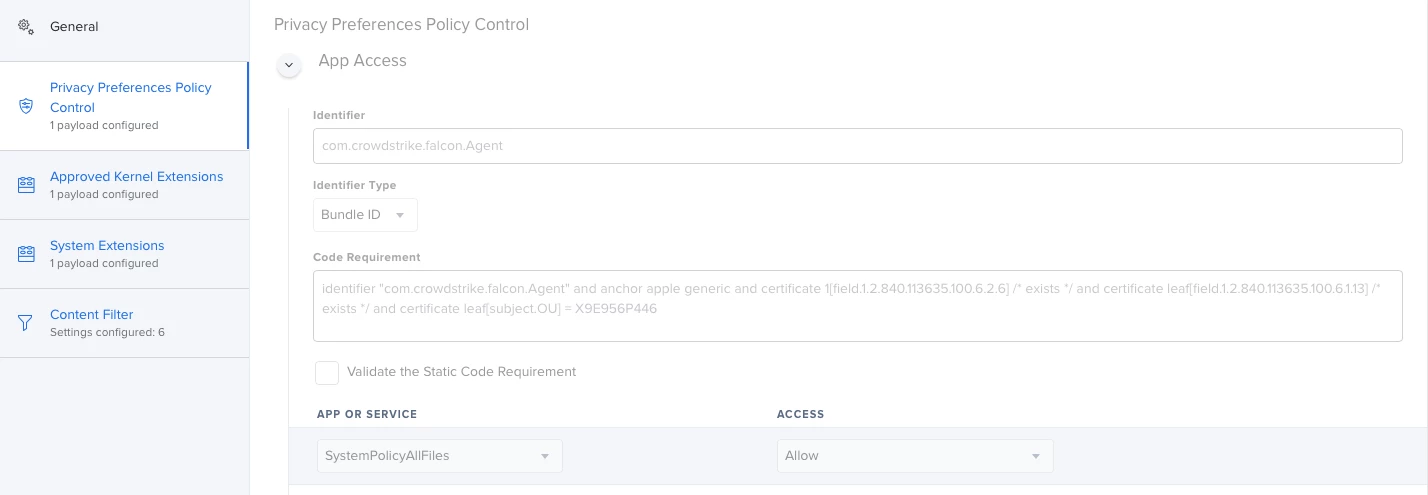
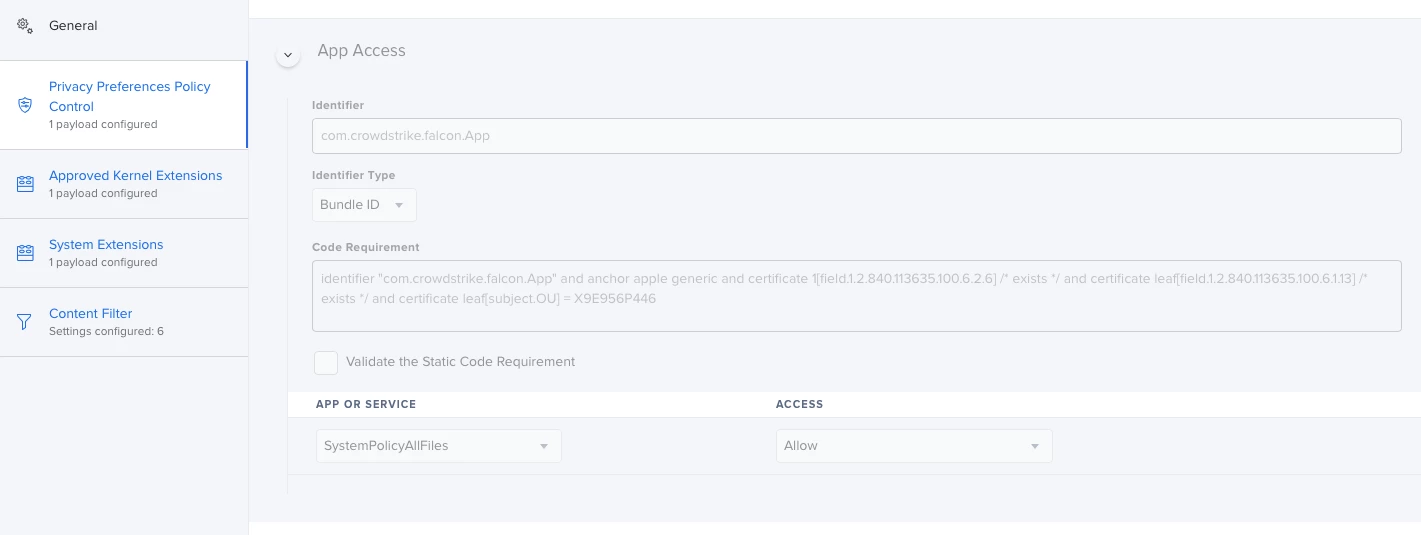
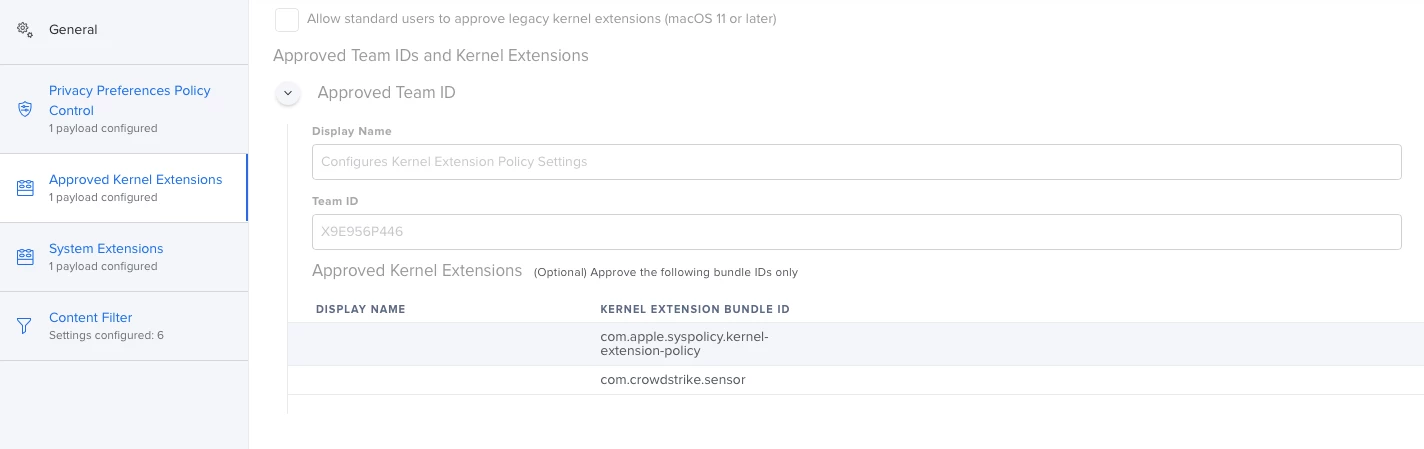
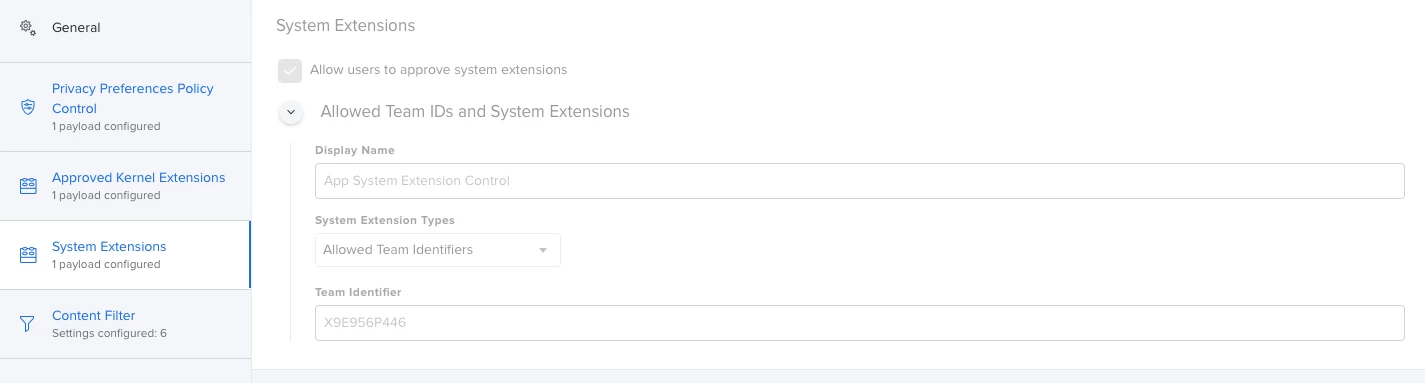
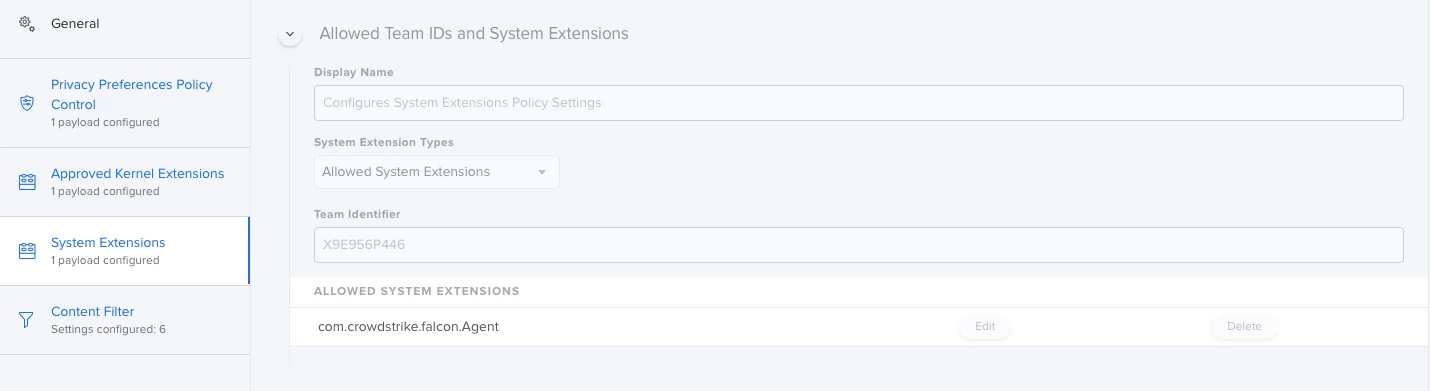
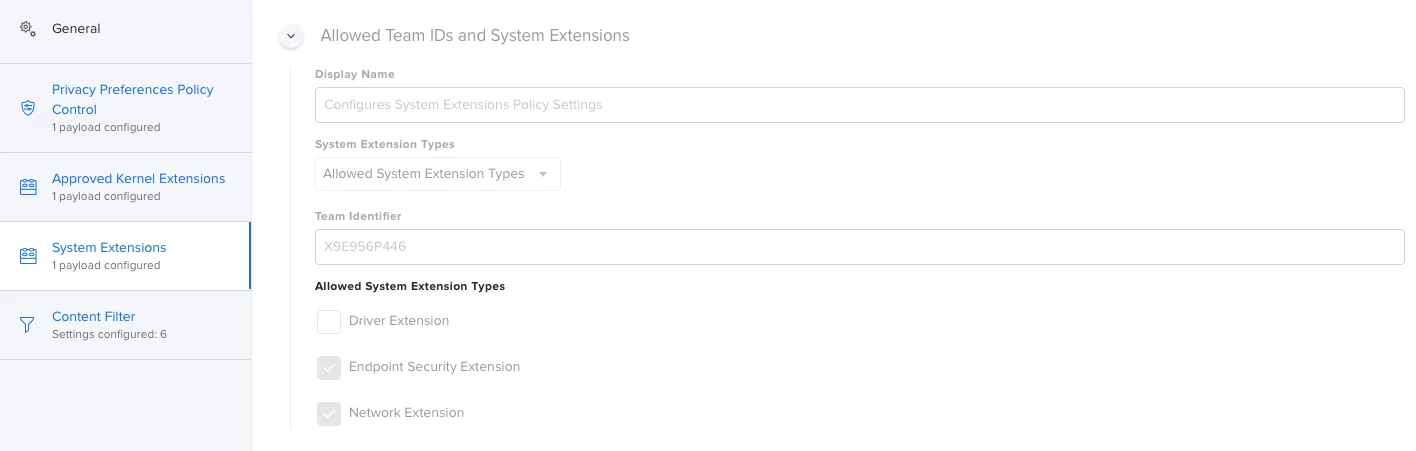
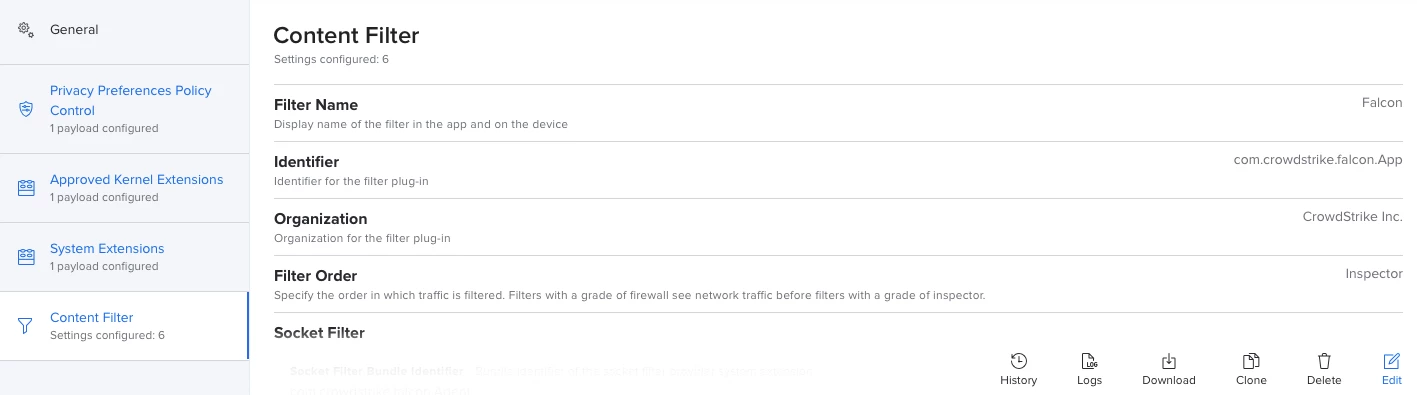
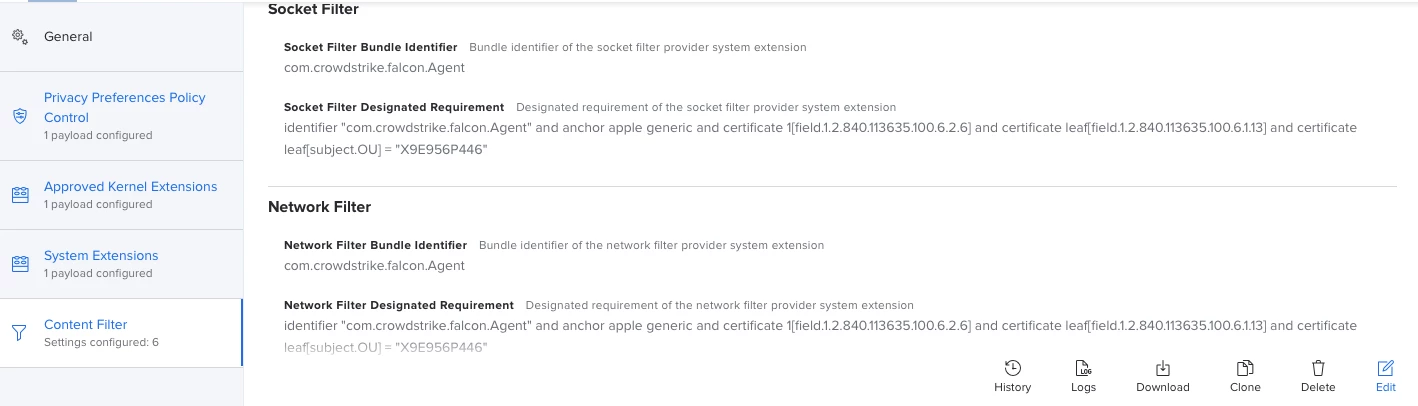
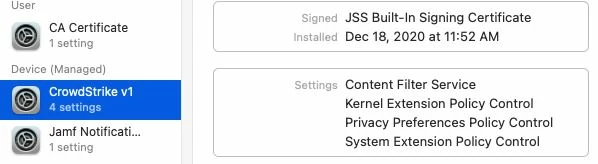
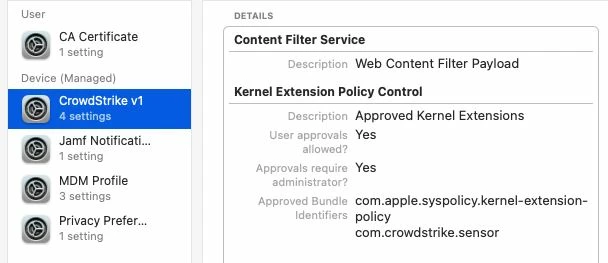
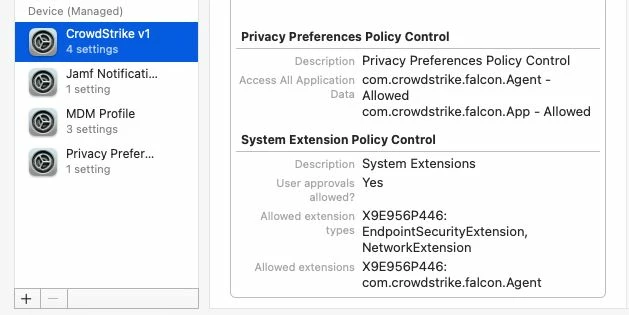
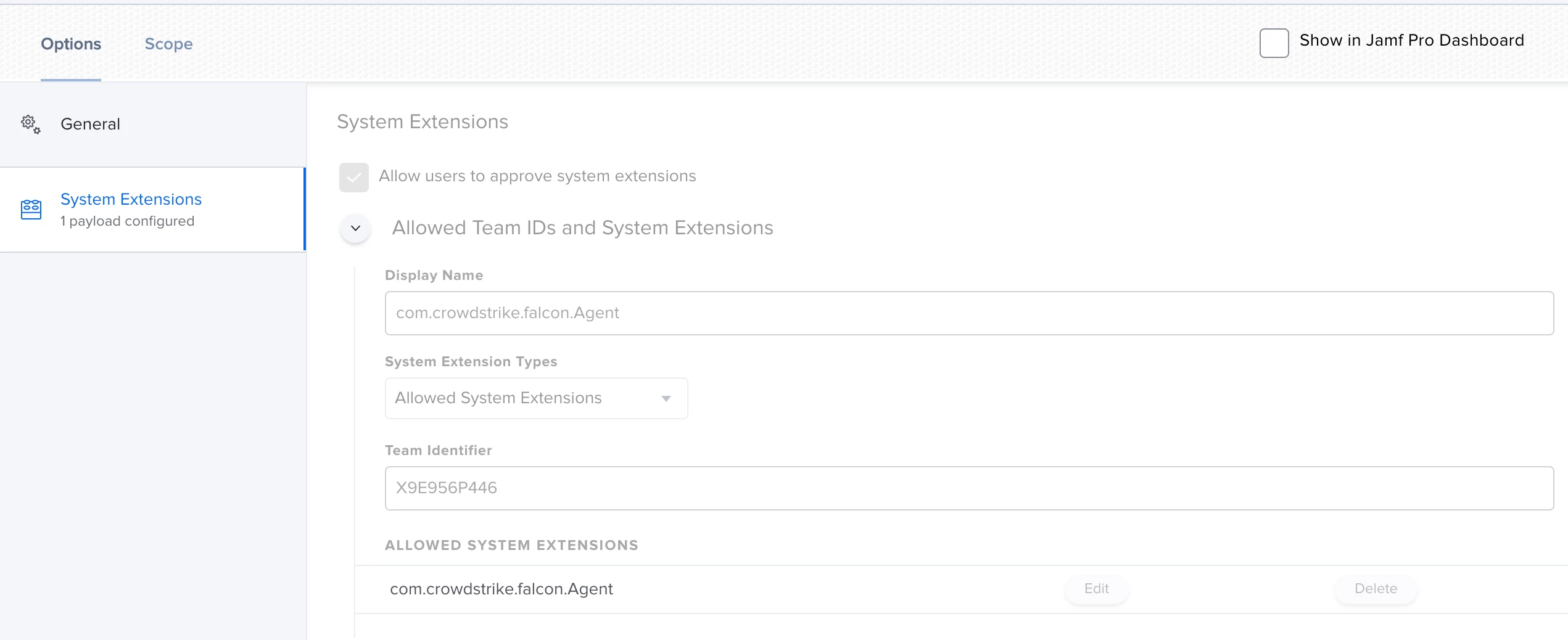
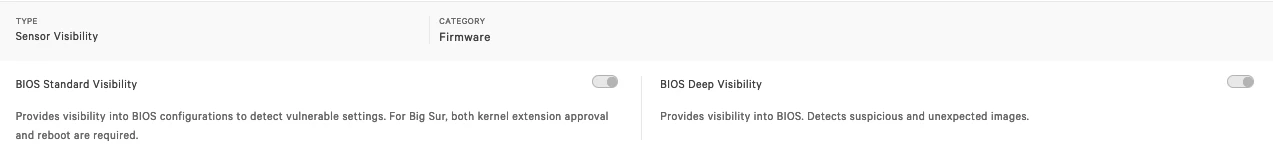
I'm actually using this config profile for pushing system/kernel approval and PPPC control.
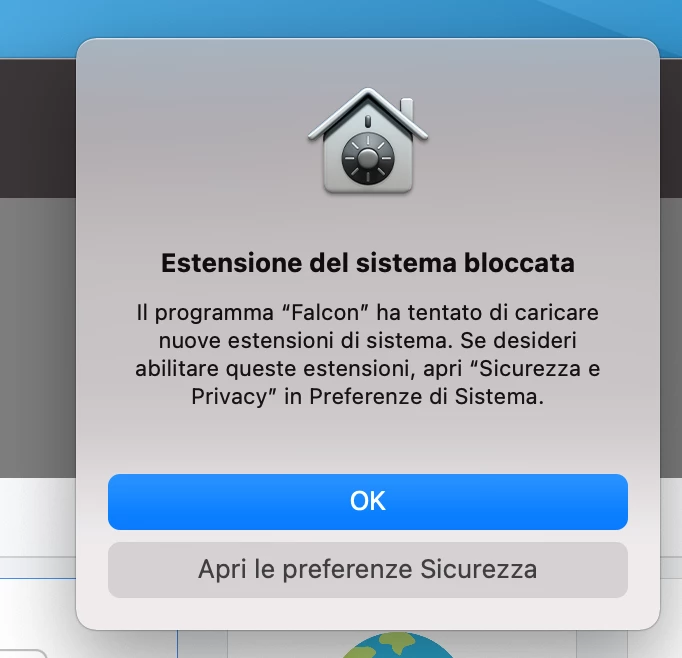
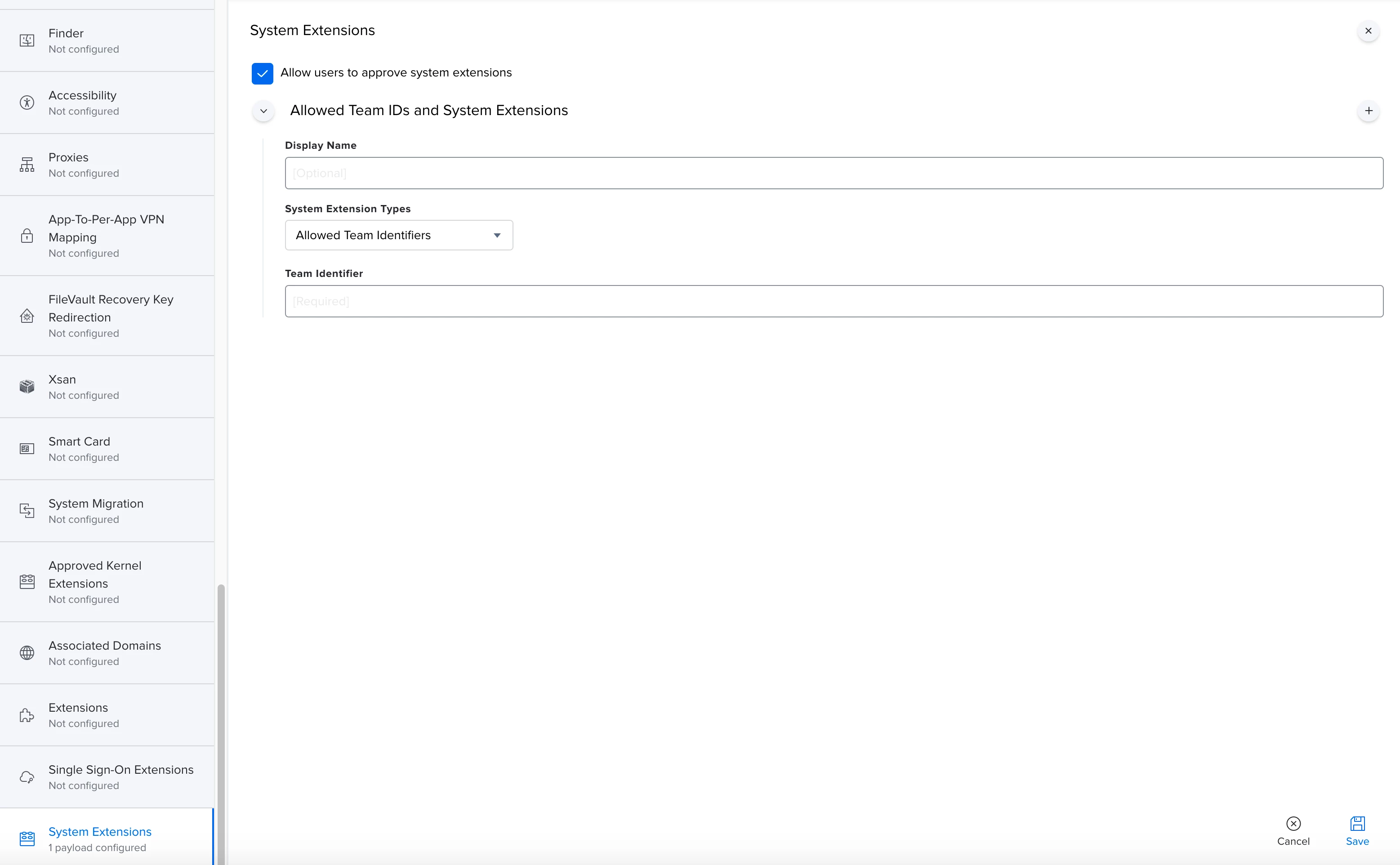
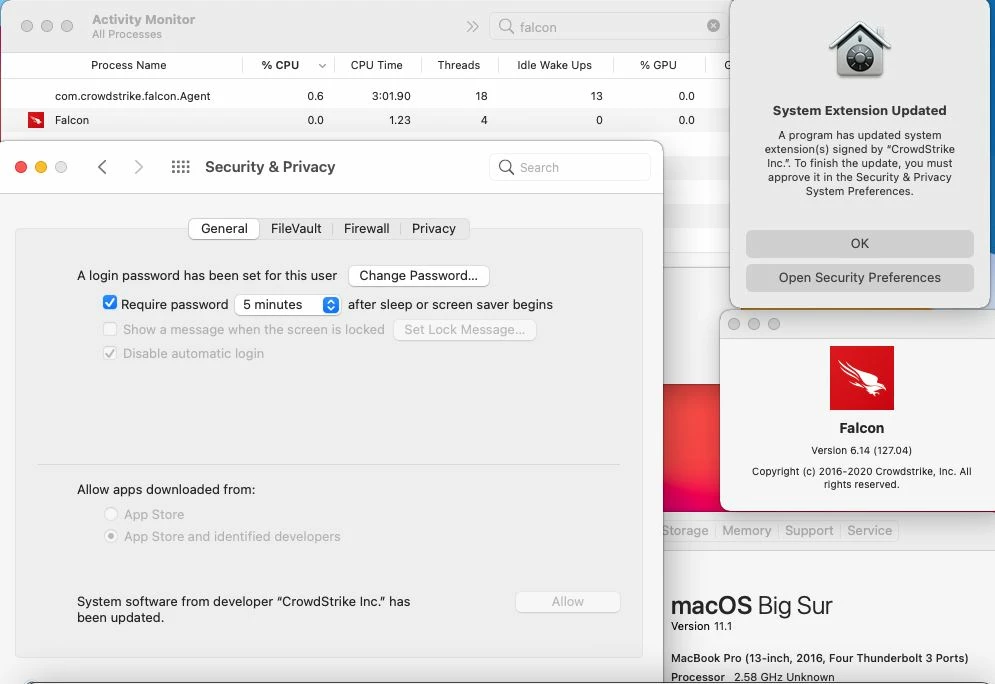
Everything looks to be working except for the "System extension approval", it keeps asking for the approval.
It is actually working in macOS Catalina, but I'm not that lucky for macOS bigSur. Any advice?