Hello Everyone,
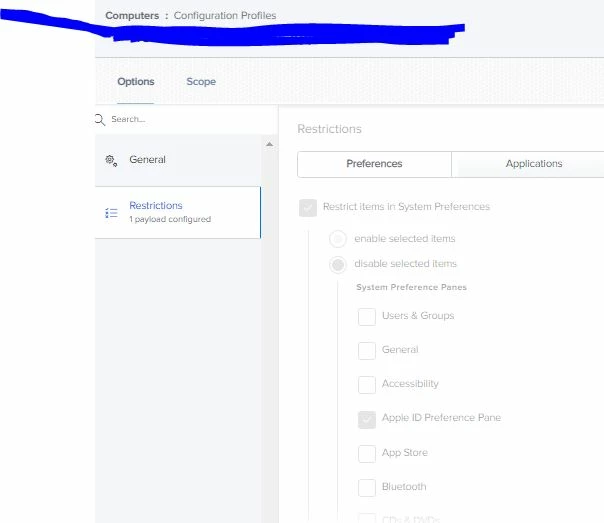
is it possible to forbid the user to log in with his private Apple ID ?
I already found a script to get out which AppleID is logged in but we want to restrict that the User is only allowed to login with the company Apple ID...
Thank in Advance.