Hey!
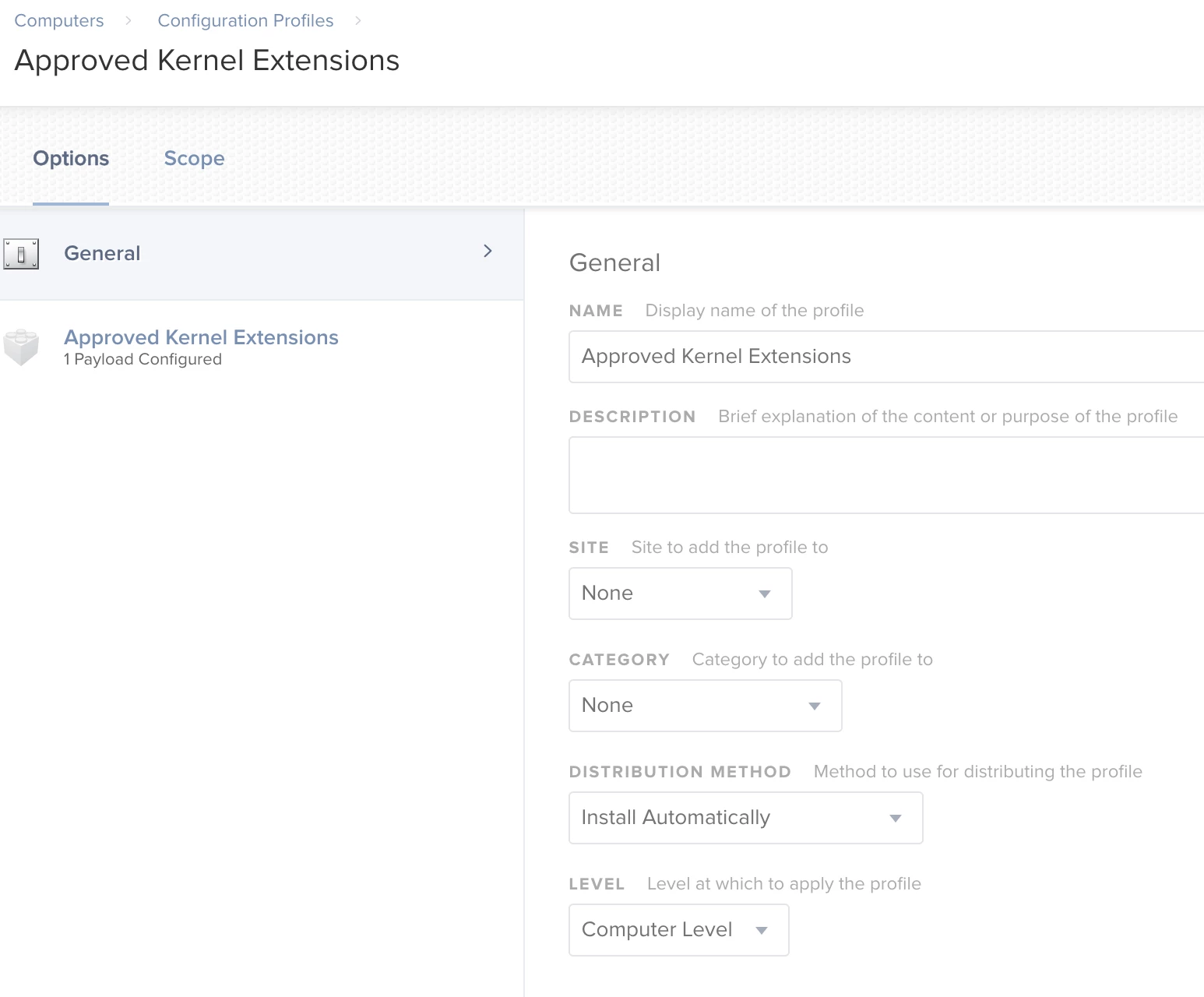
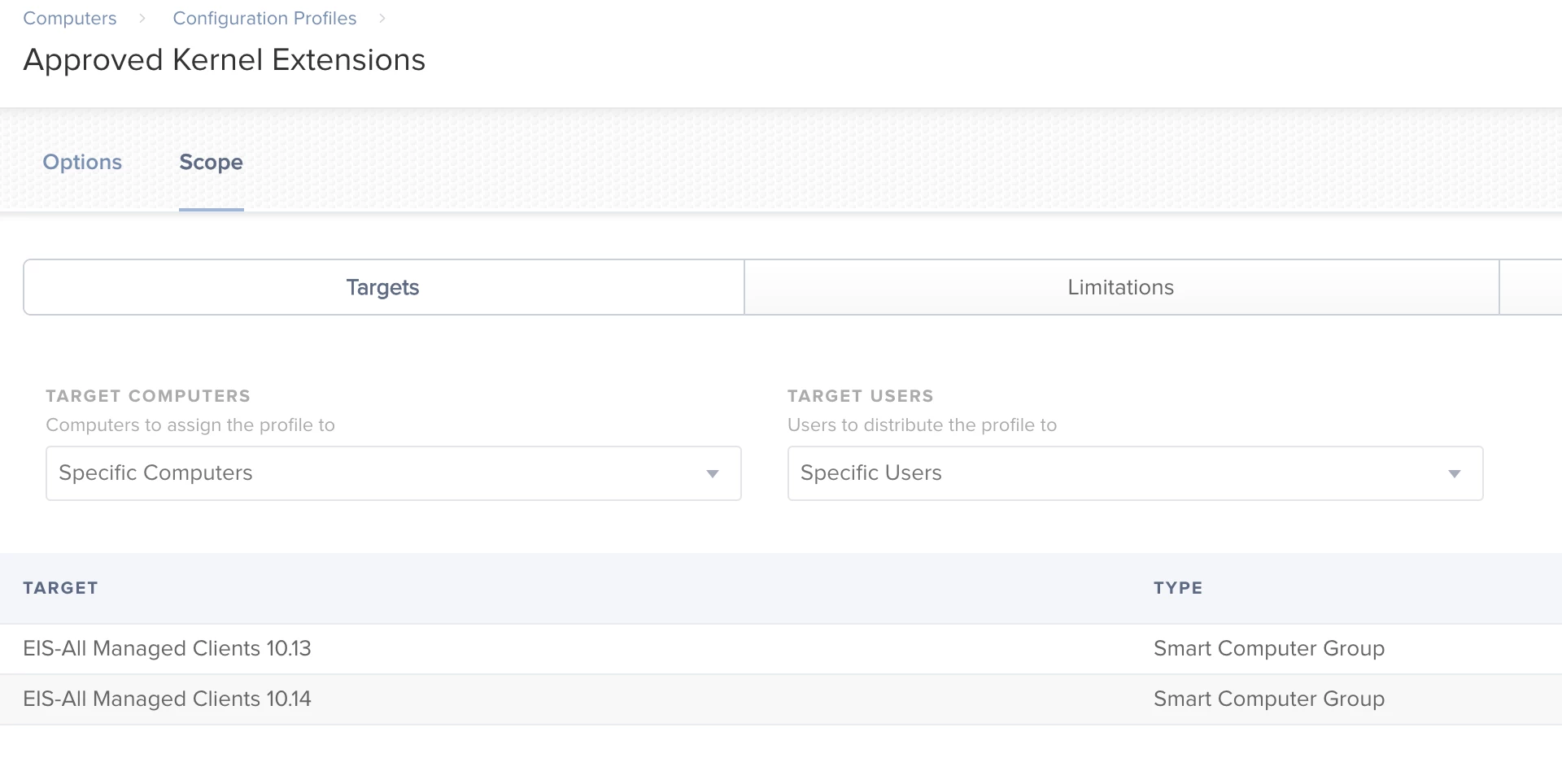
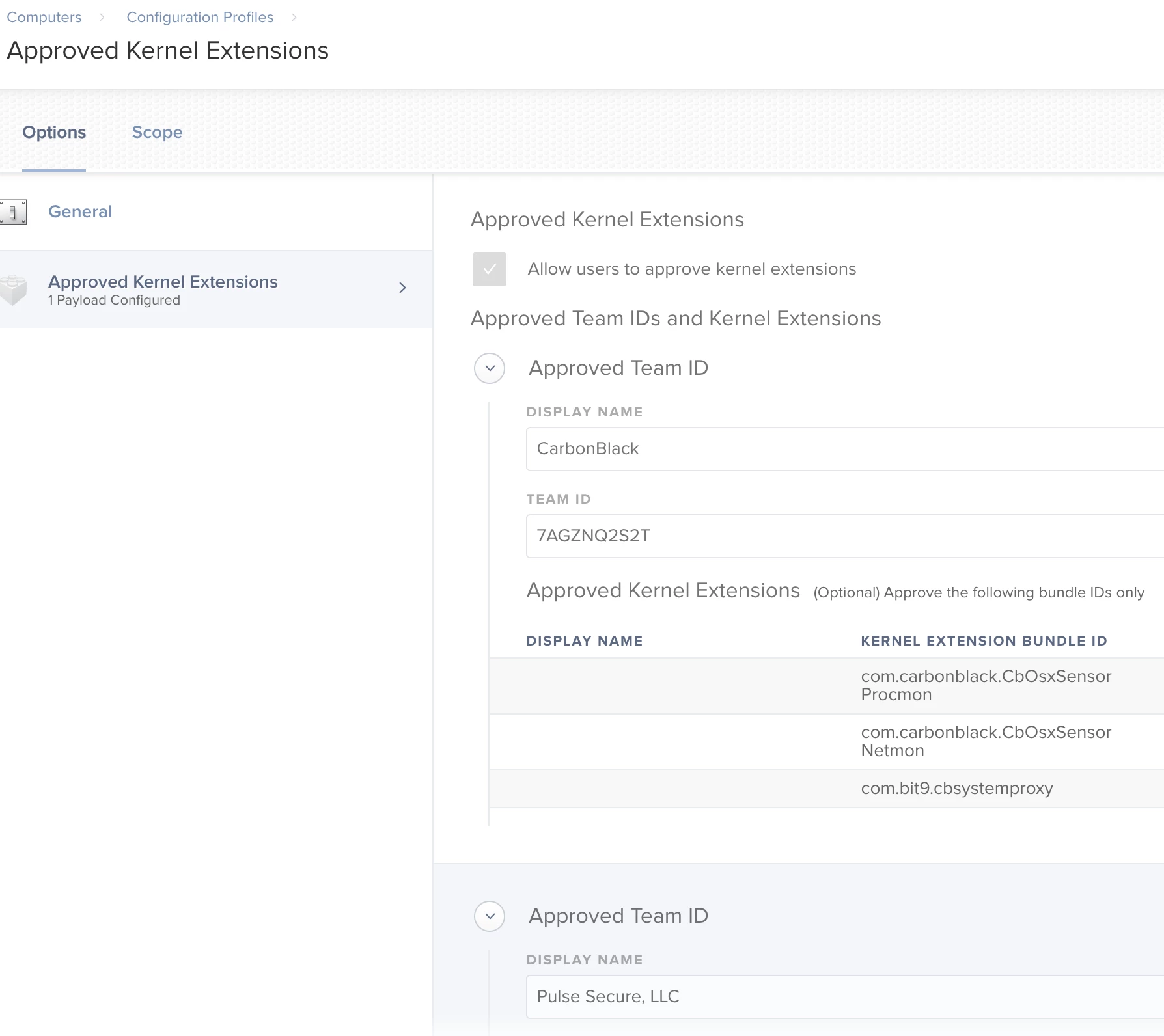
I've been testing the new 10.13.4 update. As we all now, new Kernel extensions need to be either approved by the user or via Configuration Profile.
Along with 10.13.4, we are testing Google File Stream which installs a Kernel extension. I can't find the Team ID anywhere online to whitelist it. Called Gsuite support but the Tier 1 Support didn't even know what I was talking about.
Hoping that someone else has come across with the same issue.