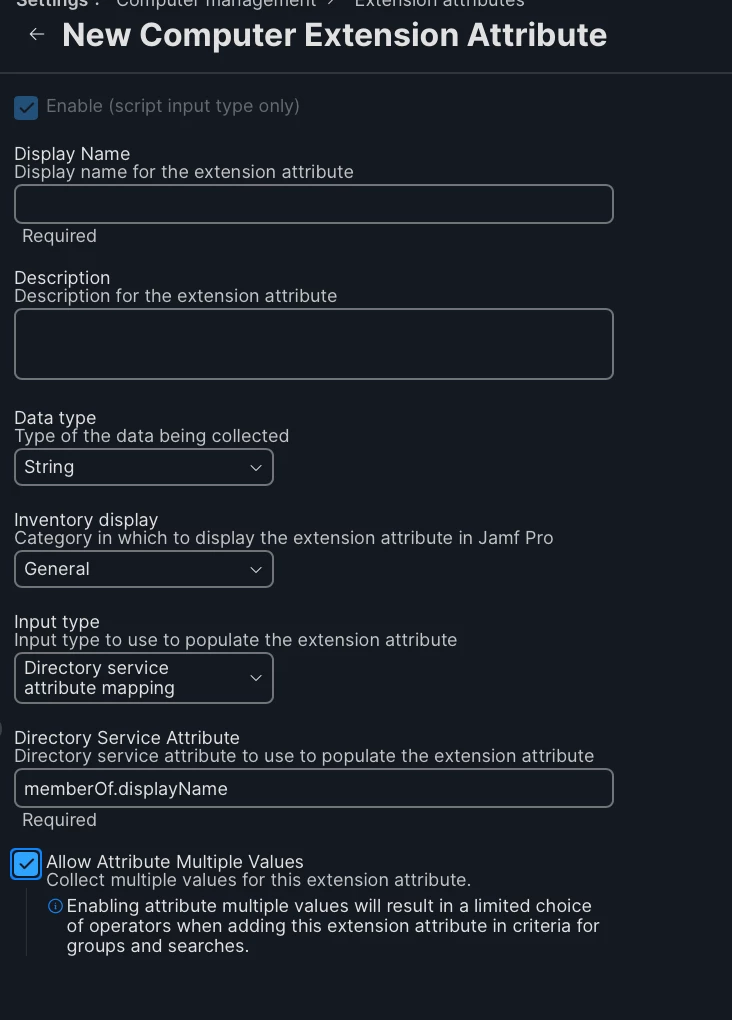
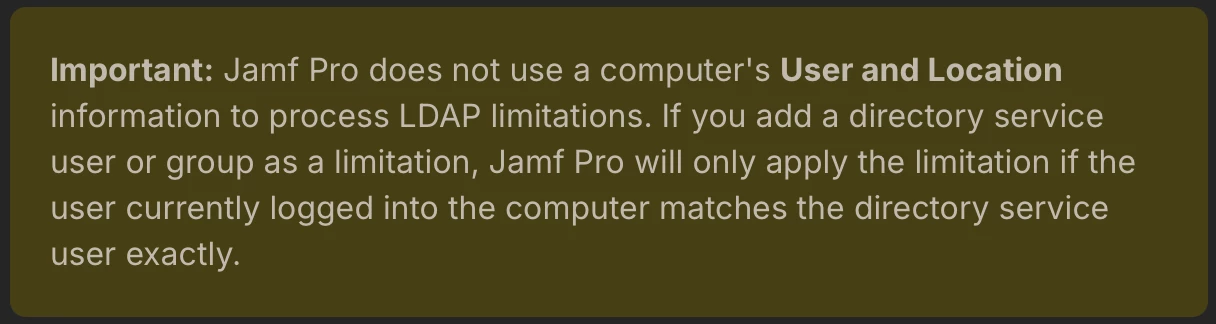
We have some entra integration in our environment. We use connect, have enroll enrollment customizations, etc.
The issue I’m having is while I can see AD groups, it seems jamf can’t see memberships (I’m assuming). When I attempt to scope a policy/config profile to an AD group (scope to everyone, limit to the AD group), it still goes to everyone with no limiting. I’m sure there’s a setting I’m missing. Has anyone seen this?