Before the M1 Mac's we used the softwareupdate command line tool to download and install updates - and force a restart after a 48 hour deadline has passed.
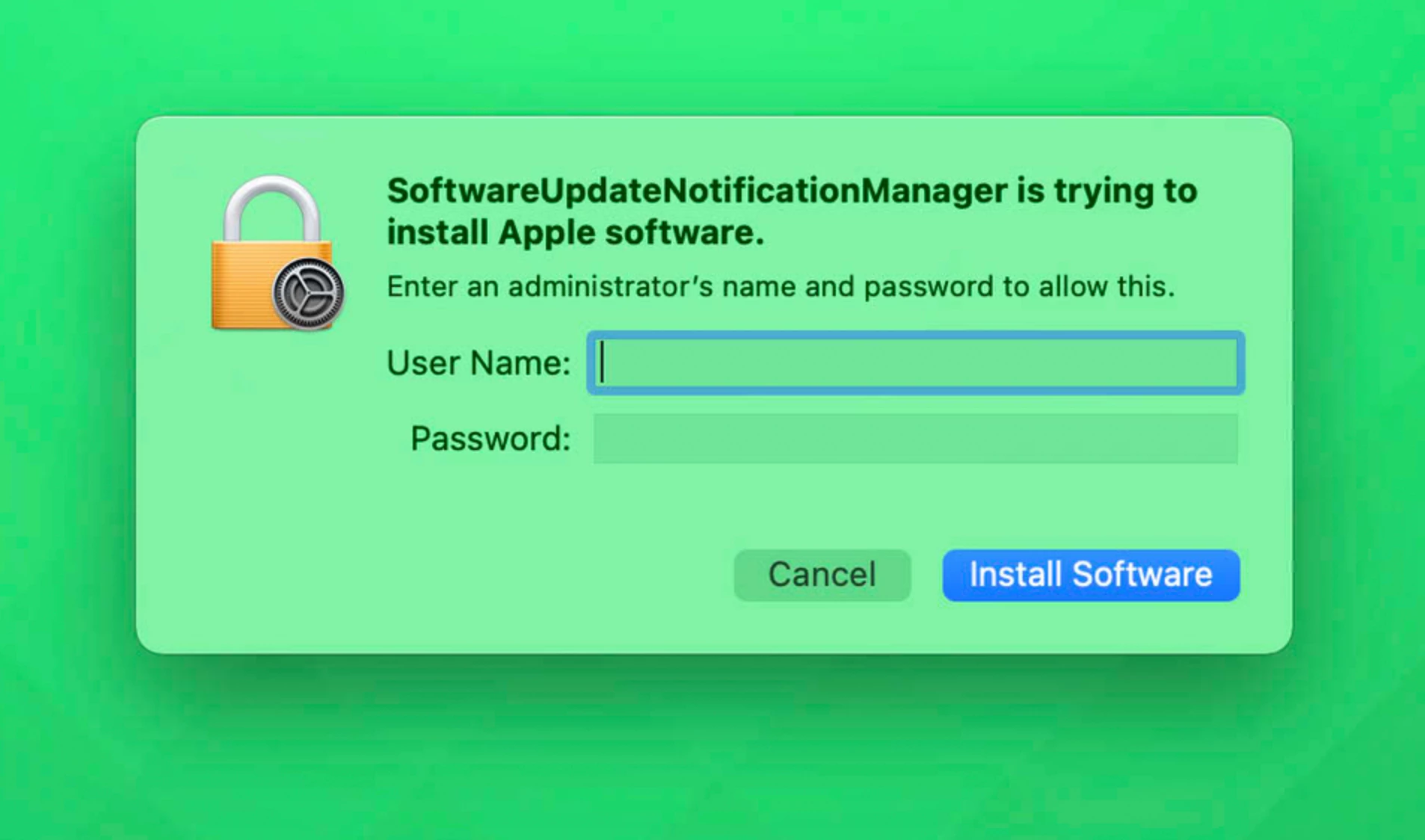
On M1 Mac's with Big Sur this fails because softwareupdate now needs a user password in the middle of the upgrade. No amount of sudoing will help.
Then we have the "Download and install software updates" management command, which:
- Cannot be issued as a policy
- Cannot be deferred
- Cannot be scheduled
and worst:
- Still needs the user to enter the password! Simply clicking cancel fails the updates :(
What are we supposed to do now? Our security team is not happy that our brand new mac's are potentially running insecure versions of macOS indefinitely - especially after we just taught everyone that security updates will be automatically installed within 48 hours.