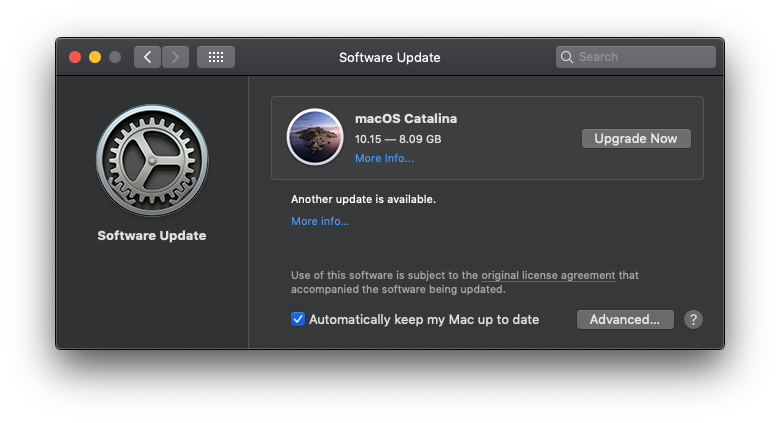
Lots of discussion in #catalina on the MacAdmins Slack on how to disable the above prompt. Turns out even though Catalina isn't a traditional software update, it does still exist as a software update catalog entry and can be ignored in the same way. Run this command to ignore on a single machine...
sudo softwareupdate --ignore "macOS Catalina"
The Catalina banner in Software Update should disappear almost immediately. To send that out to your entire fleet with Jamf Pro, create a new policy with Files and Processes. Under execute command add that command. Scope to whichever Macs you don't want to be prompted. Problem solved! Thanks to folks on MacAdmins Slack for working through this.
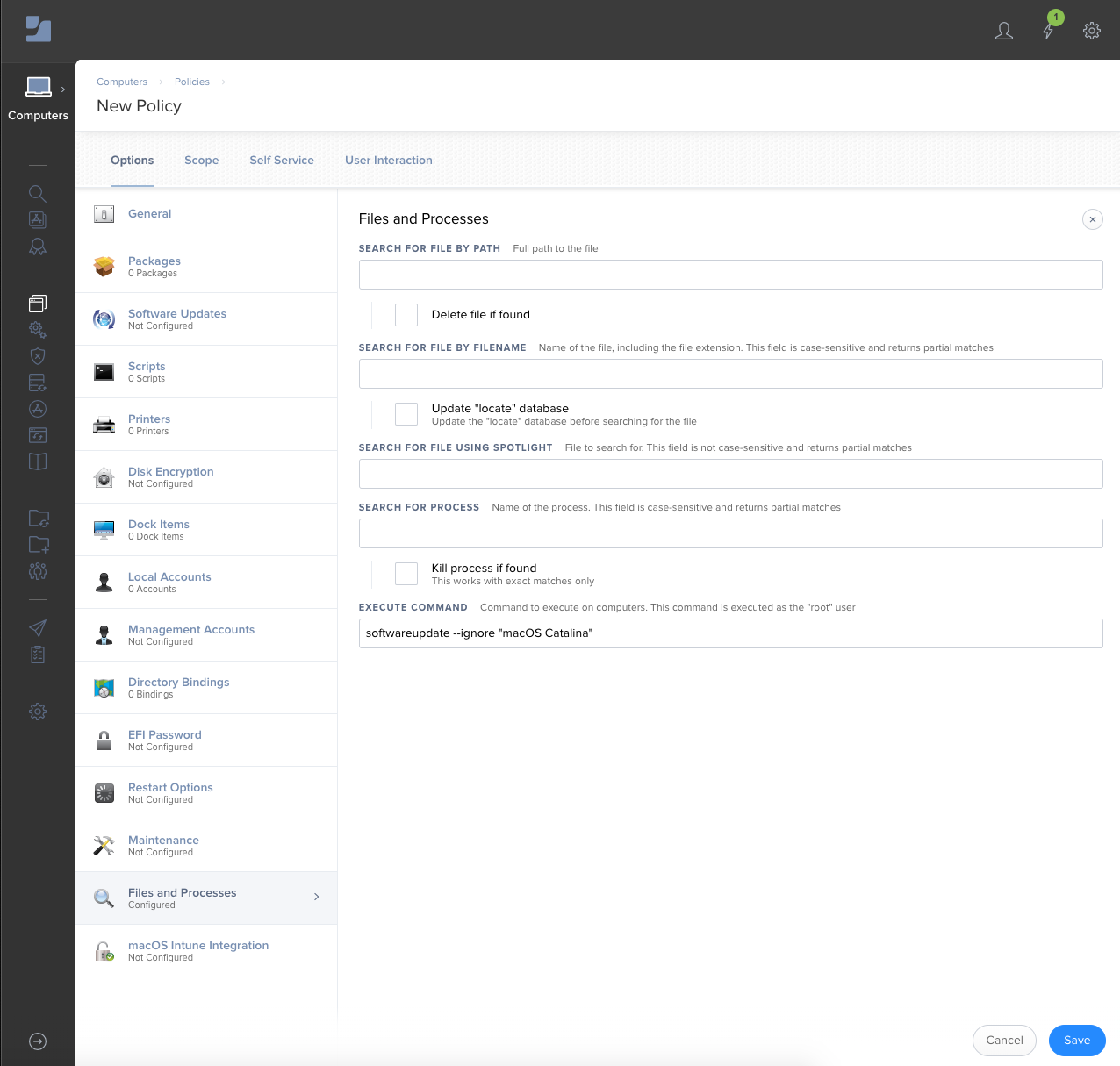
To undo what you just did and remove ignored software update entries run...
sudo softwareupdate --reset-ignored
To collect inventory information on what Macs have this ignore software update in place I have an EA. Tested on High Sierra, Mojave, and Catalina. Returns a list of ignored software updates added with the --ignore command. Useful to run advanced searches or smart groups against as needed.
https://github.com/nstrauss/jamf-extension-attributes/blob/master/ignored_softwareupdates.py











