We recently purchased Okta, and I thought it would be great to get Okta talking to JAMF Pro. We have a hosted JSS, so we cannot connect it to AD (don't want to open up ports to an internal server) so I thought this would be the perfect way to allow users to sign into Self Service, and Admins for the JSS, without having to add all the users manually into the JSS.
I followed the instructions provided by both Okta and JAMF, and still was unable to get it to work. After a lot of trial and error, I was able to get it working properly. So, I thought I would write about it and share the tricks needed for configuration with everyone in JAMF Nation, as I am sure there are others running in to these same issues.
Here are the steps:
Create your Group(s)
In order to get the JSS to recognize users in Okta that are NOT in the JSS, you need to create a matching group IN BOTH PLACES.
1. Create an Okta group called "jamf-users" (or whatever you want)
2. Create a group in the JSS with the IDENTICAL name: "jamf-users". CASE-SENSITIVE!
NOTE: You can create different groups in the JSS with different levels of JSS permissions. As long as there are matching groups in Okta, members of the Okta groups will have those permissions to the JSS.
Configure JSS for SSO and Okta for JSS
- Create a new SAML Template application in Okta by clicking Add Application, then "Create New App"
- Choose SAML 2.0
- Give your app a name and icon, and click Next.
- For your Single Sign On URL, enter:
https://<jss_address>/saml/SSO - The Audience URI (SP Entity ID) should be
https://<jss_address>/saml/metadata - Leave Name ID format as
Unspecified - Application Username should be whatever you want, I usually go with Okta prefix
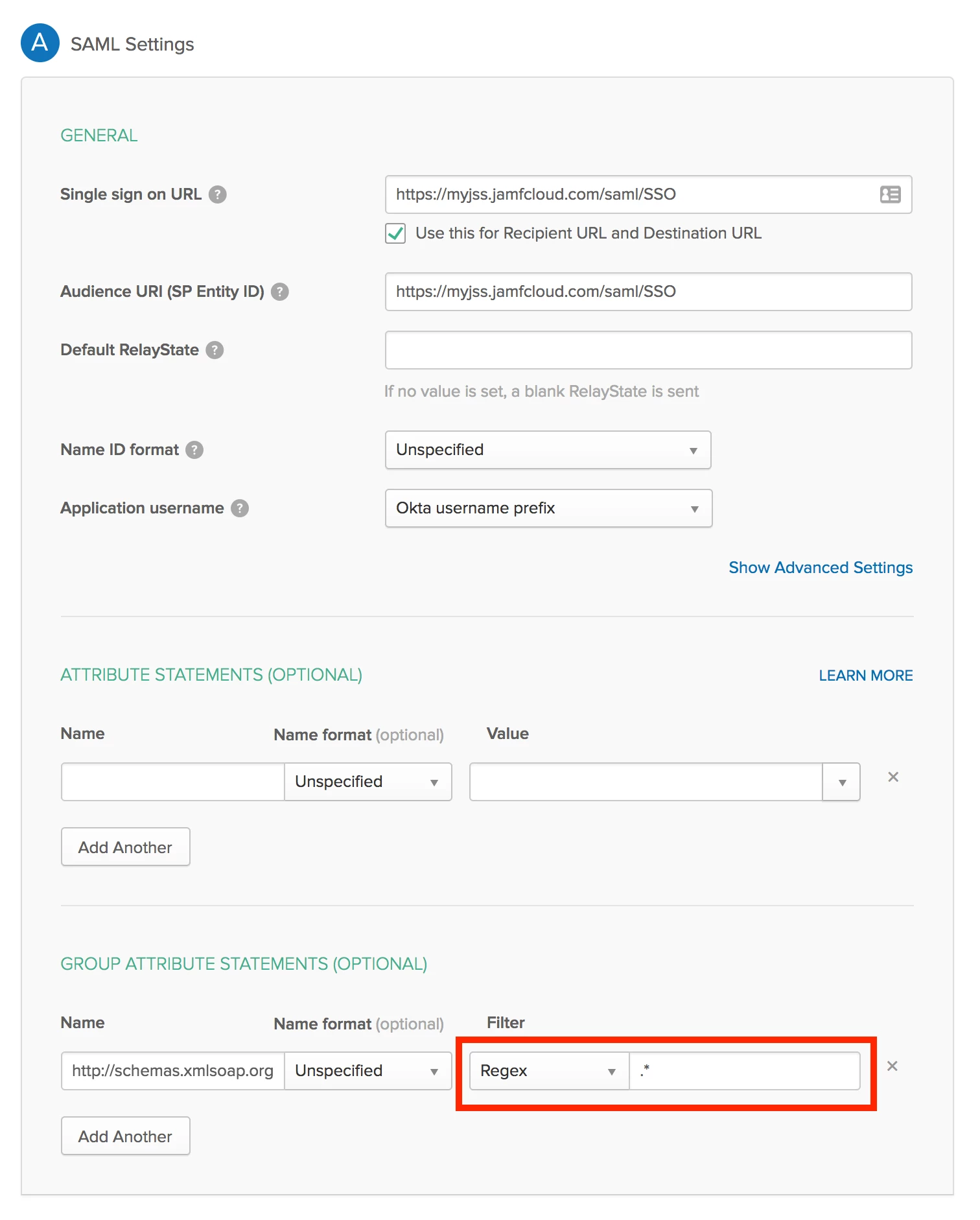
- This step is VERY important. Under Group Attribute Statements, enter:
http://schemas.xmlsoap.org/claims/Groups. The name format should be Unspecified. For Filter, enter Regex and in the field enter.*This will pass all the Okta groups into the JSS. - Click Next, assign to users, and click Save.
- Under the Sign On tab, click the Identity Provider Metadata link to download the metadata file. Save it with a .xml extension.
Now go over to your JSS, click on the Settings gear and go to Single Sign On.
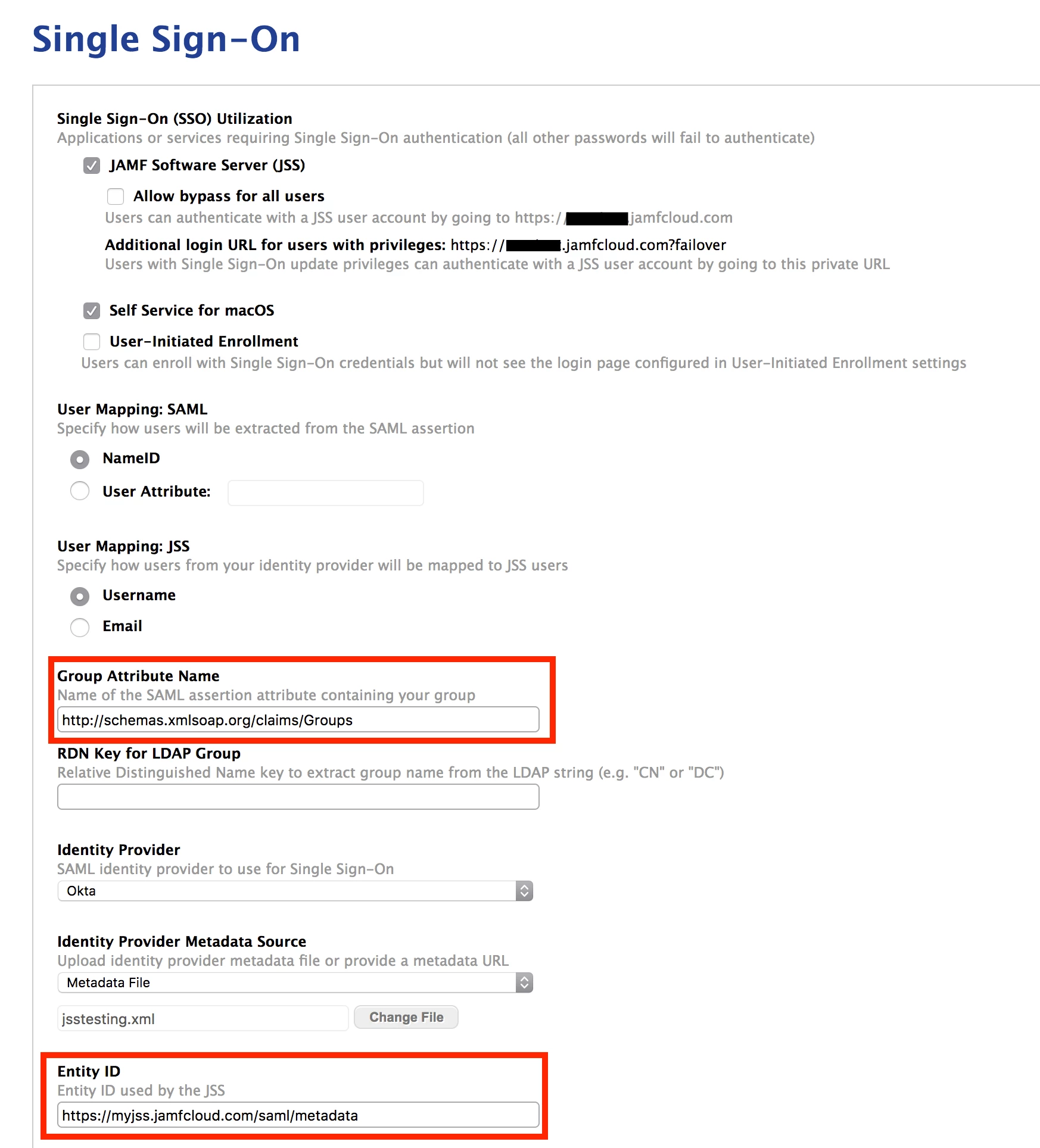
1. Click Edit
2. Check the box for JAMF Software Server, and Self Service/ Enrollment if you desire.
3. For User Mapping: SAML choose NameID
4. For User Mapping: JSS choose Username
5. For Group Attribute Name - enter http://schemas.xmlsoap.org/claims/Groups
6. Select your identity provider, in this case Okta.
7. Upload your metadata file
8. Make sure the Entity ID field is the same as what you entered in Okta under step 5. If it is different, update the OKTA field, NOT the JSS field.
9. Click Save.
You should now be able to log Okta users into the JSS without having to create them in the JSS. If you run into any issues, feel free to reach out to me directly. Here are some screenshots