Hi everyone,
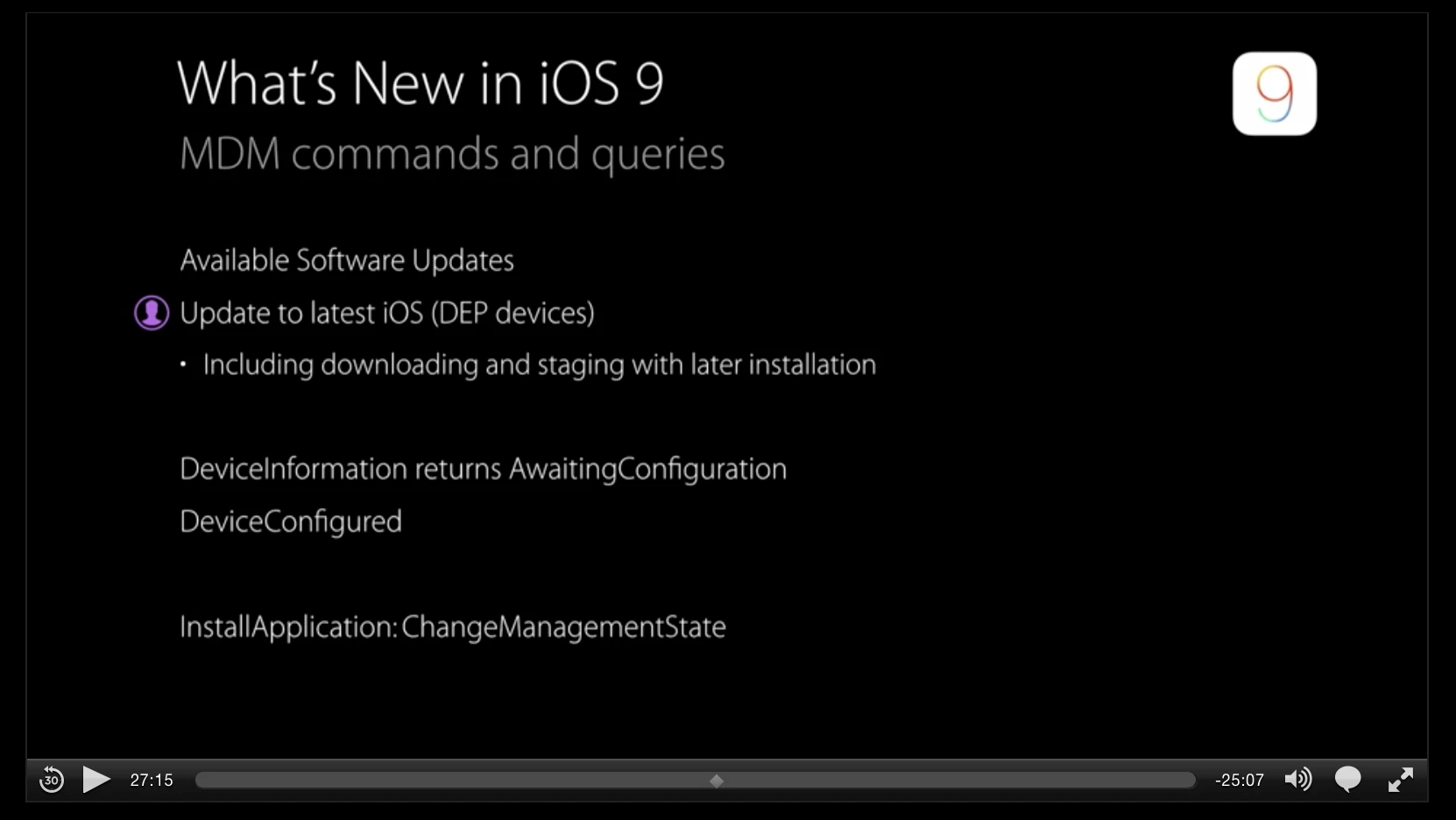
With the recent JSS 9.8 update, we see the new iOS 9 payloads are there, but some features are still missing that were announced (we're probably misunderstanding something or have missed it). We don't see a way to:
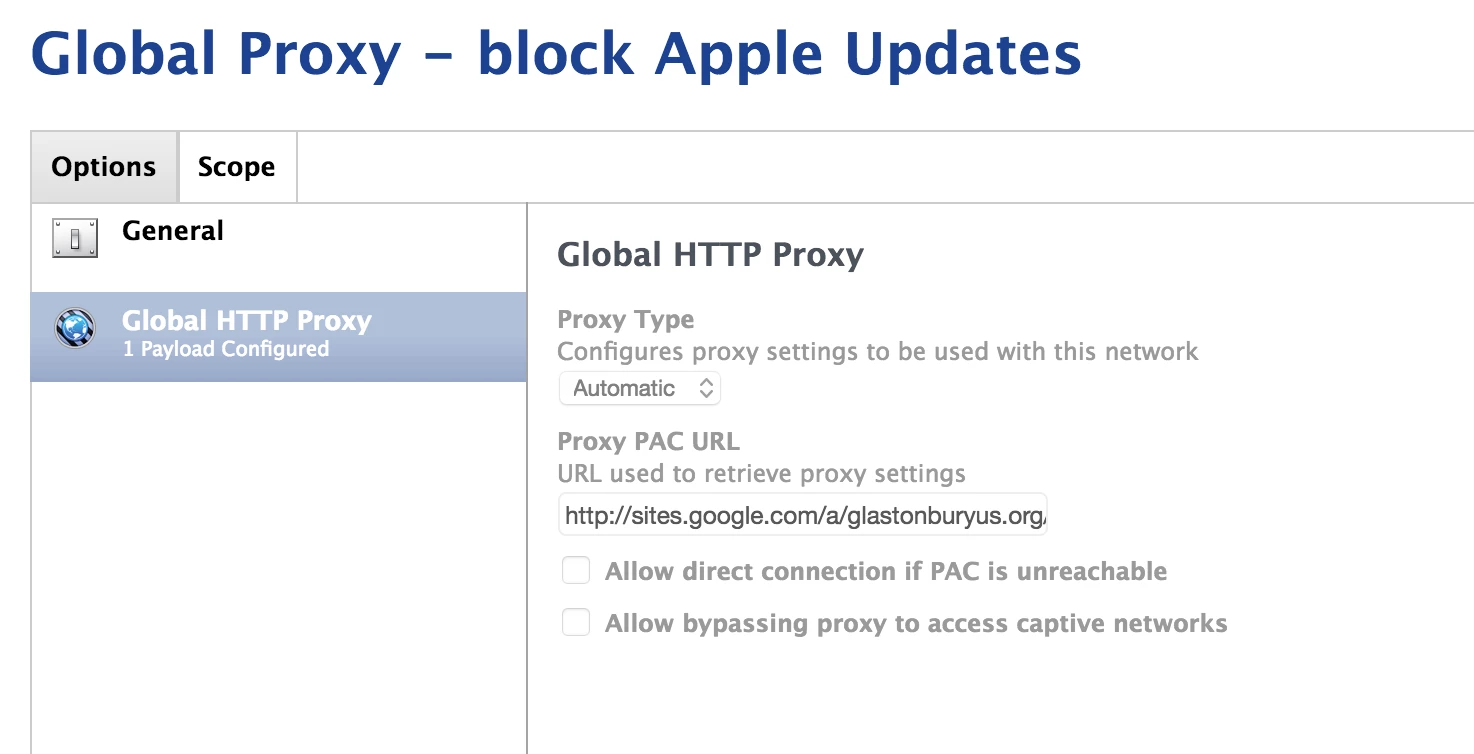
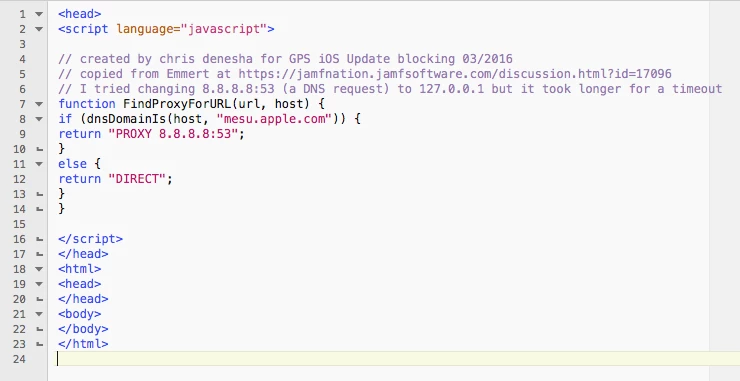
- block the user to update iOS
- force to download and update iOS
- block the user to update apps
- change the lock passcode for an iOS device
Is this still coming, or have we misunderstood something?