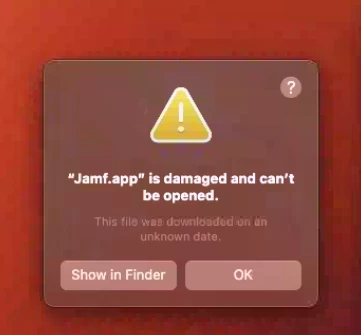
Noticed this message on one of my pilot machines today. I had to reinstall the framework via the API. Anyone seen this on version 10.44.1 or 10.45.0 of Jamf Cloud? User is running macOS Ventura 13.2.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.