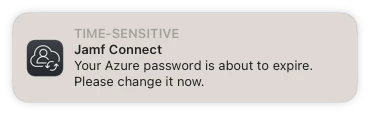
We are using Jamf Connect and Azure to sync accounts/passwords with MacOS. The computers are not AD bound. Is it possible to get Jamf to warn users when their password is set to expire (we have a company policy to reset every 90 days)?
If not, what are other fellow admins doing in this case?