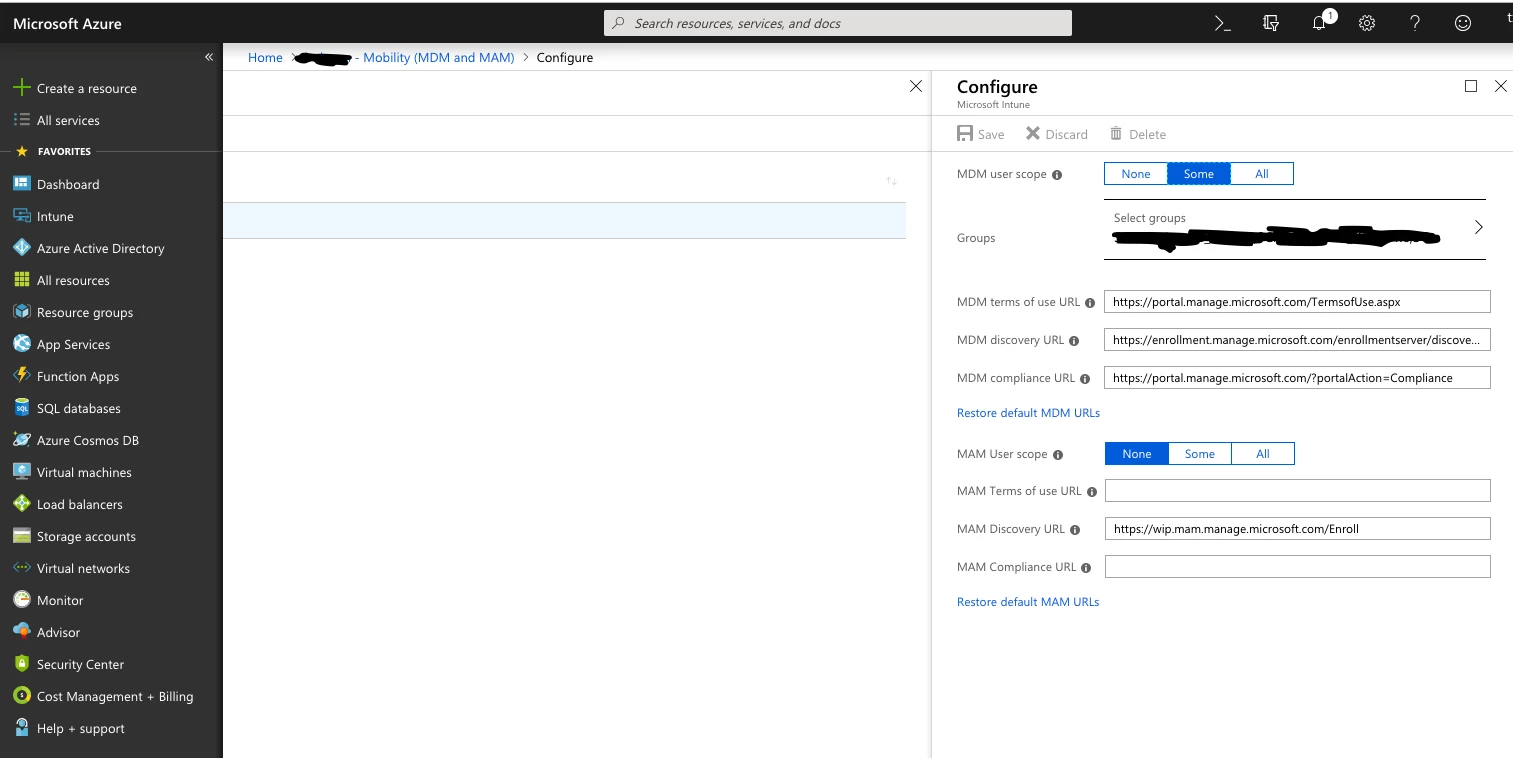
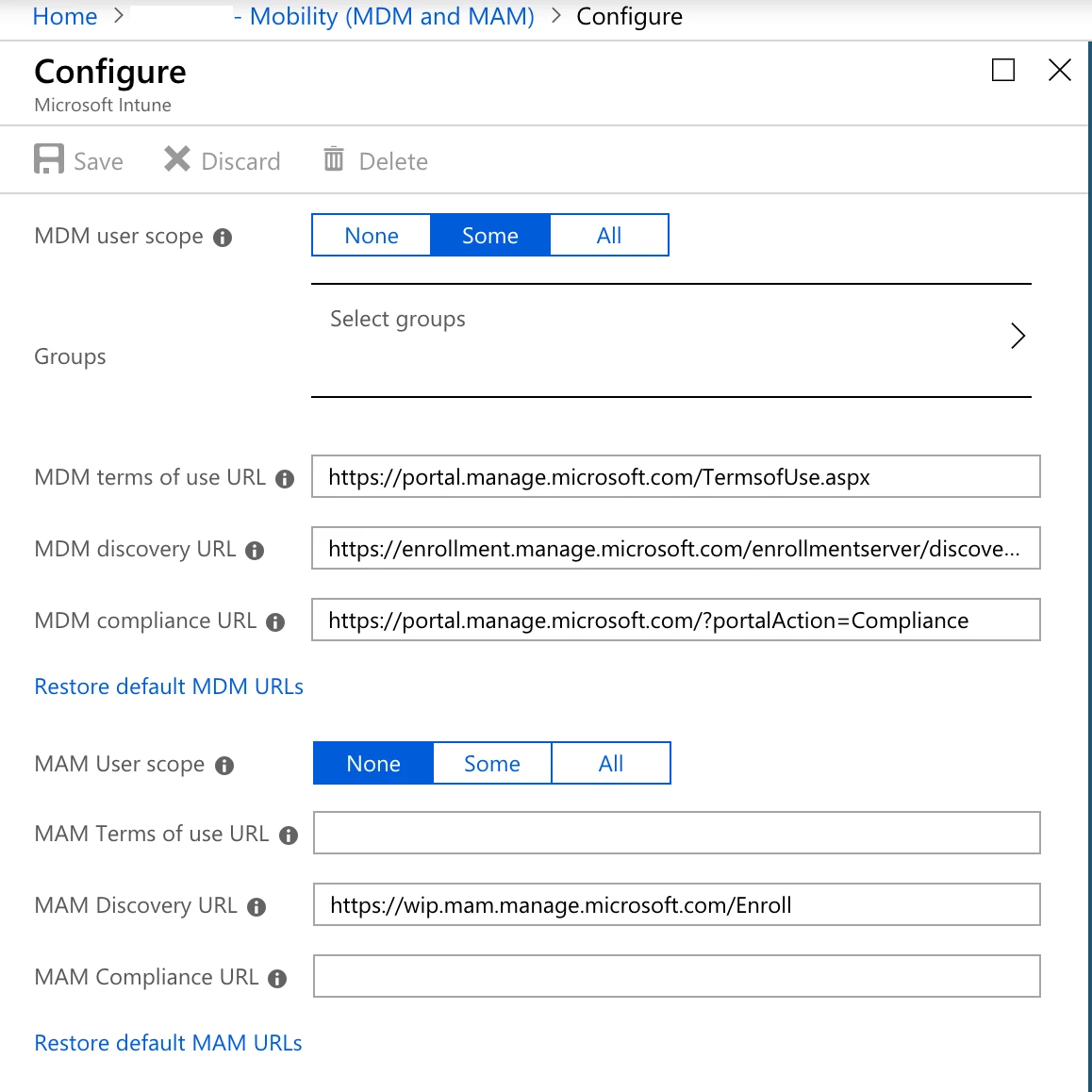
So i have Jamf and intune talking fine the app ID is all good and all says its fine.
I can enrol from self service and the Mac shows in Azure as registered but then it never seems to talk to InTune to pass on the computer details and become compliant.
Is anyone else having trouble with this? I use version 1.5 of company portal but have had this issue since version 1.1. It worked once for one device but now its fully broken and nothing enrols correctly.
Any help would be amazing as even Microsoft have no idea and the case is still ongoing.