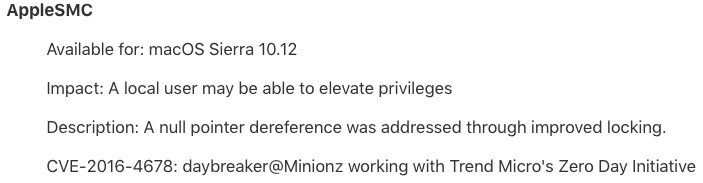
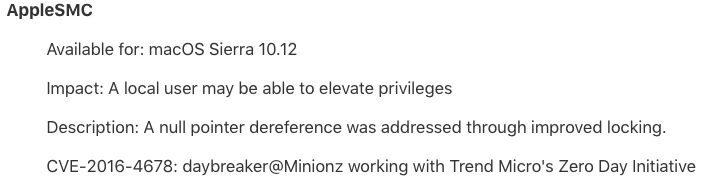
A new hotfix release is coming soon for Jamf Pro 9.97.1488392992 (formerly Casper Suite). This release includes an important security fix and we recommend customers upgrade to the latest version as soon as possible. We will notify Jamf Pro customers via email and on Jamf Nation as soon as the hotfix release becomes available.
If you have any questions about this release or anything else, please do not hesitate to reach out.