Hey there,
I edited a /bin/bash script that automatically checks the devices uptime and tells the user to restart his computer after 2weeks uptime (with the help of https://www.jamf.com/jamf-nation/discussions/17336/user-has-not-restarted-in-x-number-of-days)
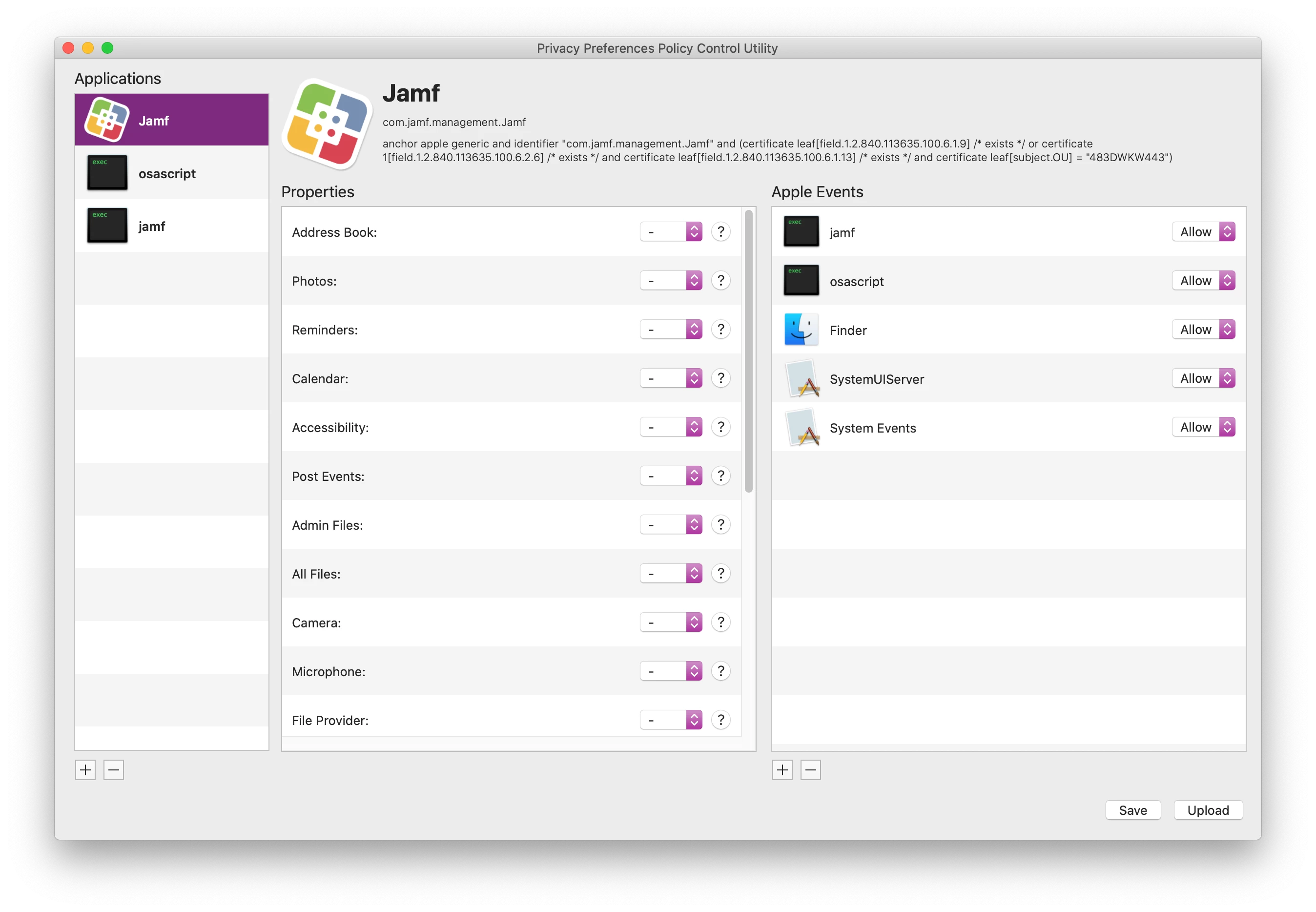
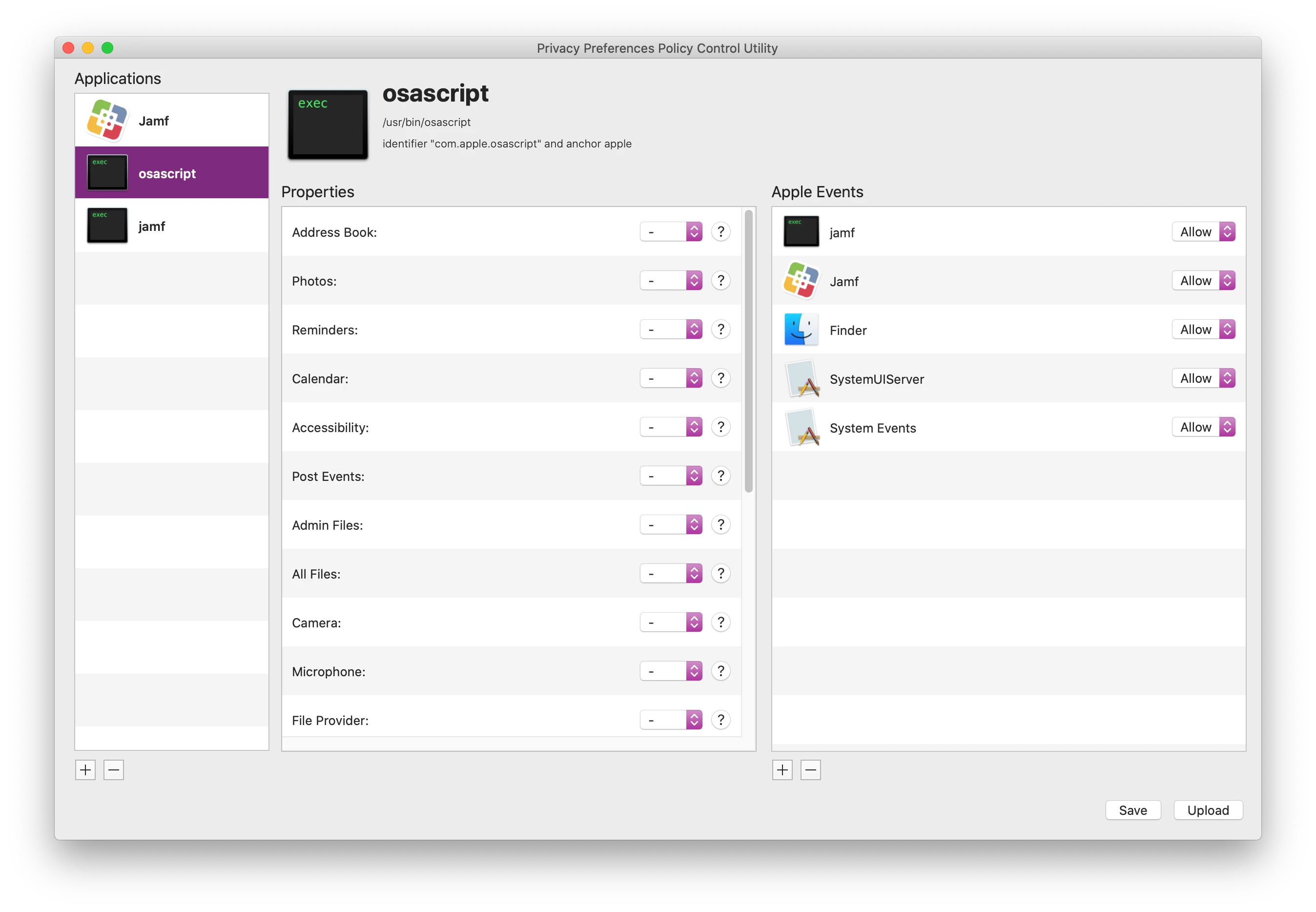
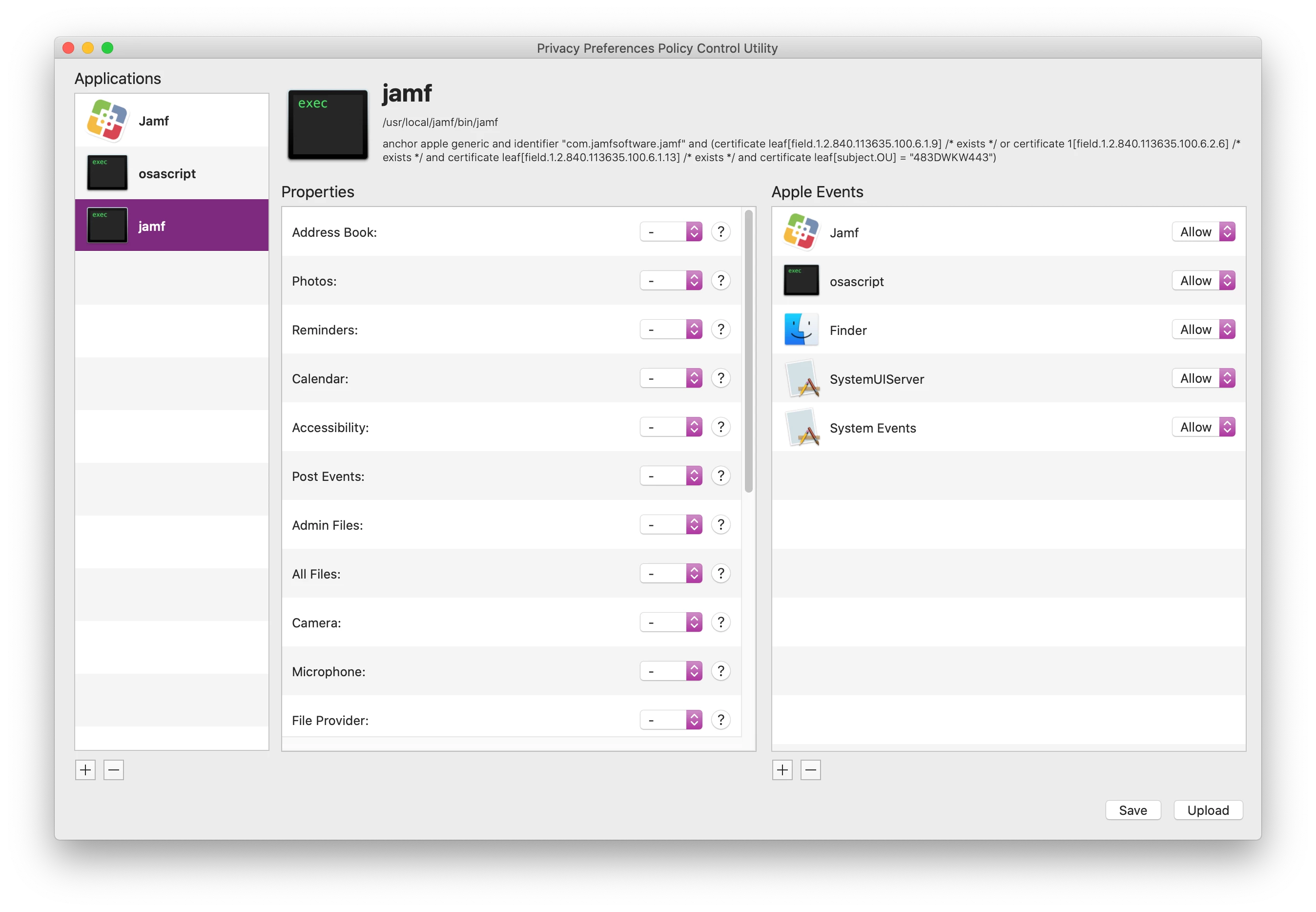
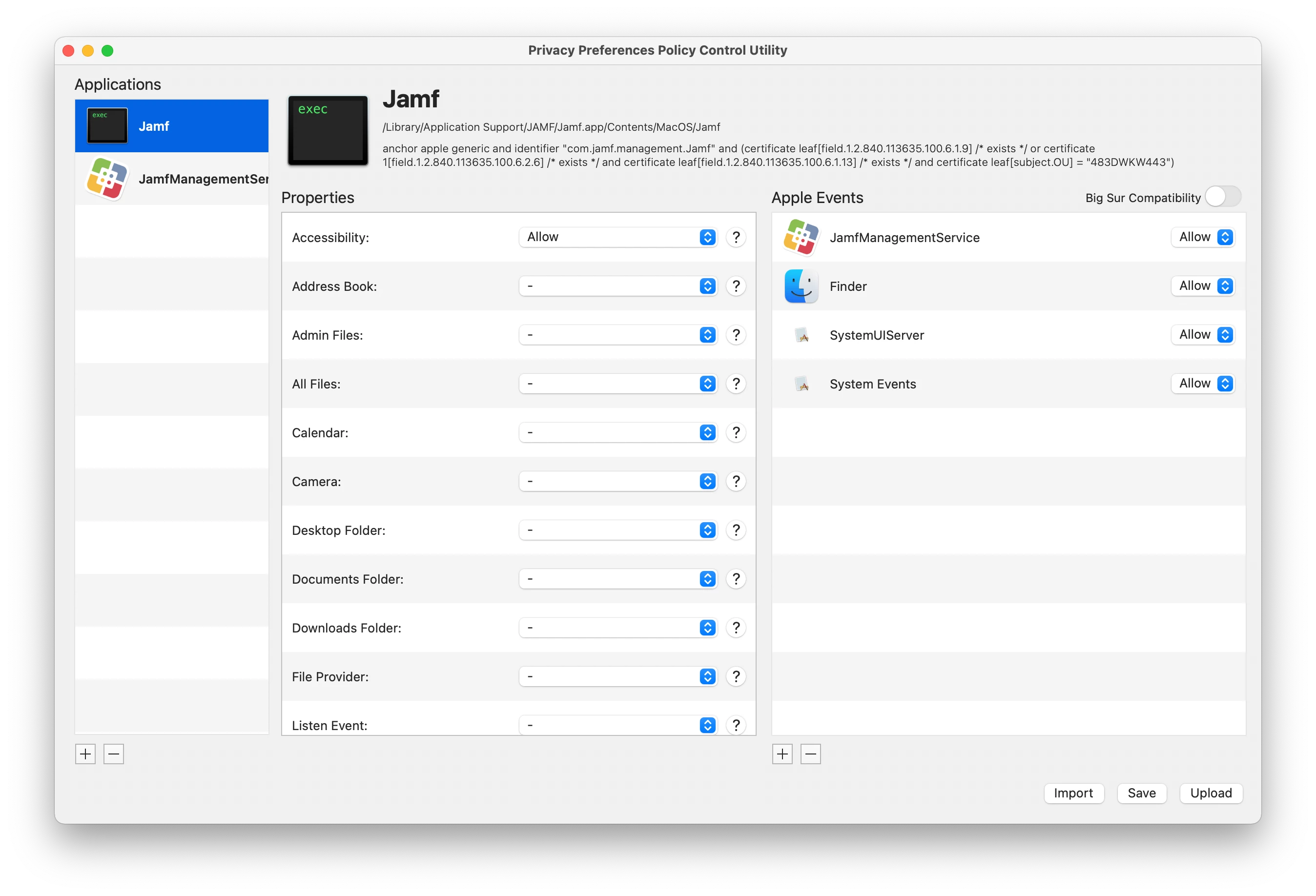
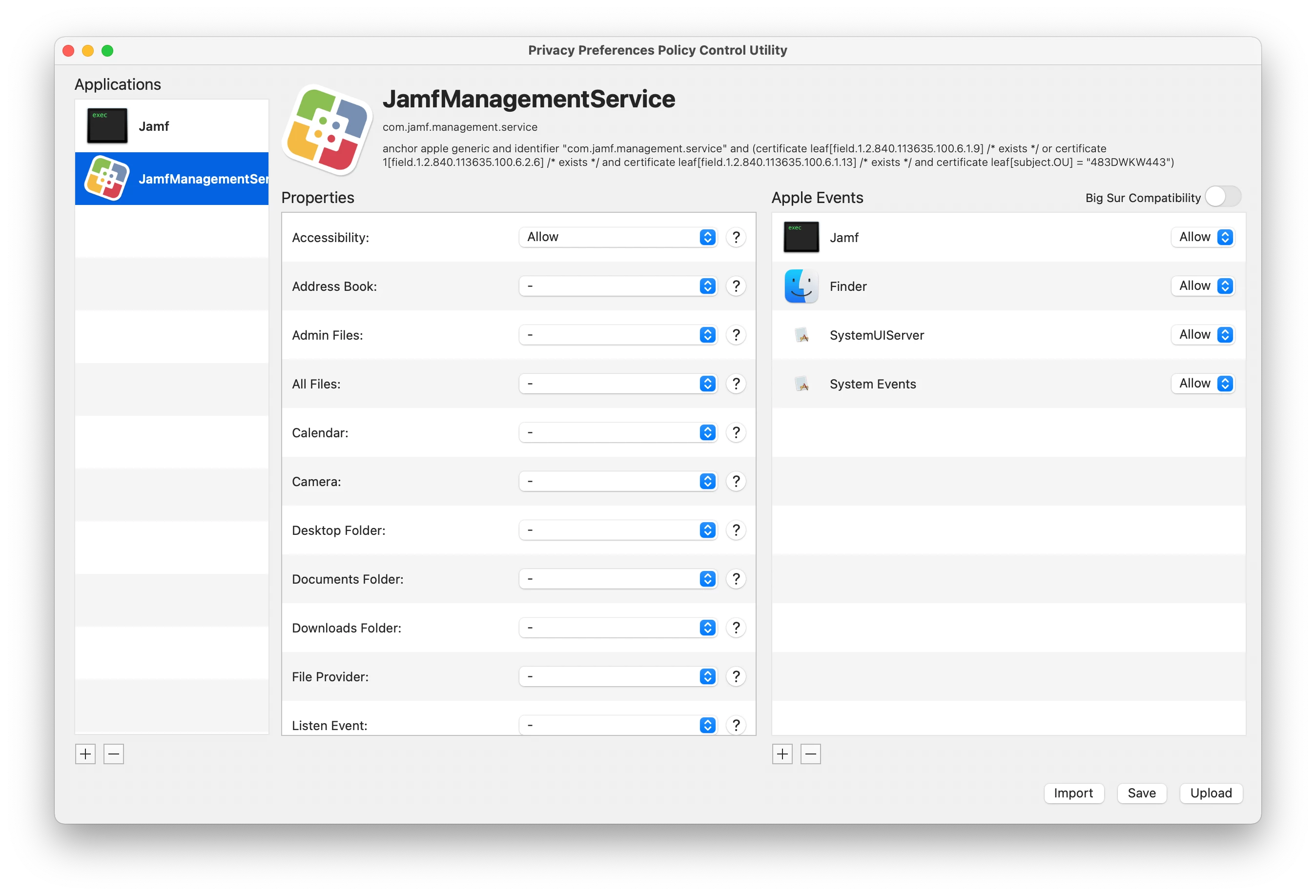
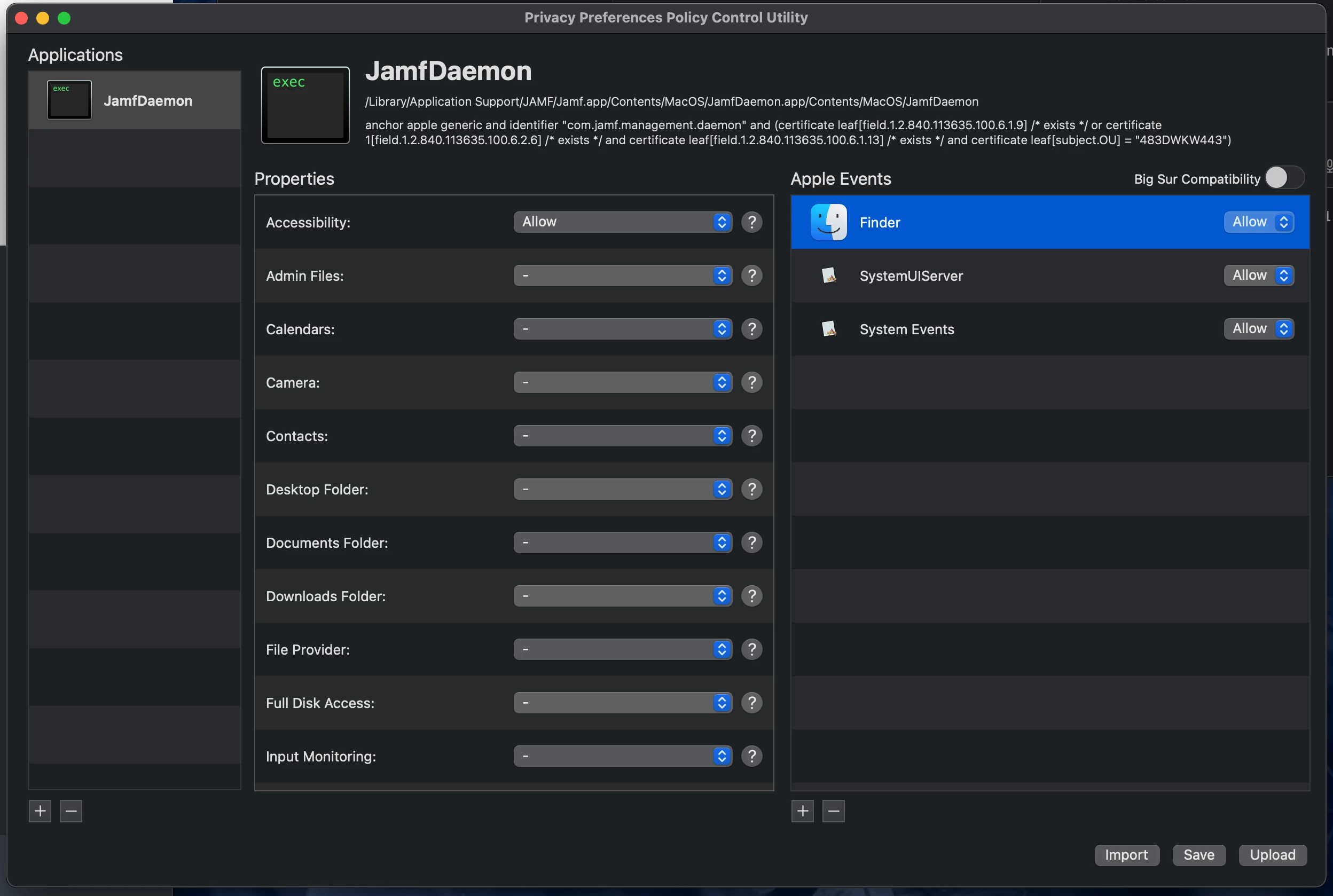
The following part generates the ""jamf" wants access to control "system events"" message for end users:
#!/bin/bash
# Discover logged in user
user=`stat -f%Su /dev/console`
#Execute code as logged in user (instead of root)
sudo -u $user /usr/bin/osascript <<-EOF
tell application "System Events"
activate
set question to display dialog "The device has not been restared for [...]"
with title "RESTART YOUR COMPUTER" buttons {"Shut Down", "Restart", "Cancel"} ¬
cancel button "Cancel" with icon caution
set answer to button returned of question
if answer is equal to "Shut Down" then
tell application "System Events"
shut down
end tell
end if
if answer is equal to "Restart" then
tell application "System Events"
restart
end tell
end if
if answer is equal to "Cancel" then
return
end if
end tell
EOF
exit 0
fiI already read the thread (https://www.jamf.com/jamf-nation/discussions/30388/loginwindow-wants-access-to-control-system-events) but couldn't find the solution there.
The issue seems to be the tell / end tell statement but I can't find a way to change the script.
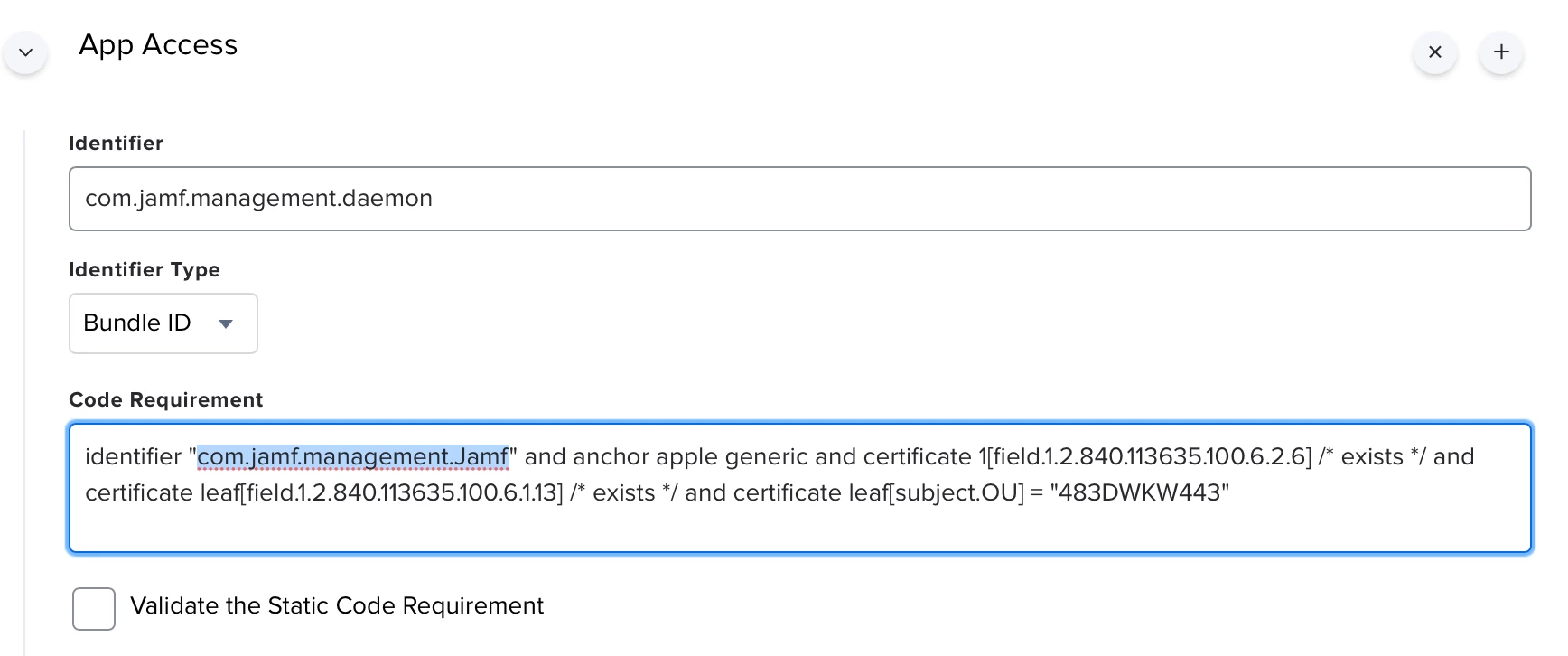
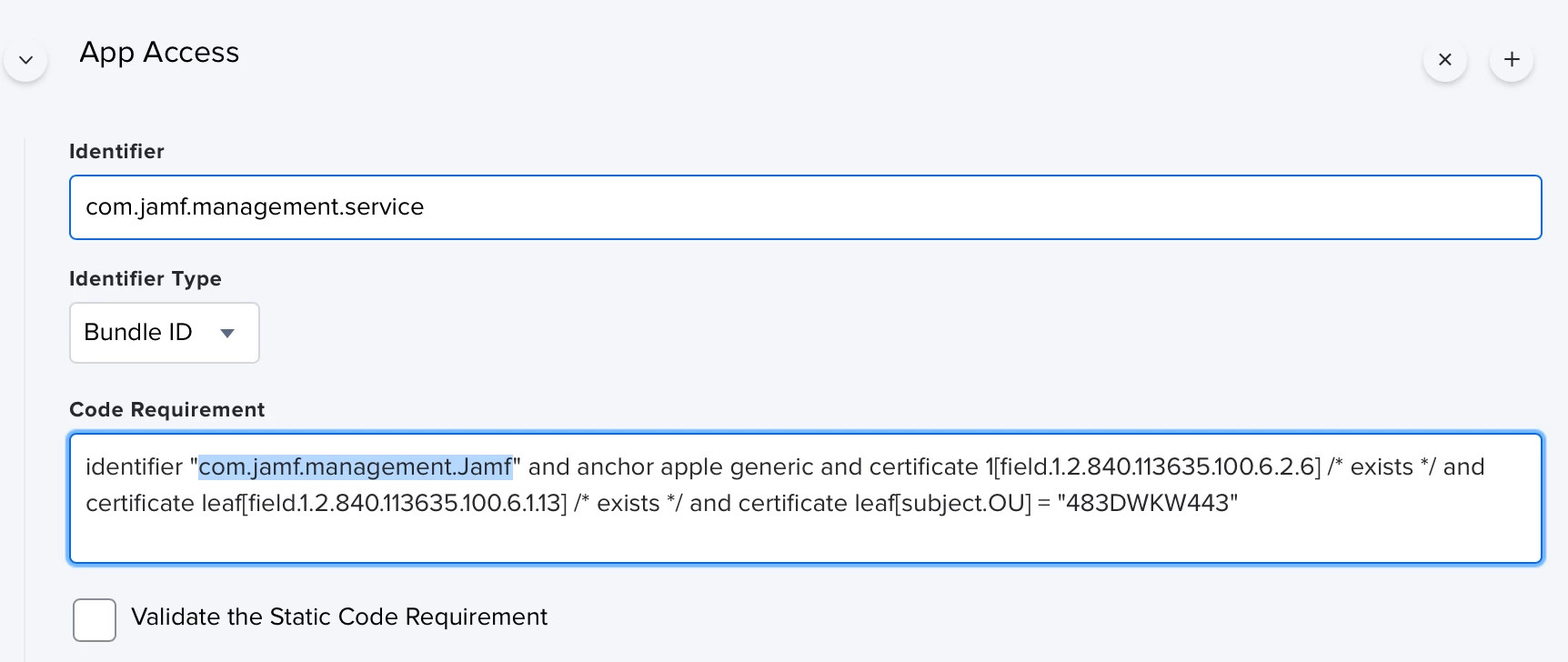
I tried several PPPCs and gave JAMF access to Accessibility, System Events and everything else that's required.
The script itself works fine.
Can someone help me out here?