We got Defender working on our Macs about a year ago - deployed via JAMF Pro and with configuration profiles. We are not bound to the domain and do not use JAMF Connect.
I am trying to follow along with Microsofts documentation (Onboard and offboard macOS devices into Microsoft Purview solutions using JAMF Pro | Microsoft Learn) which seems to be written for setting this up from scratch rather than adding it in to an existing setup. It seems to be doing something as we are getting better feedback under Device Onboarding, but still not making much progress.
Here is an example of the details in Device Onboarding in Microsoft Purview with the error messages before and the more informative messages after I have created the configuration profiles in JAMF from the above guide:
View under Device Onboarding: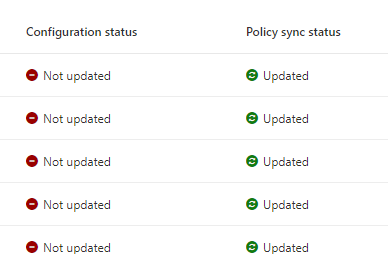
Before the configuration profiles were updated:
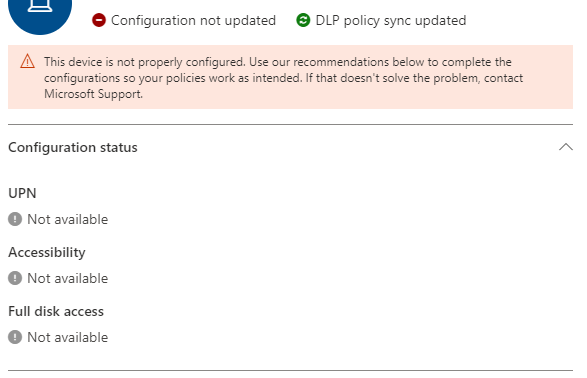
After the configuration profile was updated: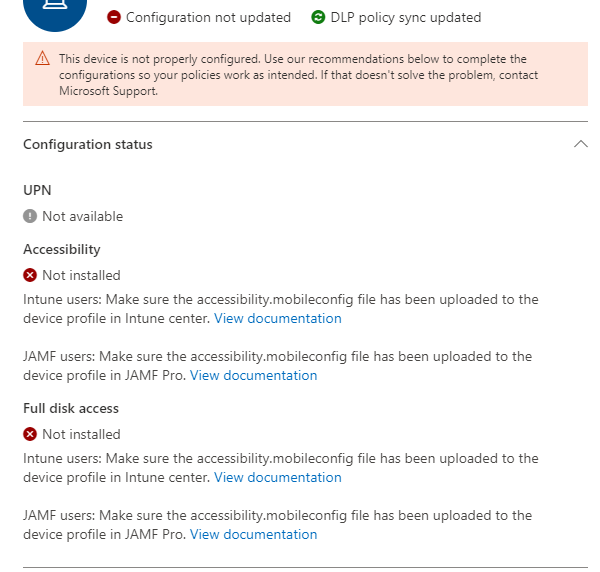
In the documentation that I linked to near the top, there is a "Before You Begin section which mentions this (formatting mine for clarity):
- Make sure your macOS devices are managed through JAMF pro and
are associated with an identity (Microsoft Entra joined UPN) through JAMF Connect or
Microsoft Intune.
We are managed through JAMF Pro, but we don't use JAMF Connect and they don't seem to have a UPN as shown in the screen shots above. I suspect this is a big part of the problem - but not sure how to fix it. Or am I incorrect and this is a red herring to some other problem in the Configuration Policy/settings/PPPC in JAMF Pro? Maybe both?





