Hi everyone,
I'm currently trying to deploy Jamf Protect across my company, where about 90% of the users are developers.
Since deploying Protect, we have noticed a massive slowdown during npm install — installation time is multiplied by 4 to 5, depending on the machine and project.
To try to fix this, I added the following exceptions:
-
Download Event exclusion
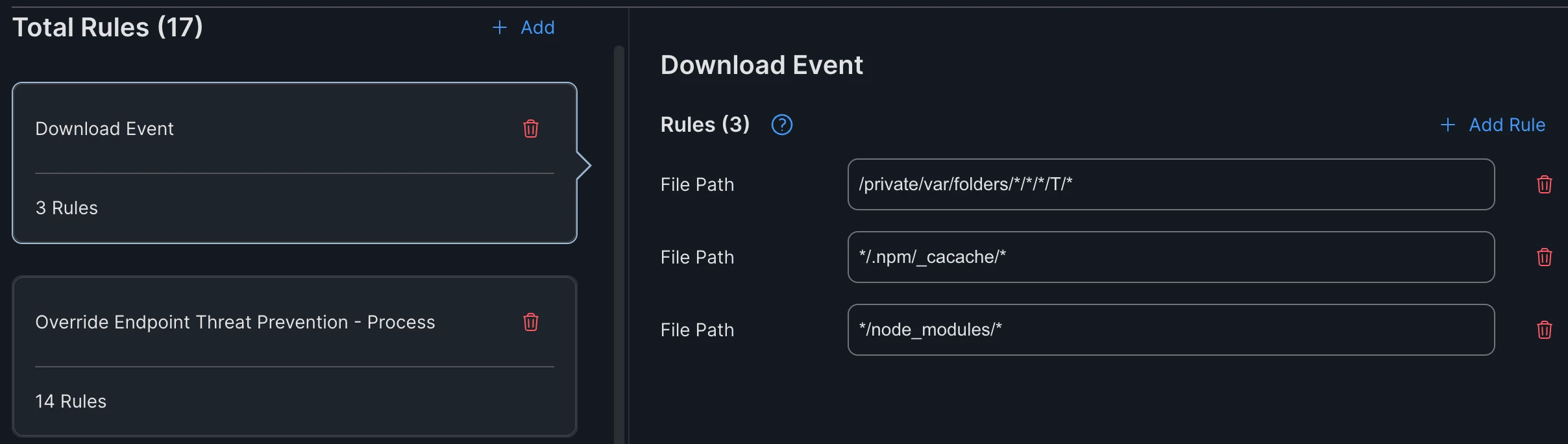
-
Override Endpoint Threat Prevention – Process exclusions
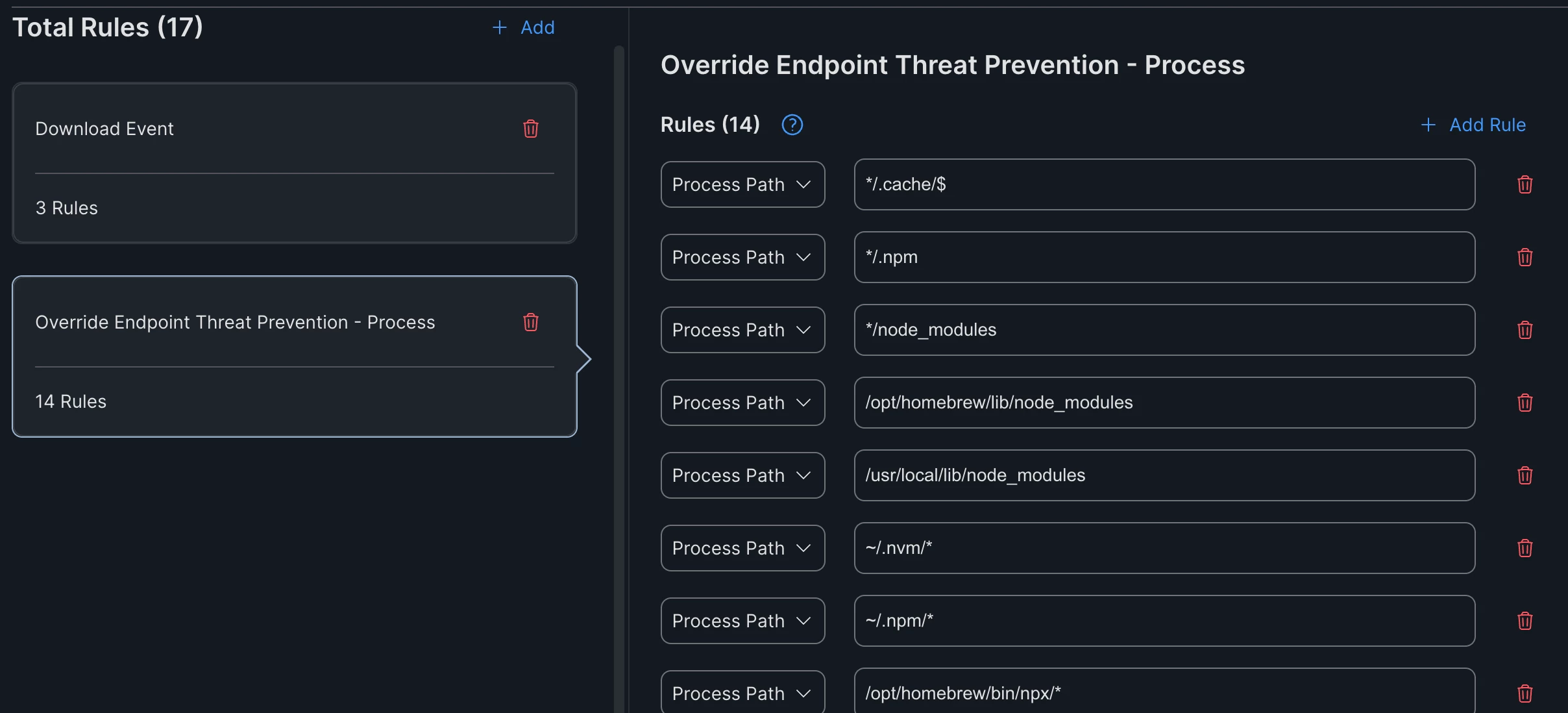
However, instead of improving performance, these exclusions seem to make the scan even slower.
Has anyone experienced similar slowdowns with Protect during package-heavy operations (npm, yarn, brew, Xcode builds, etc.)?
Do you have recommendations for:
-
the correct type of exceptions to configure,
-
paths or processes that should be excluded,
-
or general best-practices for developer-heavy environments?
Any help would be greatly appreciated — this is currently blocking our deployment.
Thanks!

