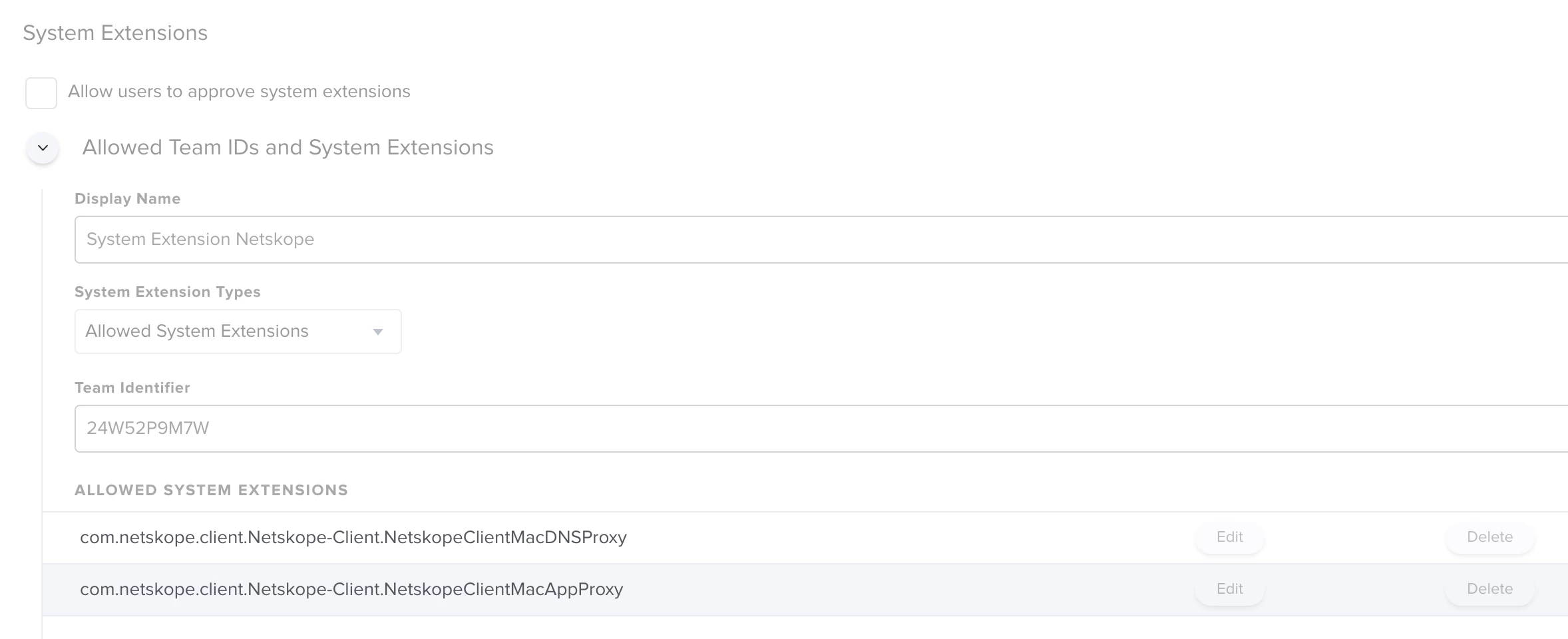
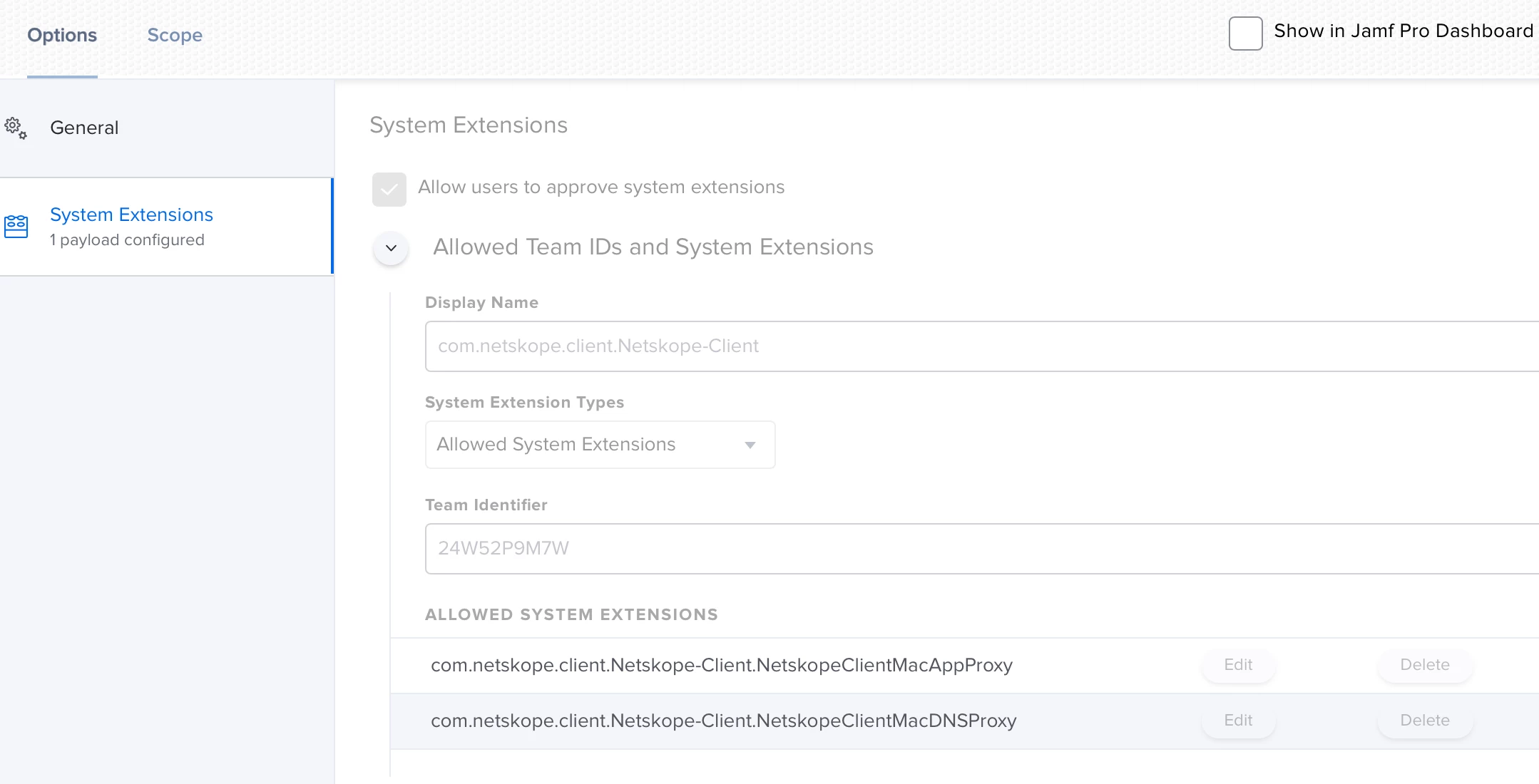
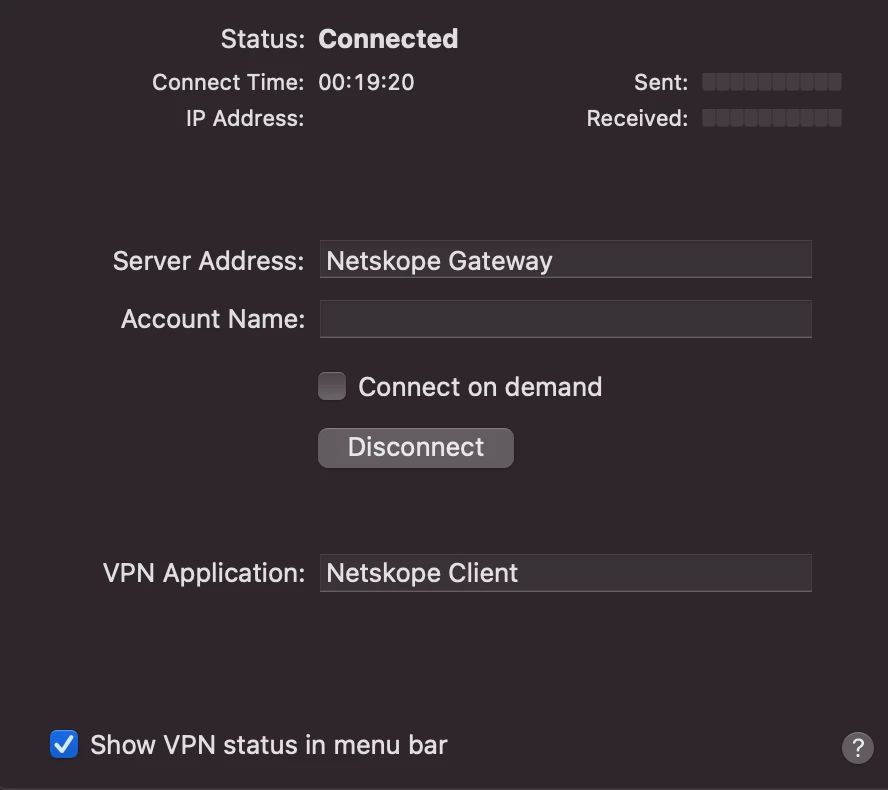
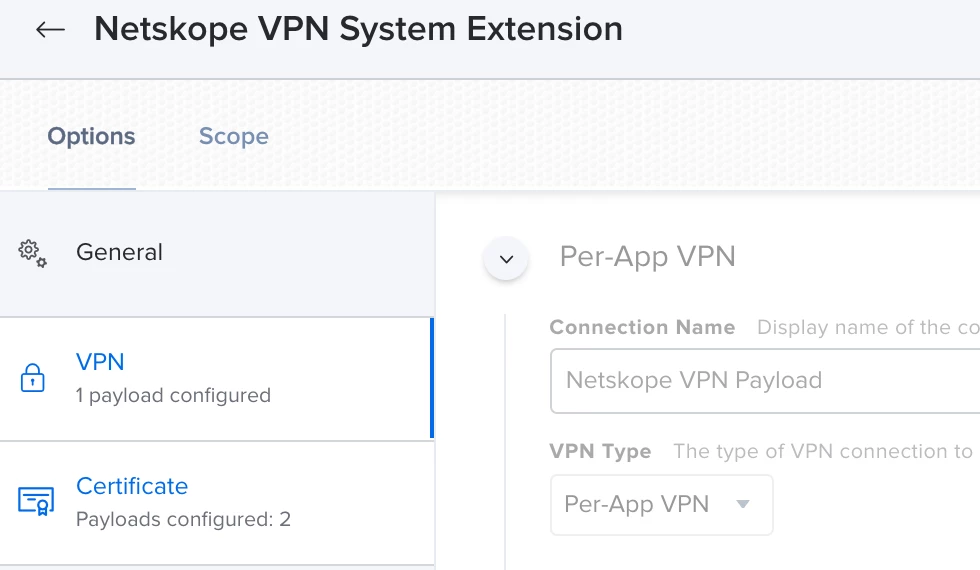
Hey everyone, I recently got passed handling our Netskope deployment. My predecessor claims that with the v71 client, due to us using Azure AD for our IDP we cannot auto populate the tenant information. Basically once the install finishes we get a popup where we have to input our company name.
I know there has to be a way around it, anyone have any familiarity with it?