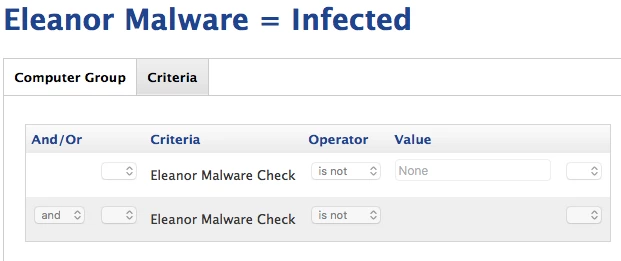
It's a trojan that comes along for the ride with a an app called EasyDoc Converter.app. It's a full-access backdoor which uses your expected resources of Tor, pastebin, etc.
I can't actually find the application anywhere (not that I looked that hard) but I've already setup "EasyDoc Converter.app" in my restricted software. I'm not sure that's the actual process name of the app at launch (when it prompts for credentials to get in place). :-
http://www.cultofmac.com/436670/dangerous-new-mac-malware-fully-compromises-os-x/
https://labs.bitdefender.com/wp-content/uploads/2016/07/Backdoor-MAC-Eleanor_final.pdf