Hi,
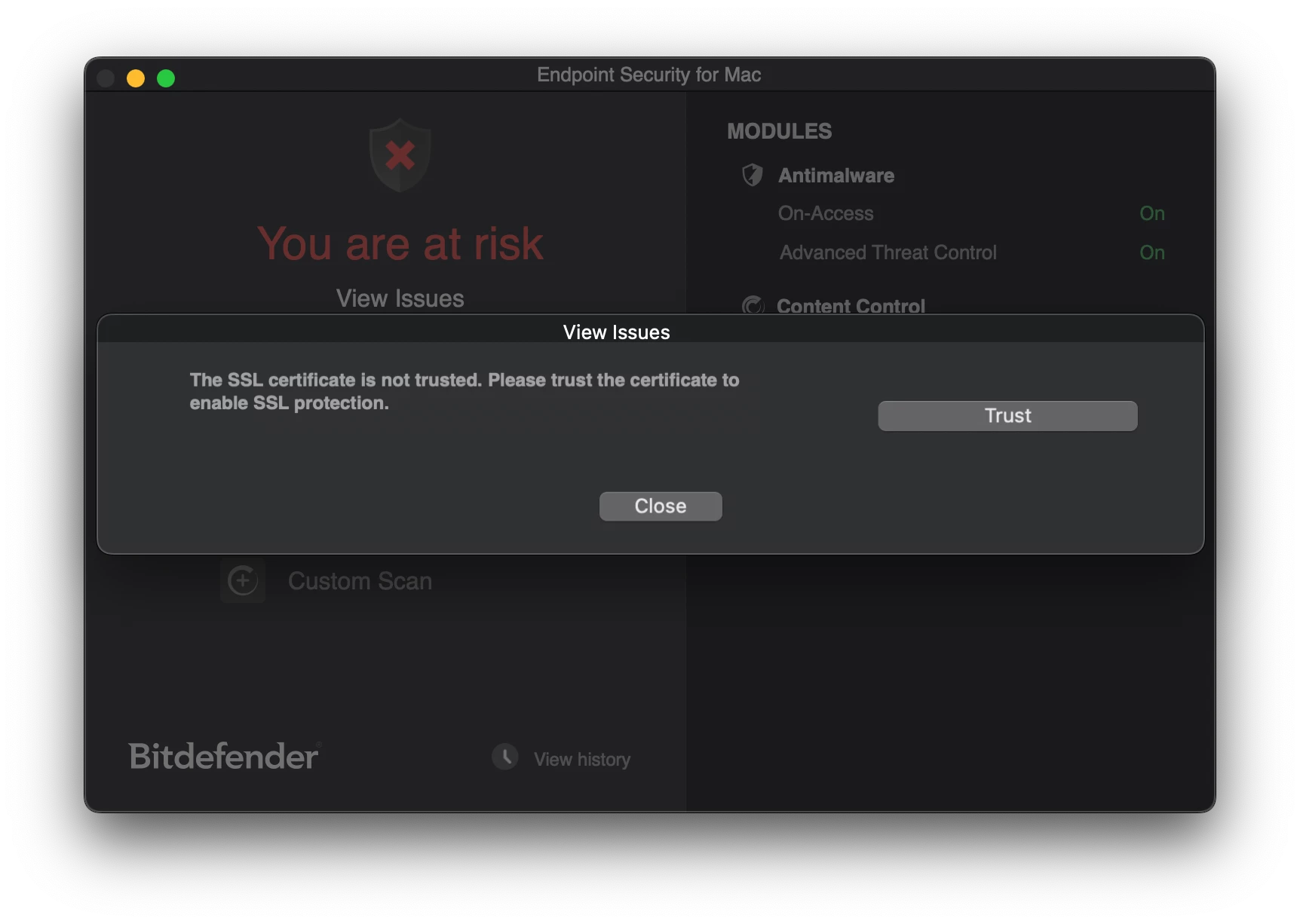
Bitdefender has activated a new web content control module in the Endpoint Security app, which now results in the end user having to approve a system extension.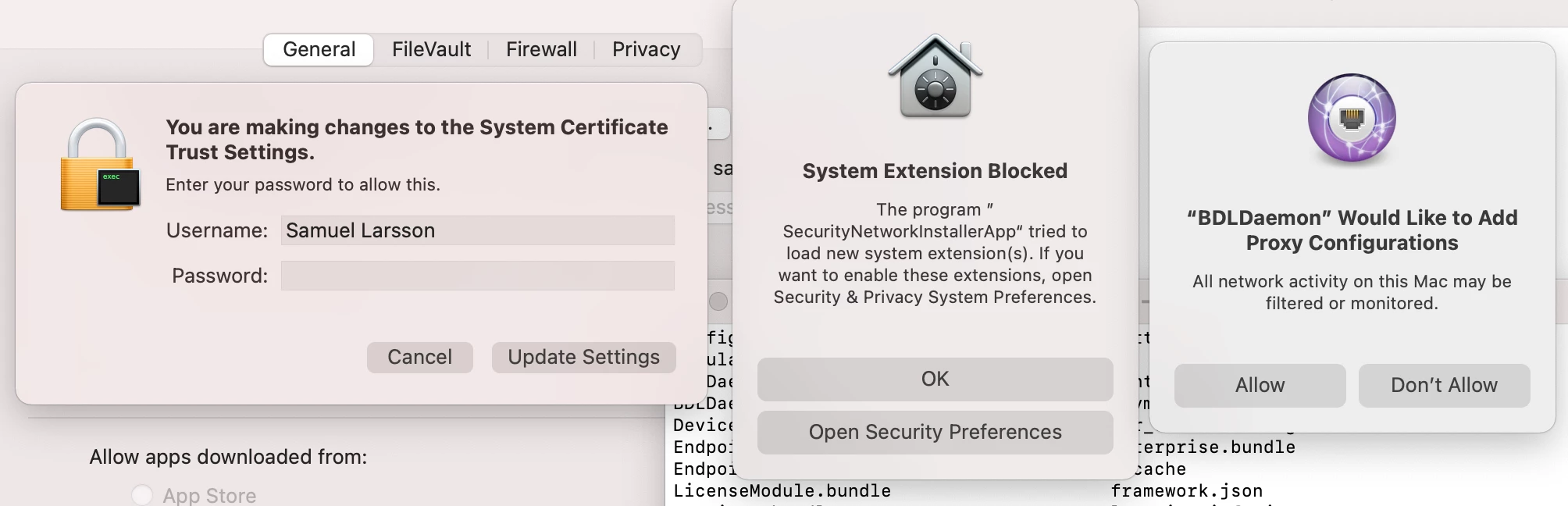
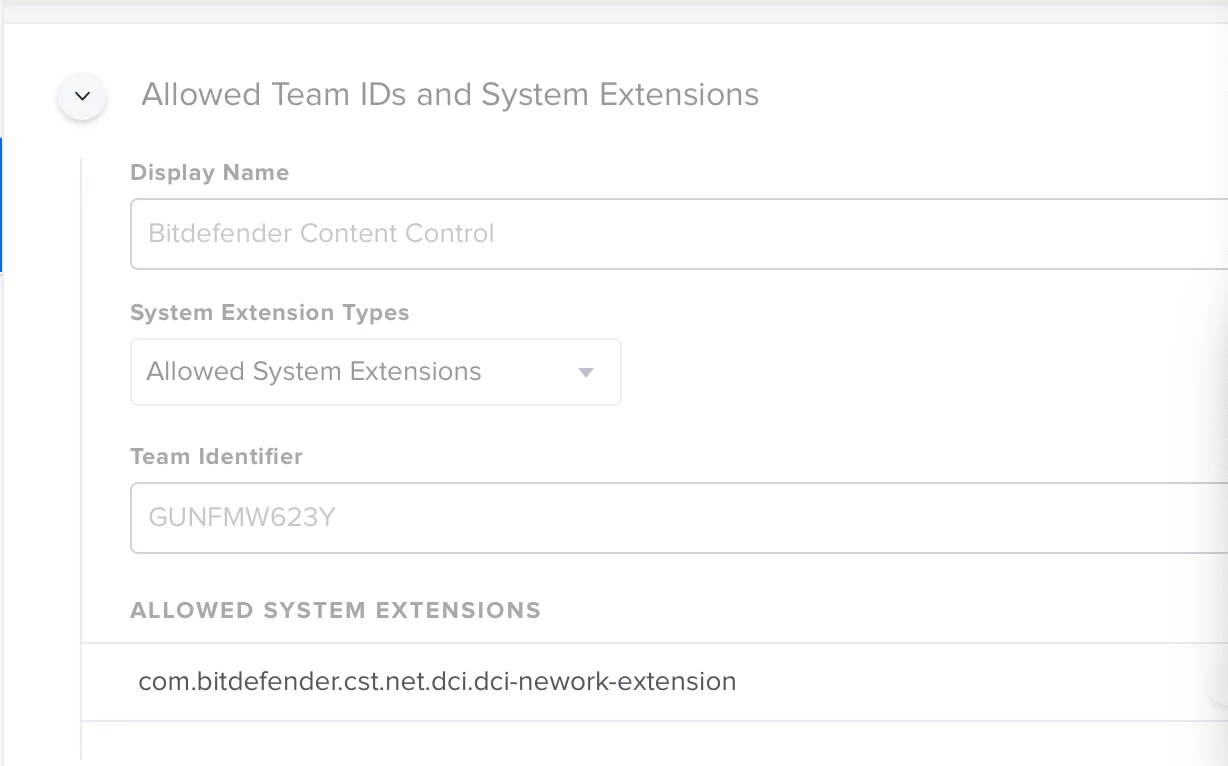
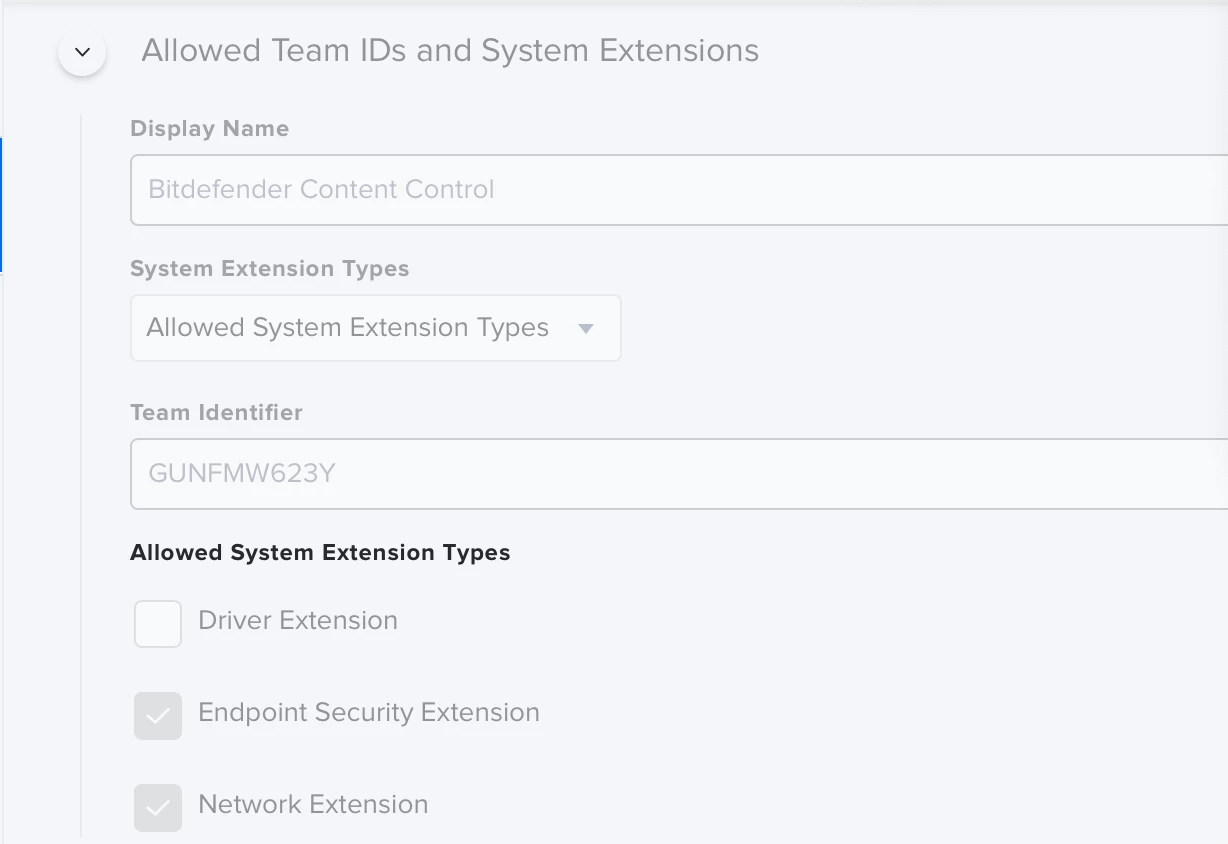
I have tried to add the below approved system extensions in a config profile, but they still show up. What else can I do?