Hello,
Has anyone been able to configure the Payload needed for Crowstrike to run with Ventura? (Screenshot attached it all Crowstrike's support continues to give me)
I have configured the system extensions as well as the content filter, but can't seem to figure this one out as they don't give much information. I've attempted to use PPPC-Utility as well as Apple Configurator, but they don't seem to work. As we have to go in and manually approve access. This is not ideal as it's our antivirus software and we'd like to have it up and running as soon as the device is enrolled.
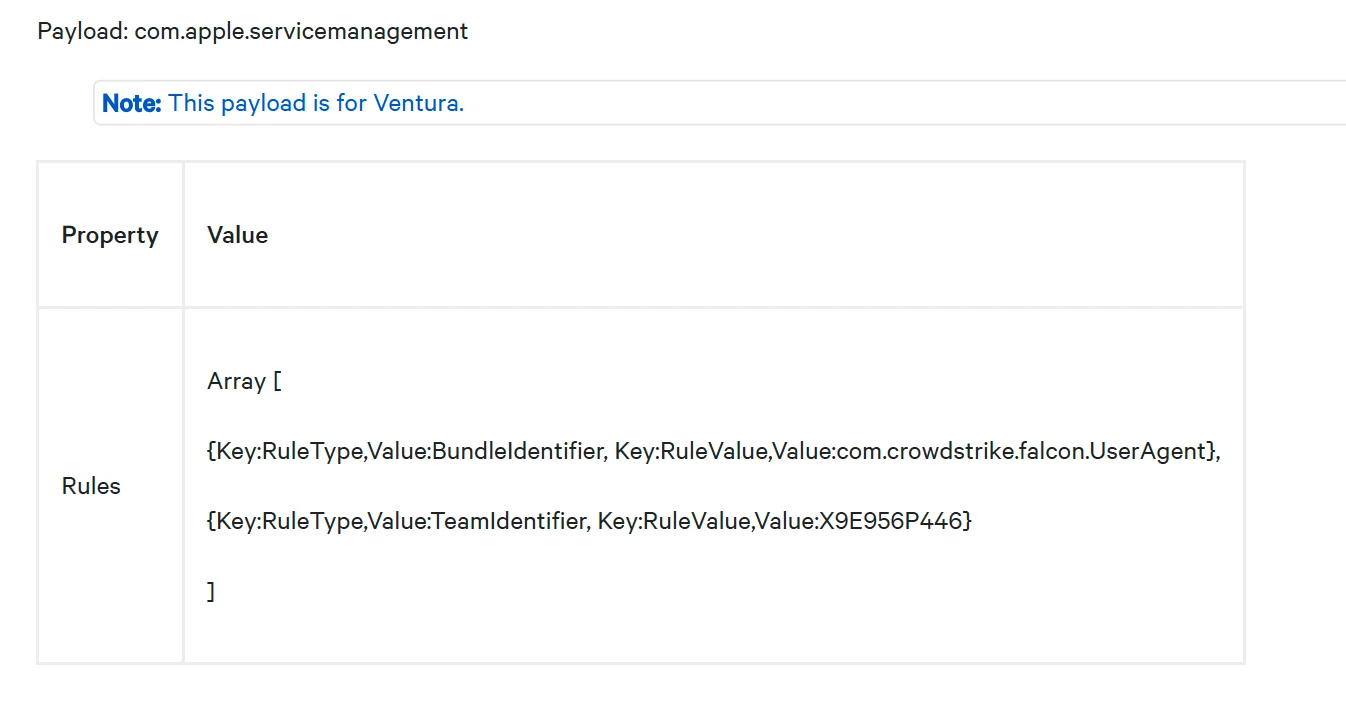
I am also confused about how to enter the XML script into Jamf, that they provide to allow full disk access to Crowstrike. (Code below)
Any assistance is much appreciated. Thank you!
<dict>
<key>SystemPolicyAllFiles</key>
<array>
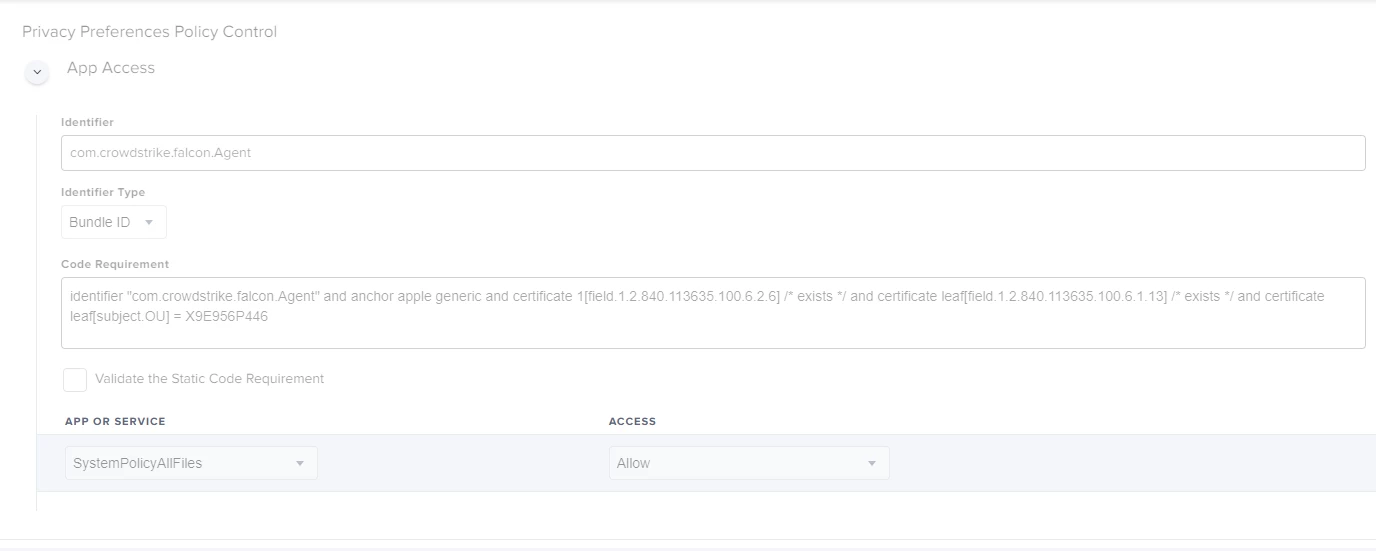
<dict>
<key>Allowed</key>
<true/>
<key>CodeRequirement</key>
<string>identifier "com.crowdstrike.falcon.Agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = X9E956P446</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.crowdstrike.falcon.Agent</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<false/>
</dict>
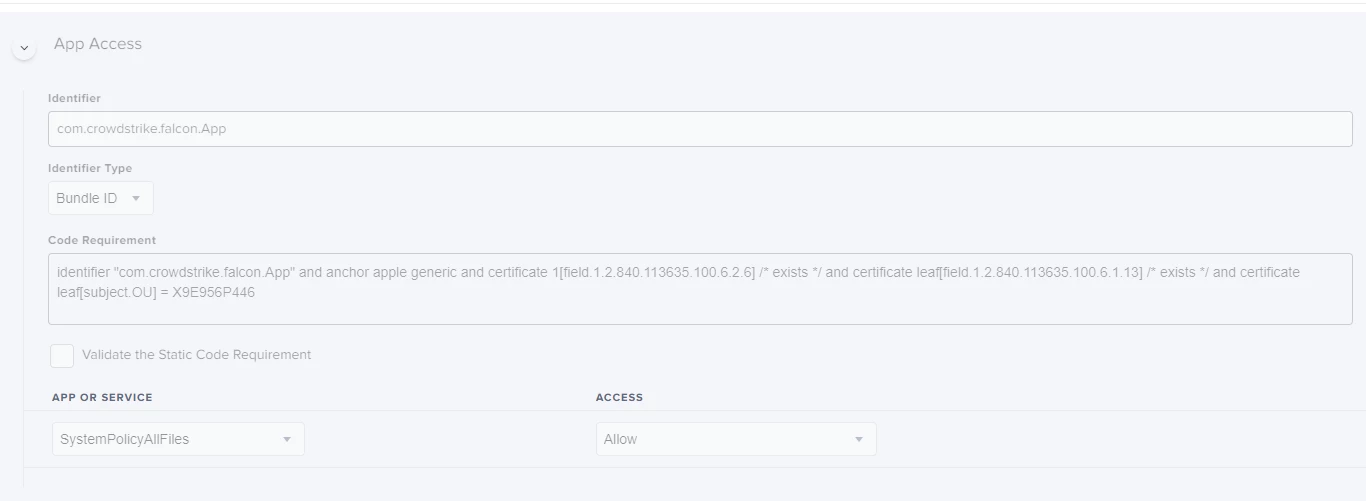
<dict>
<key>Allowed</key>
<true/>
<key>CodeRequirement</key>
<string>identifier "com.crowdstrike.falcon.App" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = X9E956P446</string>
<key>Comment</key>
<string></string>
<key>Identifier</key>
<string>com.crowdstrike.falcon.App</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<false/>
</dict>
</array>
</dict>