Hi everyone
is it possible to get the result of the variable for configuration profile in lower case?
Currently I have configured “Lock primary account information” with variables(see screenshot)
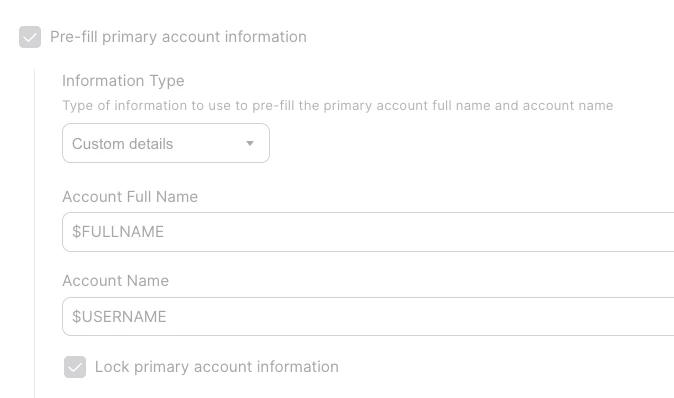
The result of the variable is always in upper case. it is possible to change it to lower case? if yes then how?


