Good Day!
I am testing Platform SSO out in our environment and so far it is working great!
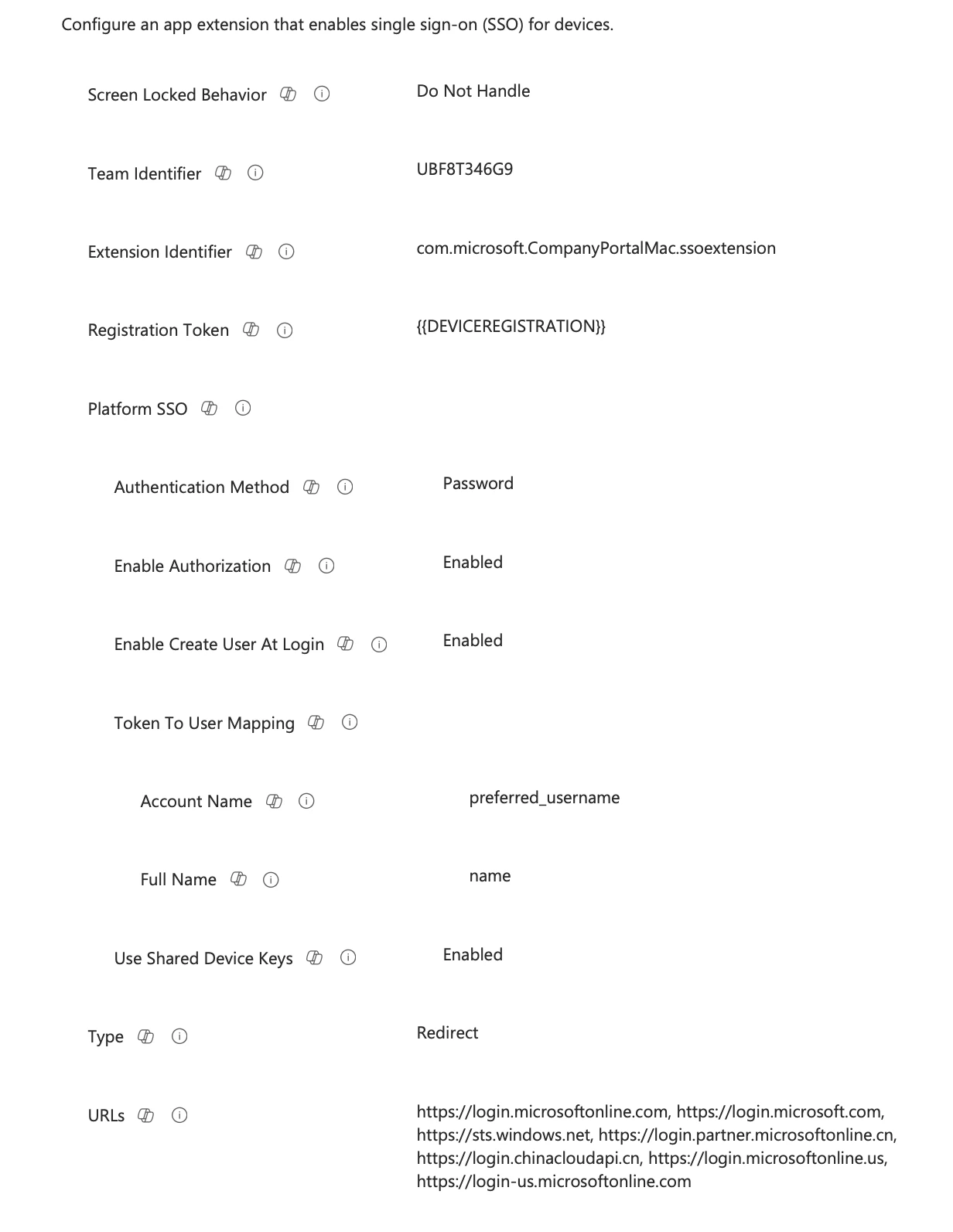
We are pushing out MSCP via the Jamf Mac Apps. We’re using “Password” as our authentication type. Setup with Entra. And we do not currently have any custom config, just out of the box setup.
Our machines are NOT Bound to AD, and we use local standard user accounts to start off with. then register and sync passwords.
I have 2 major issues that I would love to hear from the hivemind:
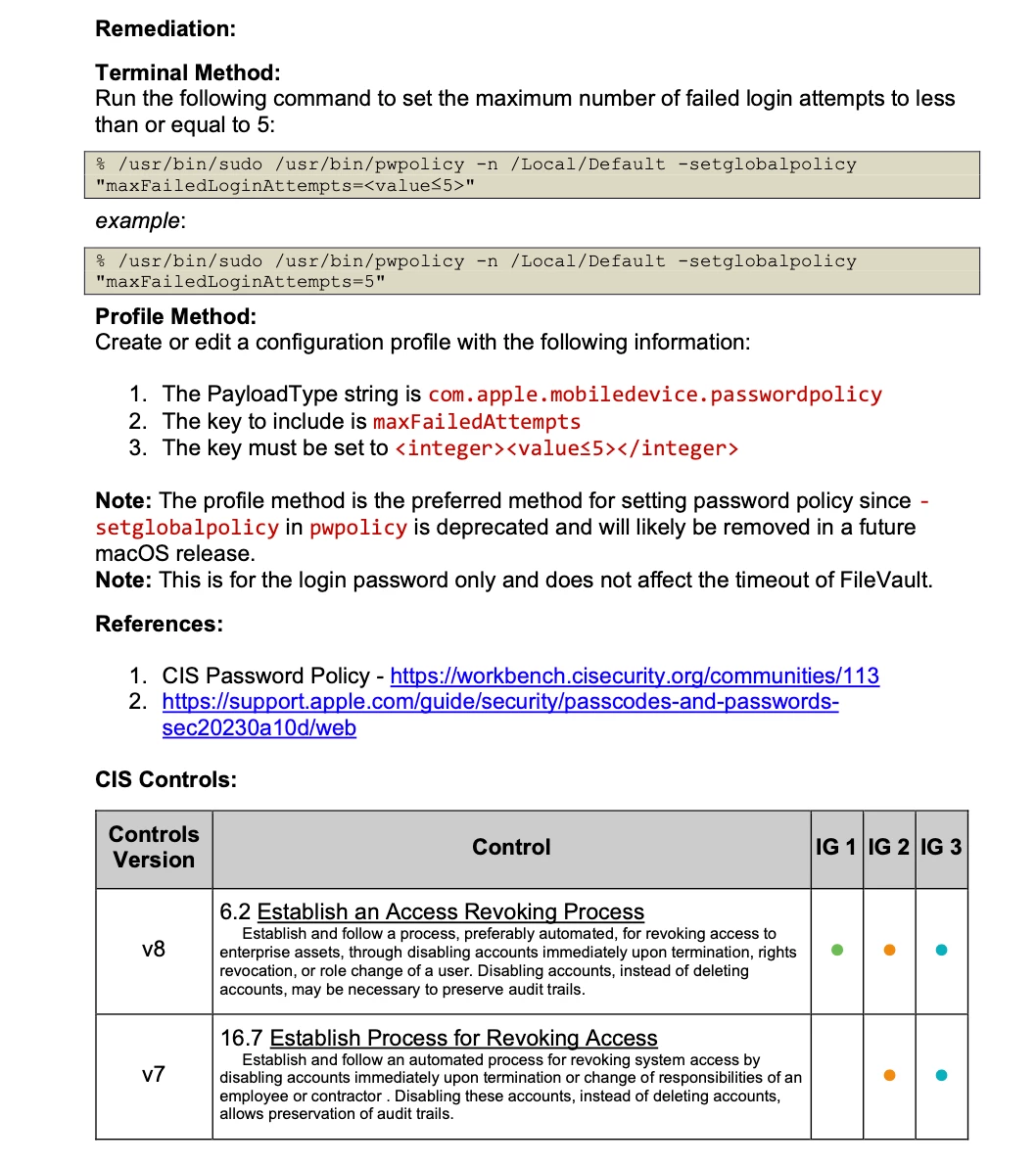
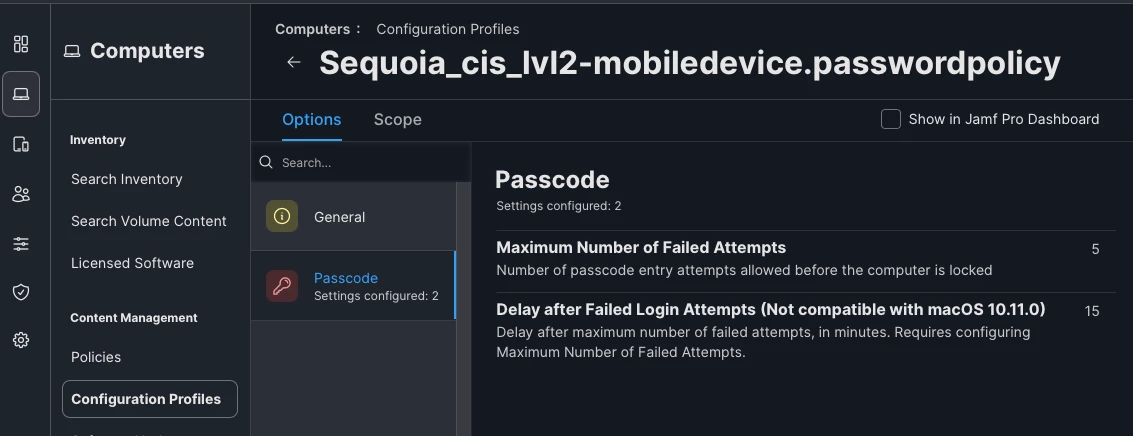
- We are seeing that we can put in many bad passwords at the login screen without any repurcussions. If the machine was compromised, what is stopping someone from brute forcing the correct password? Is there a way to set password attempts?
- When a user’s password changes they can obviously go re-authenticate and sync their password again, but what if a user just ignores this and never syncs their password? Meaning whatever their password WAS is what they are using to Log In and then use a different password for their AD Account info such as M365 apps. Is there anything that can “auto sync” the password? Is there anything that can “force” the user to stop what they’re doing and do the sync?
Excited to hear from yall! Thanks in advance!