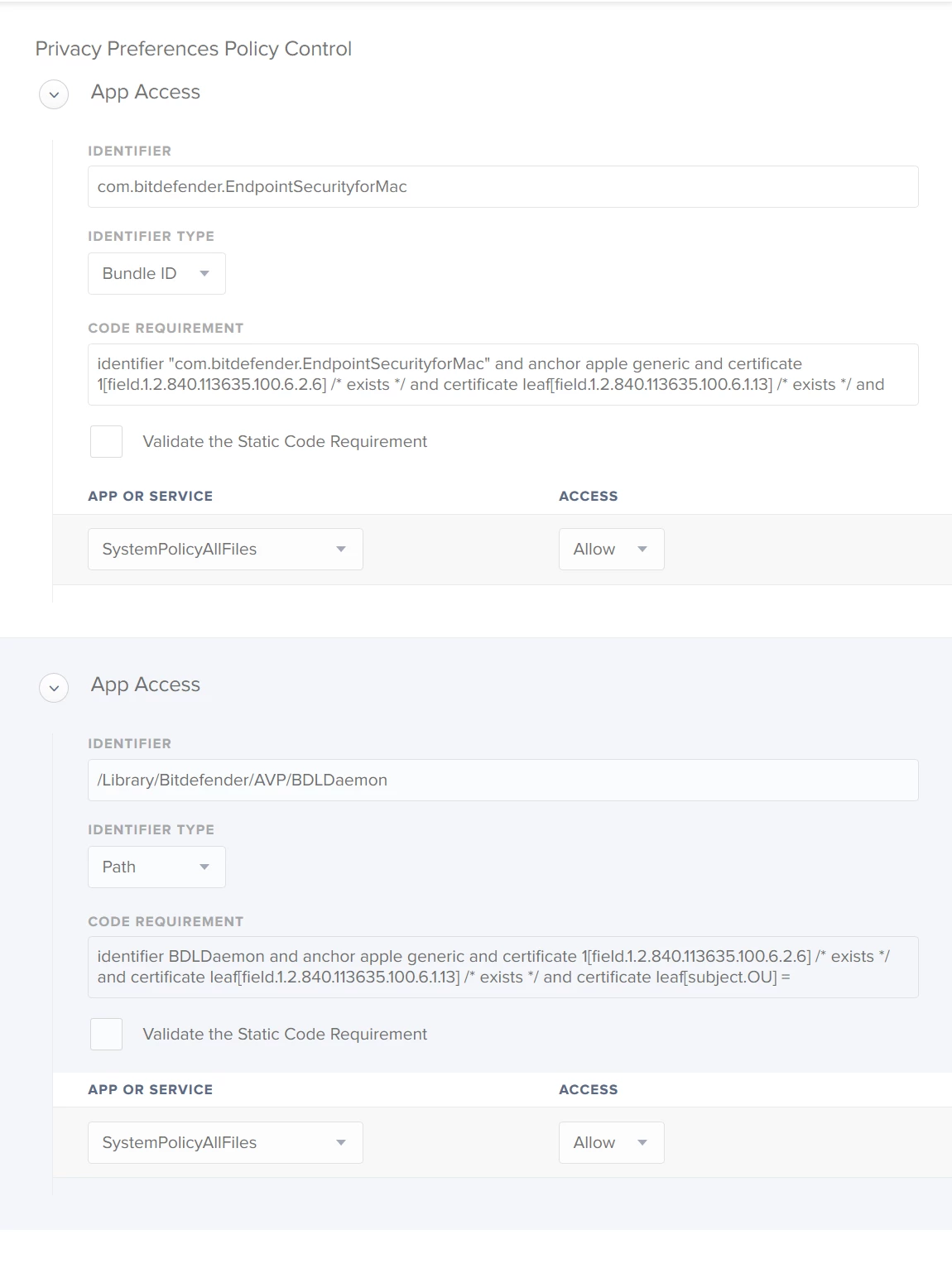
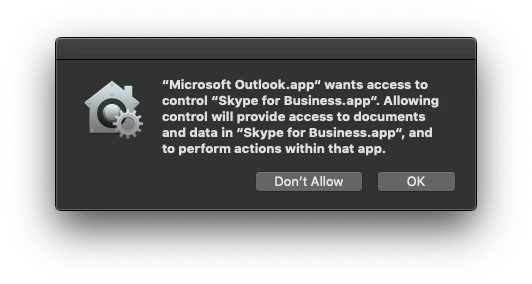
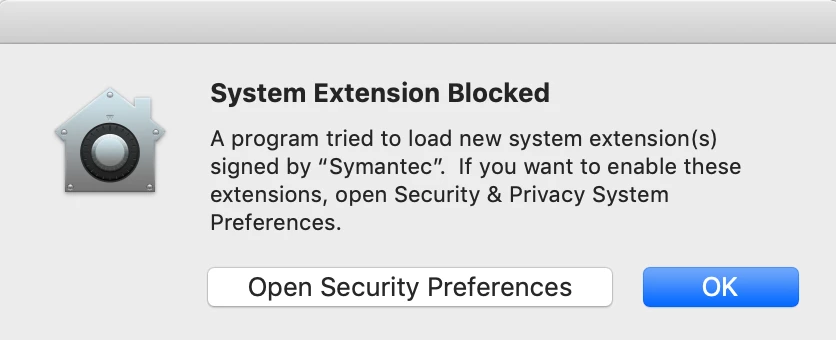
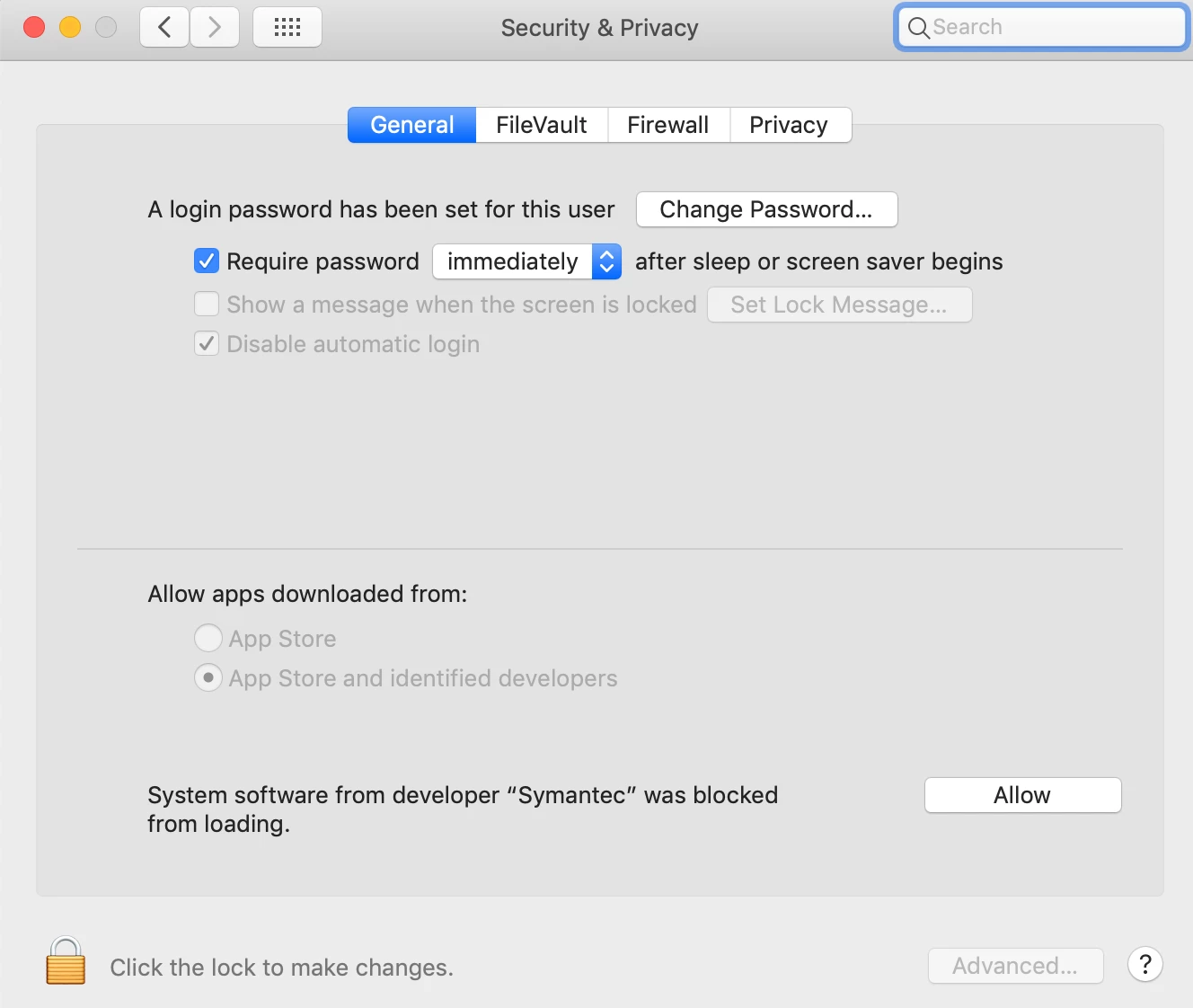
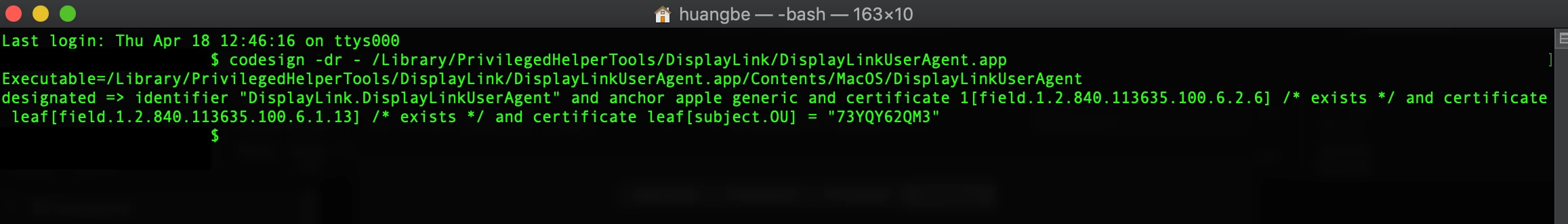
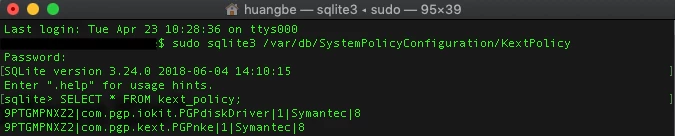
I'm starting to get my head around this PPPC joke....
It appears I am going to have to create a PPPC profile for almost every application that does anything... for example, Photoshop and After Effects....
So, have I missed something that means I only need to deploy one profile? or am I doomed to installed a PPPC profile for every Application I want my users to access?
TIA